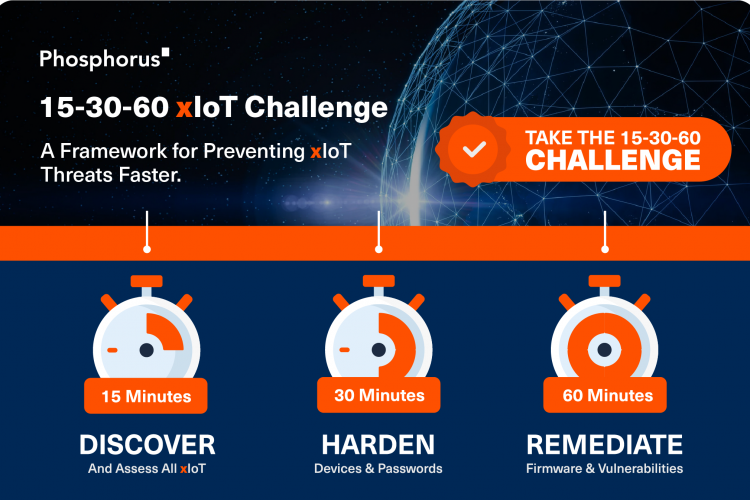
Amid active exploitation of CVE-2023-20198, Phosphorus is releasing a new platform capability that enables organizations to instantly assess and mitigate all at-risk Cisco IOS XE devices in their networks through its automated enterprise xIoT security platform.
NASHVILLE, Tenn., October 17, 2023 (GLOBE NEWSWIRE) – Phosphorus, the leading provider of unified security management and breach prevention for the xTended Internet of Things (xIoT), today announced new security features to help organizations prevent exploitation of the recently disclosed zero-day vulnerability (CVE-2023-20198) in Cisco’s IOS XE software. The new security update is being released today and is immediately available to existing Phosphorus customers, as well as new prospects in need of a mitigation and incident response plan.
Phosphorus’s new enhancement for its Unified xIoT Security Management & Breach Prevention Platform allows organizations to quickly discover and assess their IT, IoT, and OT networks for any/all Cisco IOS XE devices vulnerable to this actively exploited zero-day. The new capability provides remote mitigation at scale by allowing users to instantly disable the HTTP Server feature on all affected devices until a security patch becomes available, and represents the Cisco-recommended response action for the vulnerability. The Phosphorus Labs team is also working on new IOS XE-focused capabilities to identify devices that have already been compromised and to help customers recover and restore impacted operations.
“This is a critical zero-day vulnerability that could allow attackers to hijack devices and gain control of the affected systems in order to launch a variety of disruptive cyberattacks,” said Sonu Shankar, Chief Strategy Officer of Phosphorus. “It is absolutely imperative for all organizations to take immediate action on this vulnerability. This includes running a comprehensive security audit to determine how many devices within their environments are affected and taking the necessary mitigation actions as quickly as possible.”
CVE-2023-20198 is a privilege escalation vulnerability that affects Cisco’s IOS XE web user interface. It has the highest possible CVSS severity rating of 10 and allows a remote, unauthenticated attacker to gain control of the affected system with privilege level 15 access. The vulnerability affects physical and virtual devices running the IOS XE software, with the HTTP or HTTPS server feature turned on. This includes routers, switches, wireless controllers and access points, including several ruggedized industrial versions of these device types.
Facilitating Incident Response & Remediation Actions at Scale
Phosphorus empowers organizations by giving them direct control over every single Cyber-Physical System (CPS) in their wide-ranging xIoT deployments – including IoT, OT, IIoT, and IoMT devices. Through the platform’s Hardening and Remediation capabilities, organizations can update and rotate a device’s credentials, manage firmware, disable remote services, turn off unnecessary connectivity features, check for valid certificates, reboot the device, and more.
For organizations that have detected zero-day impacted xIoT technologies in their networks, specific device-level actions such as changing passwords, disabling services, managing configurations, and reducing connectivity will be critical for limiting the potential risks of these devices prior to security patches becoming available.
Phosphorus’s Unified xIoT Security Management & Breach Prevention Platform is currently deployed in Fortune 100, Fortune 500, and government networks. It is the industry’s only CPS Protection Platform covering the entire security and management lifecycle for xIoT devices. The company’s Intelligent Active Discovery (IAD) engine assesses xIoT assets up to 98% faster than traditional passive scanners. Its evidence-based risk assessment capability collects over 3X more data points from xIoT assets than other services – including current firmware version and CVEs. Phosphorus’s platform is able to automate the remediation of the most significant device vulnerabilities – including out-of-date or vulnerable firmware, default credentials, out-of-date device certificates, risky configurations, inaccurate asset inventory, etc.
For more information, visit www.phosphorus.io.
ABOUT PHOSPHORUS
Phosphorus Cybersecurity® is the leading xIoT security management and breach prevention platform for the xTended Internet of Things. Designed to secure the rapidly growing and often unmonitored world of Things across the enterprise xIoT landscape, our Unified xIoT Security Management Platform delivers attack surface management across every industry vertical, providing intelligent active discovery and risk assessment, hardening and remediation, and detection and response. It brings enterprise xIoT security to every cyber-physical system in your enterprise environment. With unrivaled xIoT Intelligent Active Discovery and risk assessment, Phosphorus automates the remediation of the most significant IoT, OT, IoMT, and IIoT device vulnerabilities – including unknown and inaccurate asset inventory, out-of-date firmware, default credentials, risky configurations, and out-of-date certificates. Follow Phosphorus on LinkedIn, Twitter, Threads, and YouTube, and learn more at www.phosphorus.io.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.