Streamlining Compliance with OMB Mandates
The Office of Management and Budget (OMB) has mandated federal agencies to maintain a detailed inventory of their Internet of Things (IoT) and Operational Technology (OT) assets. This directive aims to enhance the cybersecurity posture of federal infrastructures by ensuring comprehensive visibility, continuous monitoring, and proactive risk mitigation against cyber threats.
The mandate comes at a time when U.S. adversaries like China, Russia, and Iran continue to actively target xIoT assets within critical industries – including water treatment plants, electrical grids, oil and natural gas pipelines, and transportation systems – to gain a foothold inside networks and systems and launch significant disruptive attacks.
Phosphorus’ Cyber-Physical System (CPS) Protection Platform empowers Federal Agencies to meet – and exceed – OMB mandates for IoT/OT Cybersecurity with efficiency and precision.
Key Requirements from OMB Memo
The OMB FY24 Memo focuses on enhancing Federal Information Security and Privacy Management in alignment with the Federal Information Security Modernization Act of 2014 (FISMA). It emphasizes the adoption of zero-trust principles, measuring implementation progress, and improving security outcomes through data-driven approaches. The memo outlines requirements for agencies to prioritize automation, integrate Continuous Diagnostic and Mitigation (CDM) data into FISMA reporting, and improve security-privacy coordination.
It also details responsibilities for inventorying IoT devices, enhancing cybersecurity practices, and mandates close collaboration with the Cybersecurity and Infrastructure Security Agency (CISA) to ensure compliance and enhance federal cybersecurity posture.
The memo defines IoT devices in pages 5 and 6:
“NIST defines IoT devices as those that have at least one transducer (sensor or actuator) for interacting directly with the physical world and at least one network interface (e.g., Ethernet, WiFi, Bluetooth) for interfacing with the digital world. Many IoT devices constitute operational technology (OT), defined by NIST as “[p]rogrammable systems or devices that interact with the physical environment (or manage devices that interact with the physical environment). These systems/devices detect or cause a direct change through the monitoring and/or control of devices, processes, and events. Examples include industrial control systems, building management systems, fire control systems, and physical access control mechanisms.”
It then specifically mandates the following, in pages 6 and 7:
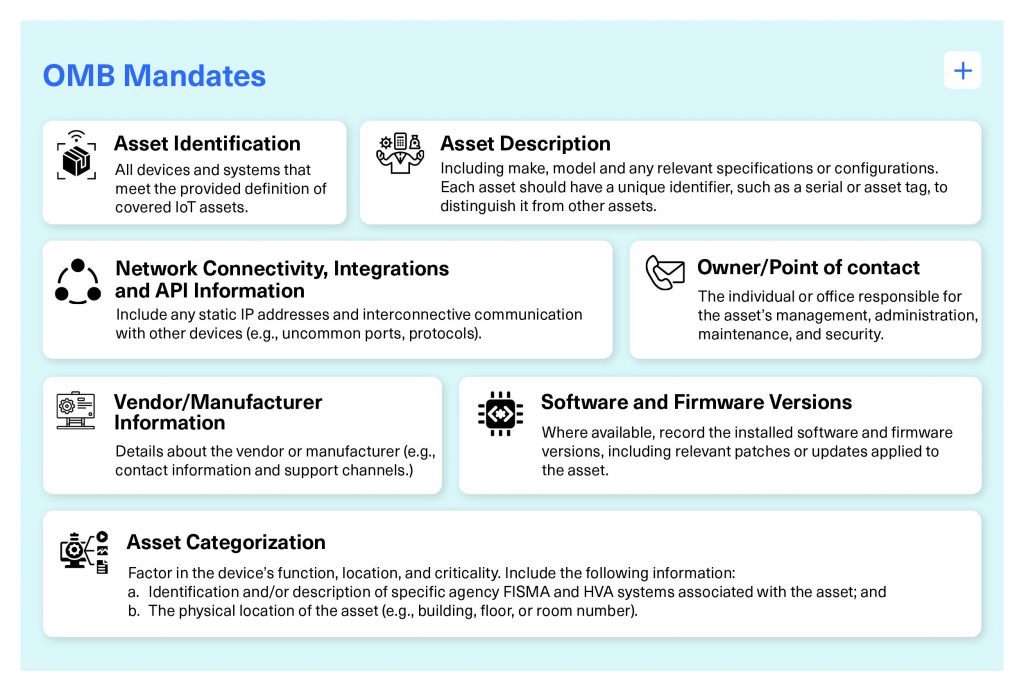
“To enhance the U.S. Government’s overall cybersecurity posture and to help ensure integrity of systems, agency CIOs shall work with asset owners and operators to establish an enterprise-wide inventory of their agency’s covered IoT assets by the end of FY 24. Inventories shall include the following information about all covered IoT assets, including OT:
- Asset Identification: All devices and systems that meet the provided definition of covered IoT assets.
- Asset Description: Including make, model and any relevant specifications or configurations. Each asset should have a unique identifier, such as a serial or asset tag, to distinguish it from other assets.
- Asset Categorization: Factor in the device’s function, location, and criticality. Include the following information:
- Identification and/or description of specific agency FISMA and HVA systems associated with the asset; and
- The physical location of the asset (e.g., building, floor, or room number).
- Owner/Point of contact: The individual or office responsible for the asset’s management, administration, maintenance, and security.
- Vendor/Manufacturer Information: Details about the vendor or manufacturer (e.g., contact information and support channels.)
- Software and Firmware Versions: Where available, record the installed software and firmware versions, including relevant patches or updates applied to the asset.
- Network Connectivity, Integrations and API Information: Include any static IP addresses and interconnective communication with other devices (e.g., uncommon ports, protocols).
- Security Controls: Describe alignment to requirements and controls, such as NIST SP 800-213, SP 800-82, SP 800-53, and other standards and protocols.”
The Challenges
The challenge of inventorying IoT devices for government agencies, as mandated by the memo, is substantial due to the vast and diverse nature of IoT ecosystems within federal operations. Agencies must identify and catalog a wide range of devices, many of which may not have been designed with enterprise management or security in mind. This task is complicated by the decentralized deployment of these devices, the wide-ranging variety of vendors, models, and protocols, and the need to integrate legacy systems with modern cybersecurity frameworks. Successfully inventorying these devices is critical for establishing a secure and manageable digital infrastructure.
This aligns with CISA and NIST efforts to enhance cybersecurity practices across federal agencies. CISA provides guidelines and resources for managing cybersecurity risks associated with IoT and OT devices, emphasizing the importance of comprehensive asset management. NIST, through its publications, outlines standards and frameworks for securing IoT technologies. Both agencies underscore the necessity of accurately inventorying IoT and OT devices as a foundational step towards implementing robust cybersecurity measures, ensuring that agencies can effectively mitigate risks and comply with federal cybersecurity mandates.
The Phosphorus Advantage
Phosphorus provides a comprehensive and state-of-the-art security platform and framework that adapts to the evolving cyber threat landscape so that federal agencies are not just compliant, but also equipped to increase cyber resiliency while proactively defending against and responding to new cybersecurity challenges.
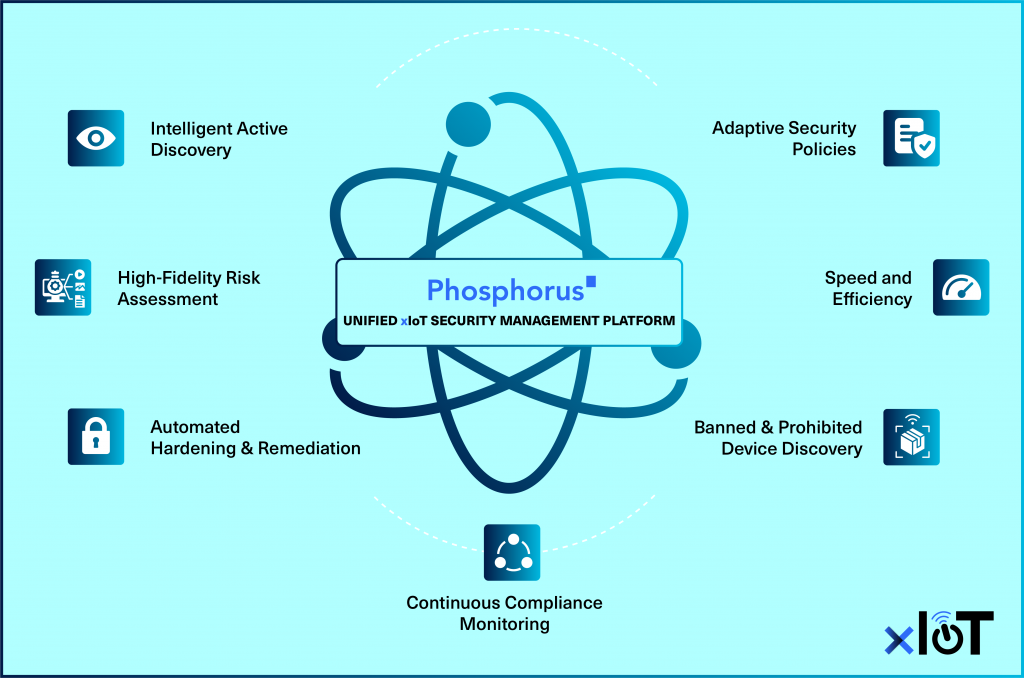
Intelligent Active Discovery: Phosphorus’ automated platform employs advanced scanning techniques to identify and catalog every connected device within the agency’s network, including over 500 vendors and one million device models. It is 98% faster than traditional passive legacy scanners and up to 95% more efficient (lighter) than legacy active scanners.
High-Fidelity Risk Assessment: Leveraging direct interaction with Cyber-Physical System assets, Phosphorus collects over 3X more high-fidelity device metadata from IoT/OT assets than any other service – including device posture, status of device credentials, current firmware version and CVEs, certificate status, risky configurations, device end-of-life status, banned devices, and more.
Automated Hardening & Remediation: Upon identifying risks, Phosphorus’ solution automates the remediation process, managing credentials, updating configurations and certificates, and applying patches without the need for manual intervention. This automated capability significantly reduces the window of opportunity for attackers.
Continuous Compliance Monitoring: The platform offers continuous monitoring and reporting features that ensure agencies remain compliant with federal cybersecurity standards over time. It automatically documents all actions taken, from discovery through remediation, providing a transparent and auditable trail that simplifies compliance verification.
Adaptive Security Policies: Recognizing the unique security needs of different federal agencies, Phosphorus allows for the customization of security policies and procedures. Agencies can tailor the platform’s settings to align with their specific operational environments, threat landscapes, and regulatory obligations, ensuring a more effective and targeted cybersecurity approach.
Speed and Efficiency: Our agentless, software-based, and automated platform significantly speeds up each step – from inventory to remediation – ensuring that federal agencies can quickly meet OMB requirements without compromising on cybersecurity.
Summary
Phosphorus’ Gartner-recognized Unified xIoT Security Management Platform specifically addresses the OMB’s directives for IoT and OT discovery and compliance. And, our agentless, software-based platform goes beyond discovery to provide in-depth device risk assessments, robust hardening and remediation, and ongoing operational management and monitoring – through its unique ability to directly communicate with all xIoT devices in their native languages.
Connect with us to get started
To learn how your network can be more secure and cost-effective without compromising on performance, connect with us here.
Author
John Vecchi
As Chief Marketing Officer, John brings more than 25 years of experience in high-tech marketing, strategy, product marketing, product management, sales and consulting. Most recently, John was Chief Marketing Officer at Anitian, ColorTokens, and Anonyome Labs.