xIoT Device Risk Advisories

EVERY DEVICE COUNTS
Securing HEALTHCARE MANUFACTURING RETAIL HOSPITALITY DATA CENTERS ENERGY UTILITIES OIL & GAS BANKING FINANCE organizations EVERY device at a time.

The UNKNOWN, UNMANAGED, UNMONITORED Problem
The xIoT attack surface is massive and growing. And any vulnerable device could be your weakest link.
Unknown
80% of organizations can't identify most of their IoT and OT devices.
Unmanaged
Average age of firmware is 7 years, 75% of devices deployed with default passwords.
Unmonitored
Your xIoT attack surface was secure yesterday? Doesn’t mean it’s secure today.
IN xIoT SECURITY
You are ONLY as secure as your Weakest Link
Whether in healthcare, manufacturing, hospitality, energy, retail, or banking, your environment has a broad mix of IoT and OT devices.
Focusing on one category of xIoT devices, while missing another, means you’re only as secure as the devices you missed.
This is why every xIoT device counts
Having vulnerable IoT and OT devices that are unknown and unmanaged leaves you at risk for:



TAKE THE 15-30-60 CHALLENGE*
Does Every Device Count in Your Organization?
*Estimated times to completion are based on typical network configuration.
Actual times may vary, depending on specific configurations and complexities of network environment.
Actual times may vary, depending on specific configurations and complexities of network environment.

Any device could be your weakest link. See for yourself.
Are these devices part of your xIoT attack surface? Can you FIND, FIX, and MONITOR every one?
[Hover over the icons below to see the vulnerabilities.]
Click on the icons below to see the vulnerabilities.
Enterprise Printers
- Extremely large attack surface because of ubiquity
- Ports/Protocols: Highly promiscuous use of Telnet, WiFi, etc.
- Priorities: Connectivity, availability
- Impact: Ideal targets for persistence, evasion, & data exfiltration
Enterprise Printers
Infusion Pumps
- Life-critical device
- Open ports/protocols: FTP, SSH, WiFi, Telnet
- Sensitive data stored in clear-text
- Priorities: Accuracy, Privacy
- Impact: Ransomware, Patient Harm
Infusion Pumps

Rugged Printers
- Default Password: Admin:1234
- End-of-Life since 2014
- Vulnerable to CVE-2021-22156
- Impact: DDOS, Malicious Script
Zebra ZM400 Label Printers
Security Cameras
- If you have 10,000 cameras, and a critical new firmware is released every month, how do you keep up? What about all your other devices?
Rate of Patching
Access Controllers
- Applications run on top of Linux by lack SDLC & basic security testing
- Critical CVEs: Production systems discovered with level 10 CVSS scores
- Priorities: Physical security, safety
- Impact: Remote, unauthenticated, and low-skill exploitation for full control
Physical Access Controllers
Industrial Gateways
- Priorities: Provides data exchange between industrial equipment
- Vulnerable: Old firmware, bad certificates, & limited security oversight
- Hygiene: Default, simple, & shared passwords are common
- Impact: Exploitation can go undetected for years, exposing other connected assets
Industrial Gateways
UPS Systems
- Default Passwords: rarely changed, easily found online
- Risks: Tied to sensitive IT assets
- Environments: Can be used for emergency backup power for physical infrastructure.
- Impact: Vulnerable to DDoS, use as remote attack vector, power disruption, destruction
UPS Systems
PDUs
- Priorities: Distribute power to IT hardware with remote connectivity
- Lifetime: Deployments can last years with almost no security intervention
- Status: Internet-accessible, vulnerable firmware, poor password management
- Impact: Unauthenticated remote takeover, destruction, delay
PDUs
Environmental Sensors
- Priorities: Critical for assessing and acting on environment-sensitive operations
- State: wireless and resource-constrained
- Vulnerable: Physical access, integrated wireless technologies
- Impact: Denial of service, Eavesdropping, Illegitimate use, and Indiscretion
Environmental Sensors
HVAC Controllers
- Most deployed with Default Passwords
- Old, unpatched firmware with critical CVEs
- Impact: Low-skill exploitation & ransomware, critical across supply chain
HVAC Controllers
PLCs
- Mostly no authentication
- IData stored in plain text
- Many deployed with key switch in program or remote mode
- Critical CVEs
- Impact: DDOS, Modification, Injection
PLCs
Robotics
- Default Password: Blank
- Remote Access via open web portal/FTP
- Priorities: Precision, Safety
- Impact: Loss of product and productivity, harm
Industrial Robot Arms

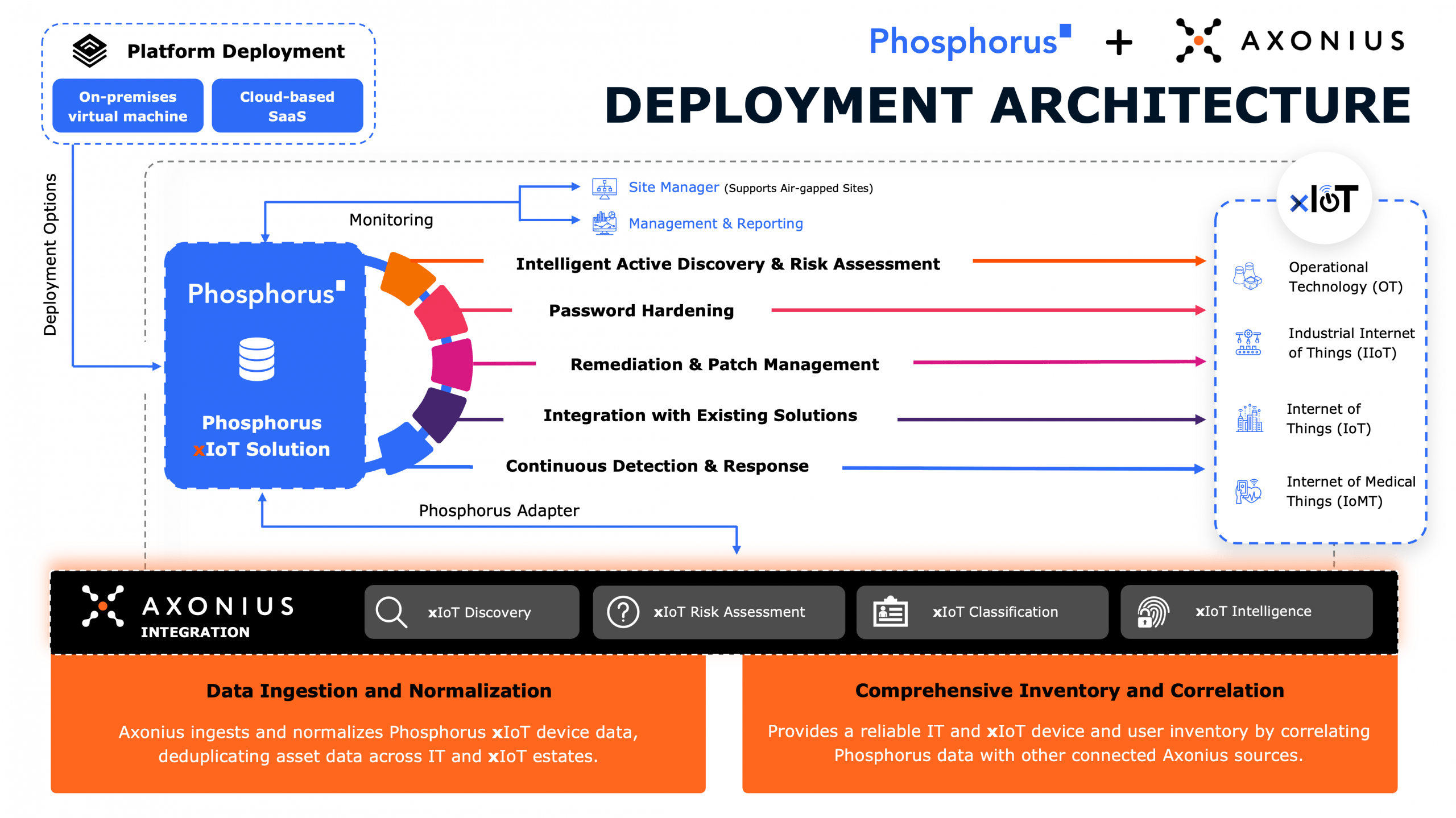
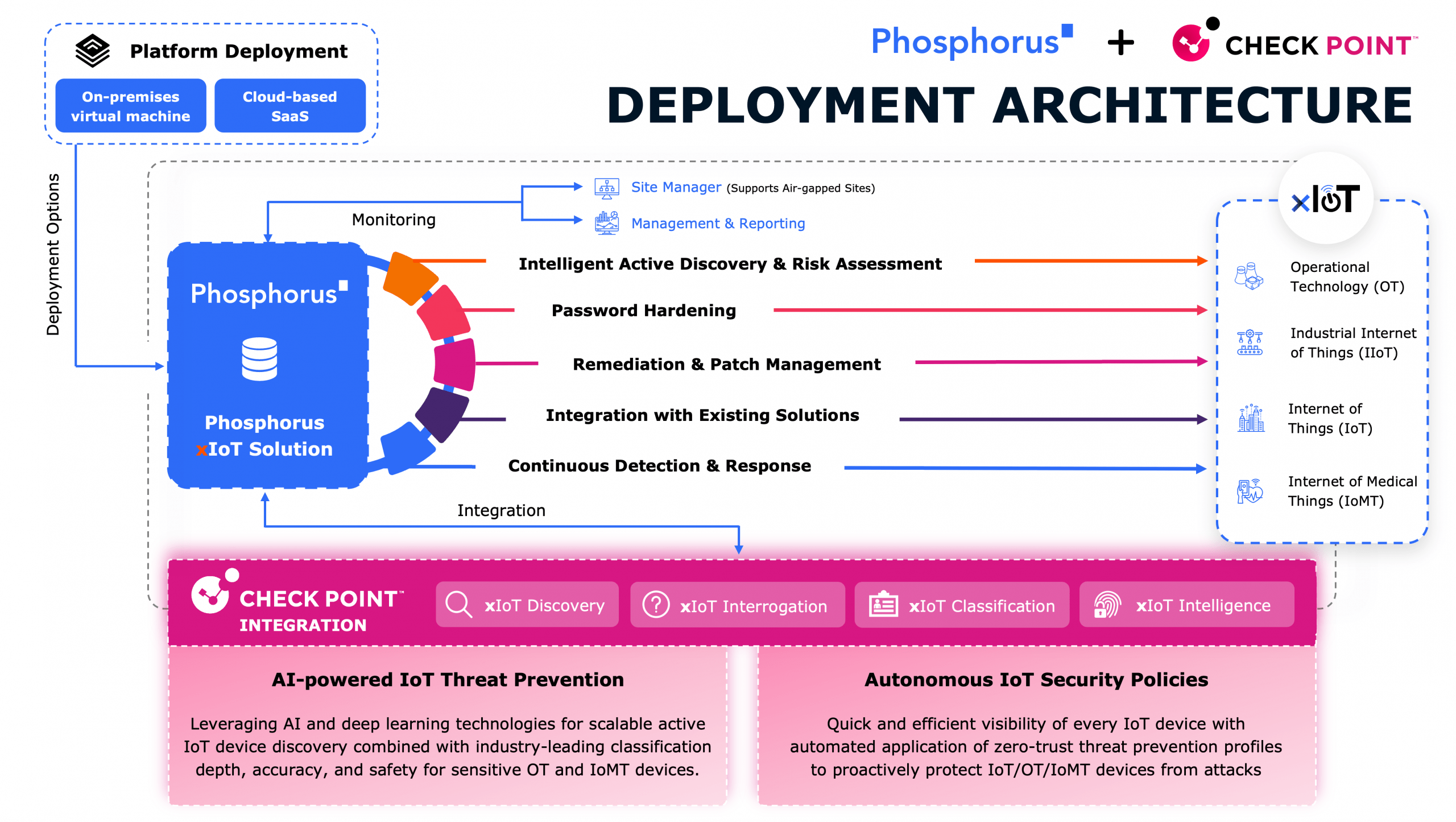
The Solution
You need to FIND, FIX, MONITOR, and MANAGE every device
Do it without agents, hardware, or hassles
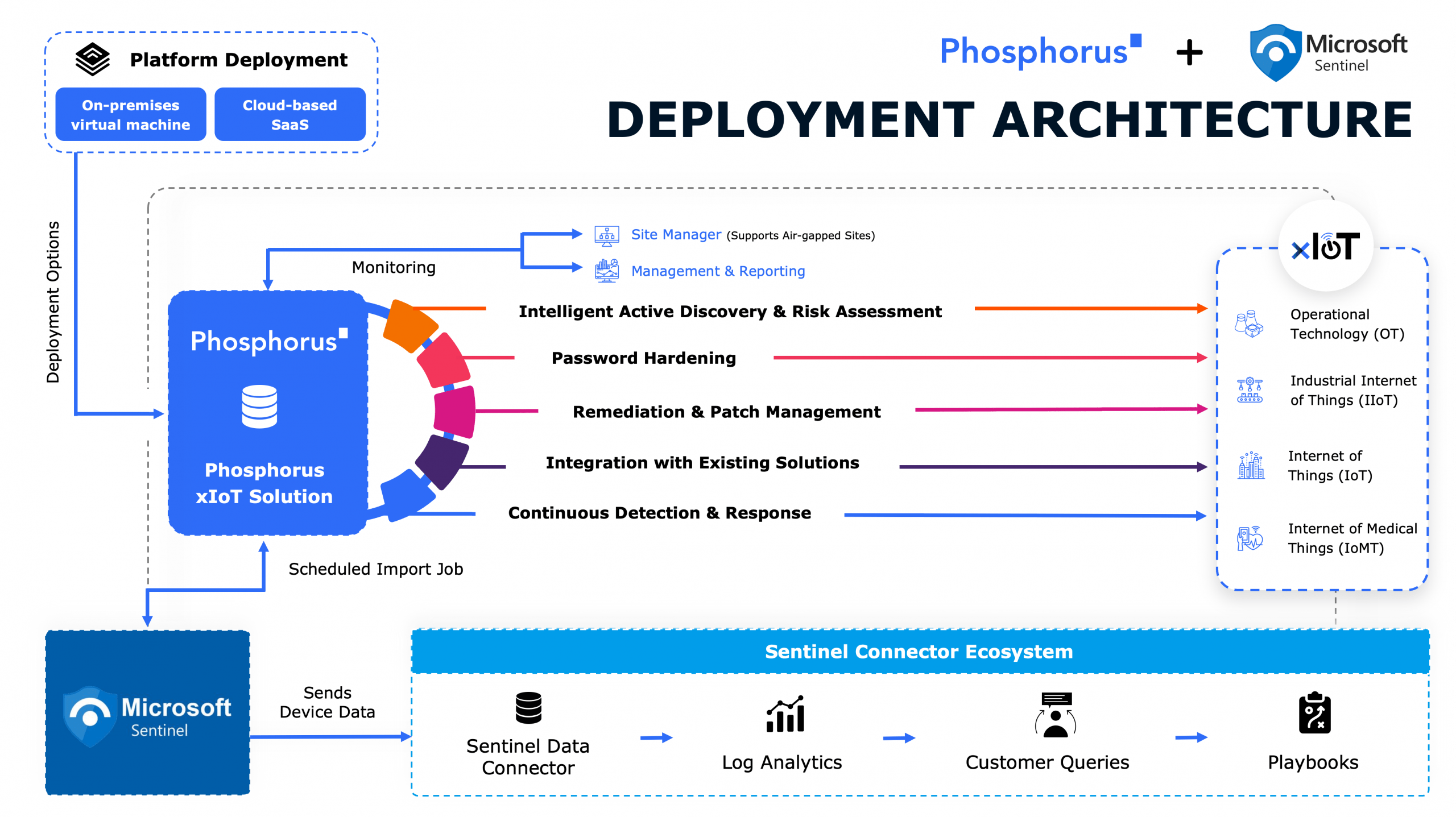
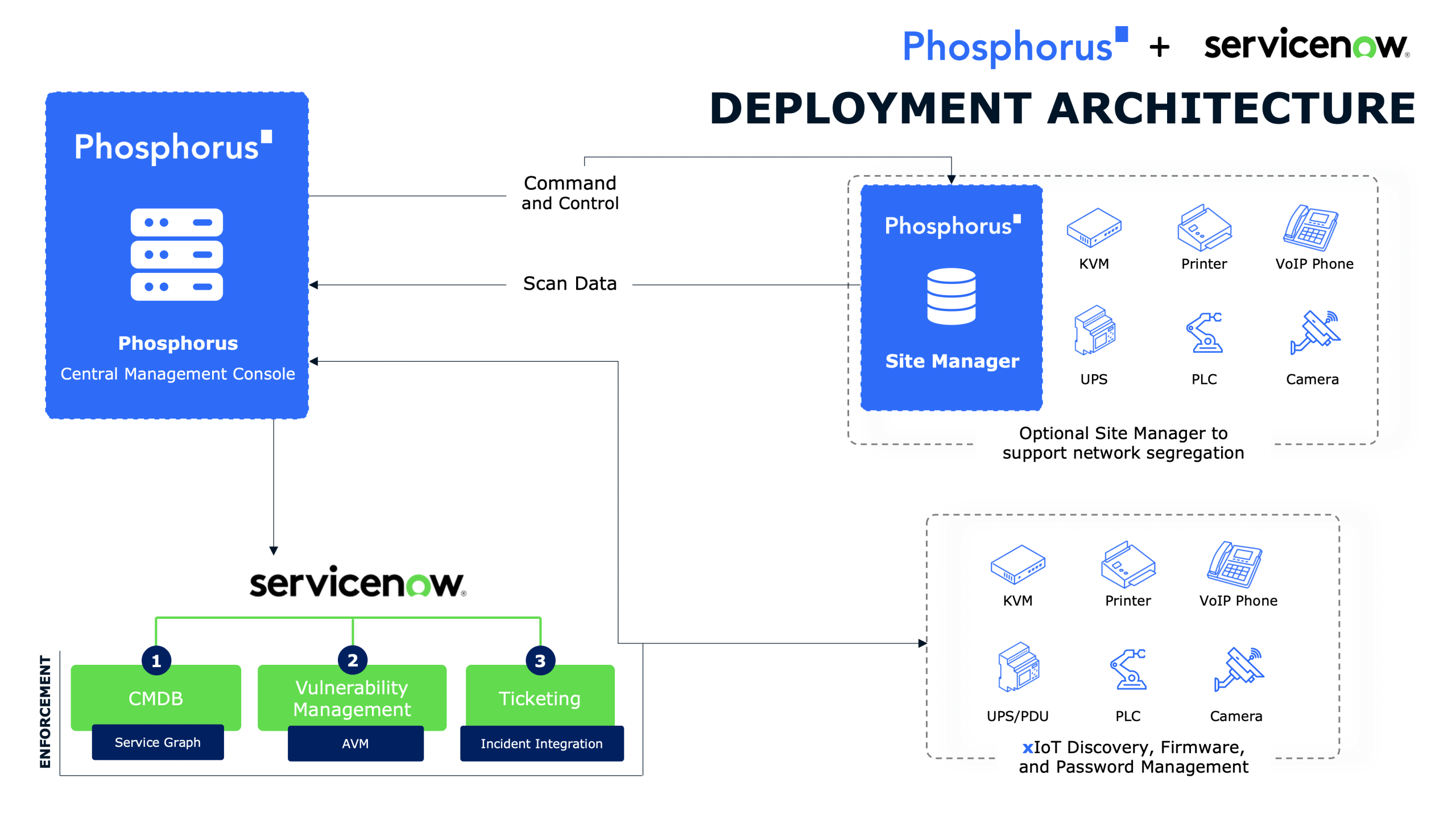
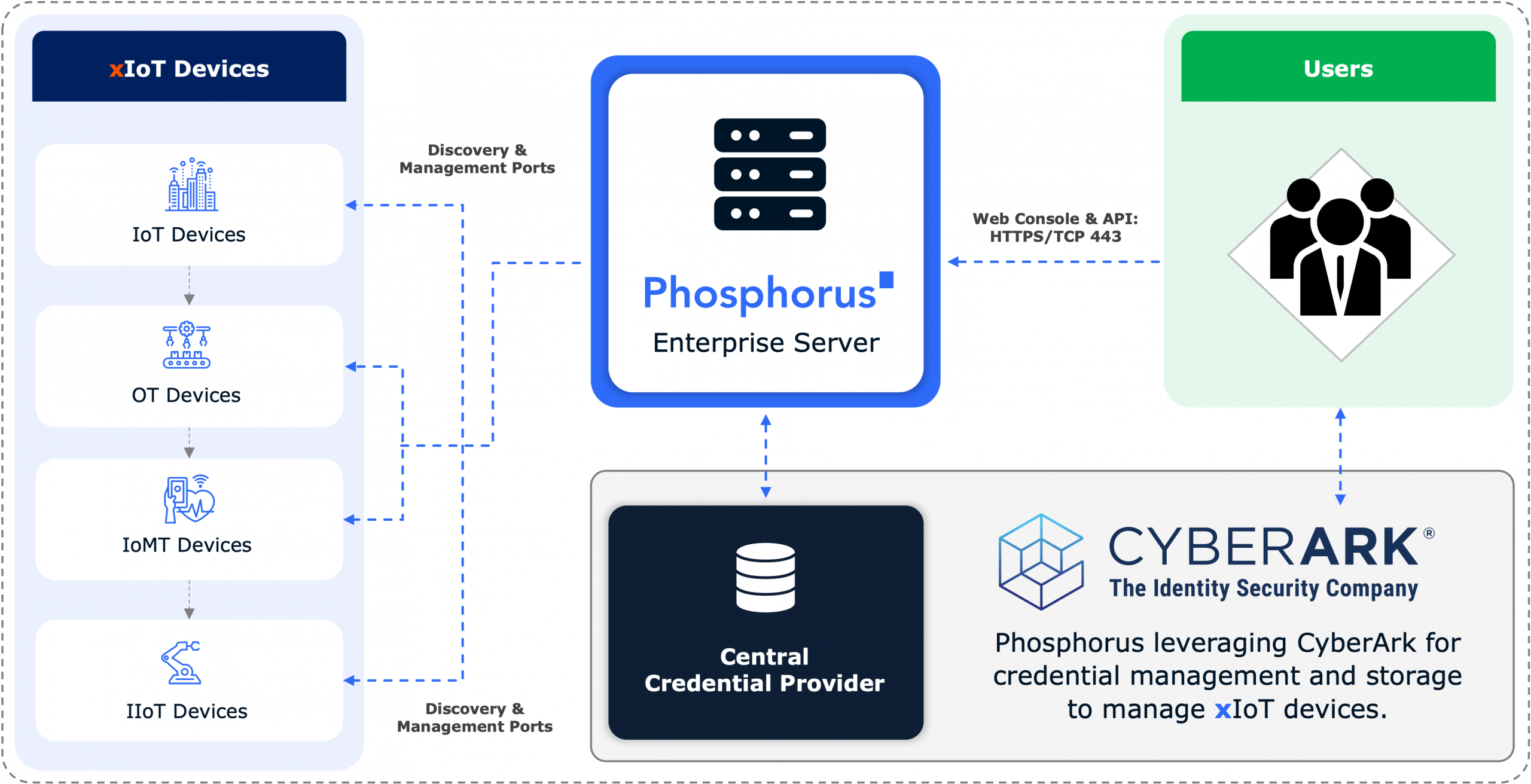
The Phosphorus Unified xIoT Security Management Platform is the industry’s only CPS Protection Platform proactively covering the entire security and management lifecycle for xIoT.
Through its unique ability to directly communicate with over one million device models in their native languages, the platform enables organizations to safely discover, harden, remediate, and manage EVERY IoT, OT, IIoT, and IoMT device — including the most sensitive mission-critical and life-critical assets.
FIND
Safely, accurately, and actively discover, classify, and assess every IoT, OT, IIoT, and IoMT device.
FIX
Automatically remediate xIoT device vulnerabilities, including passwords, firmware, and certificates, with One-Click.
MONITOR
Continuously monitor all xIoT devices for device drift and other misconfigurations with active alerts and responses.
With Phosphorus every device counts in…
Sign up now to start receiving monthly Phosphorus Labs xIoT Device Risk Advisories for common IoT, OT, and IoMT CPS devices – and learn how to remediate their vulnerabilities.
What's included?
- Receive a direct-to-inbox Phosphorus Labs xIoT Device Risk Advisory every month.
- Advisories cover xIoT devices from label printers to HVAC controllers and everything in between, including IoT, OT, and IoMT devices.
- Get high-fidelity device information with each Advisory — including common vulnerabilities, critical CVEs, and impact of a potential breach.
What happens next?
Get your FREE xIoT Device Risk Advisory
The information you provide may be used to send you updates from Phosphorus Cybersecurity. You may opt-out at any time. By submitting this form, you are agreeing to our privacy policy.