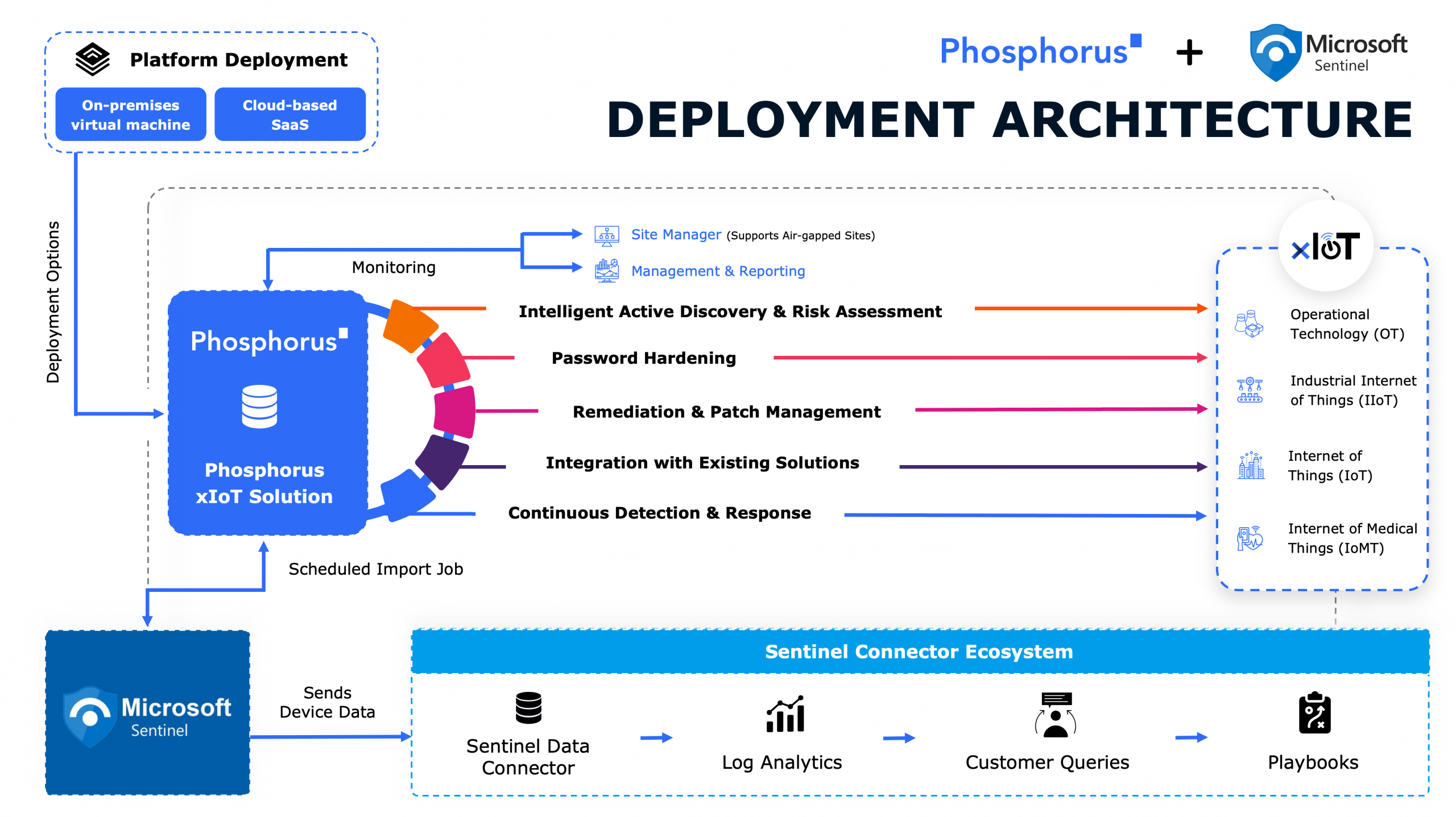
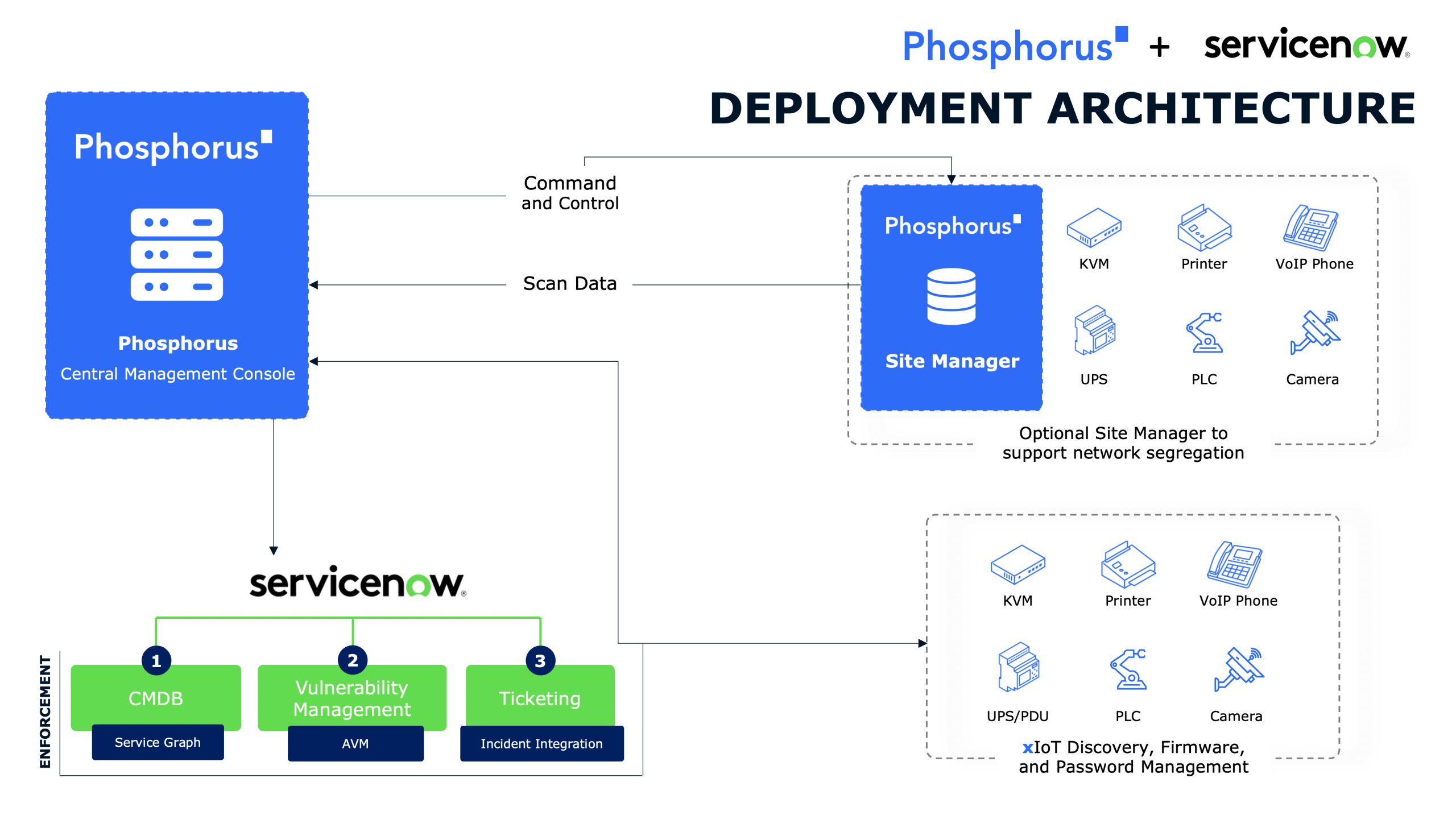
In this episode, we’re diving deep into the world of Operational Technology (OT) and IoT security, exploring the critical challenges and evolving threat landscape that are impacting sectors from manufacturing to critical infrastructure and healthcare. With insights from Patrick Gillespie, OT practice lead at GuidePoint Security, we’ll discuss the convergence of IT and OT systems, the risks introduced by COVID-19, and the advanced solutions from providers like Phosphorus that are combatting these threats. Patrick also sheds light on his personal journey from military service to a cybersecurity career, and the essential steps organizations should take to bolster their OT security, from embracing cyber hygiene to implementing robust security programs. Join us as we uncover the pressing issues facing IoT security today and how innovations drive a safer, more secure operational environment.
Subscribe on Spotify, Apple Podcasts, Amazon Music, and wherever you get your podcasts.
Transcript
John Vecchi:
Well, hello everybody. I’m John Vecchi, your host here on the IoT Security Podcast. For those of you listeners who have been tuning into this podcast for the past year, you might notice that my co-host, Brian Contos, wasn’t introduced in the introduction. That’s because Brian, like myself, we both travel a lot. We go out and speak a lot. Brian’s been incredibly busy.
He was the co-founder of this podcast with me and helped us make this very successful. But Brian is out of time to do this podcast with me, so you’re stuck with me as the primary host. So, keep tuning in and it’s the same podcast. We’re going to have amazing guests like the one we have today. And with that in mind, I would love to introduce today’s guest, Patrick Gillespie. Patrick is the OT Practice Lead at GuidePoint Security.
He’s got over 19 years of experience as an information technology and cybersecurity leader. He has a master’s degree in CIS security from Boston University. He’s got about every certification available, OCSP, CISSP, CCNA, CCSA, pen test. You name it, he’s got it all. Patrick is also an Operation Enduring Freedom veteran who served in the Army. Thanks for your service, Patrick. As an intelligence analyst, he also serves on the board of advisors for the 501(c)(3) non-profit, Boots to Books.
And that organization helps veterans attain competitive education and employment opportunities, and get hired at some of our nation’s top technology companies. Patrick has mentored dozens of veterans to enter the cybersecurity field. And is also on the board of advisors of that non-profit, Whole Cyber Human Initiative. Wow, what a background, Patrick. Please welcome Patrick Gillespie. Patrick, it’s great to have you, man.
Patrick Gillespie:
Thanks, John. Glad to be here.
John Vecchi:
So, wow. We’re definitely going to talk OT. As you know, you may have heard on the podcast, we cover all types of verticals. But we really do oftentimes dive into the industrial control system, the operational technology, that kind of manufacturing, industrial control system topic. And obviously, that’s definitely your wheelhouse.
So to start, Patrick, can you just kind of talk a little bit about your background, how you ended up at GuidePoint, how you even ended up in OT? I mean, it is such a very specific type of domain in security. It’s always interesting to hear how experts like yourself ended up on the OT side. Could you tell us a little bit about that?
Patrick Gillespie:
Yeah. OT is very niche within cybersecurity. Really, my start was in the Army. I was Intel Analyst, as you mentioned, top secret clearance, all that fun stuff. And then, which kind of helped me learn to portray the enemy really. With cybersecurity, the better we can portray the enemy, the better then we can build our defenses and our defensible architecture.
After I got out of the Army, I got into IT. So actually, for 11 years I was in manufacturing. We didn’t call it OT back then. But I ended up architecting a lot of what we’d call OT architecture today, defensible architecture, for automated facilities that built either parts for trains or put the trains together. So, I was in rail car manufacturing for a long time. During that time, is when I went to Boston University and got that master’s in cybersecurity.
It was more of an interest. And my mentor at the time, lead me in that direction. And then once I graduated from that, I got my first pen testing job. So, ended up doing that for seven years, which led me to GuidePoint. So, I came on board as a manager of the threat and attack simulation team. And then as we started hiring OT professionals, I raised my hand and says, “Hey, I was in manufacturing. I can manage these guys too.” And then we just kept getting more and more OT, IoT work. And now, I am the OT Practice Lead at GuidePoint Security.
John Vecchi:
Wow, what a journey. What a journey. I mean, as you said, right, you started on the OT side. And as we all know when we talk OT and ICS stuff, that the IT and the OT convergence is absolutely happening and happened, and which is always an interesting thing, right? You’ve got operators on that side. It’s a whole different kind of environment. Obviously, we call it xIoT, Patrick. It’s the carpeted area IoT stuff.
But also some of the IoT stuff that might actually end up on the industrial side, like there’s cameras. And then you’ve got the OT kind of industrial, the PLCs, the HMIs, the industrial gateways, RTUs, and sensors, and robotics, and SCADA systems, right? And those things are converging. How is that, I mean, for you coming from the IT side now just seriously deep in the OT side, how would you describe that convergence that we talk so much about, right?
Patrick Gillespie:
Yeah. The convergence probably been happening the last 10 or 15 years just for to make better business decisions really. The more information you can get from a machine, from the OT network, the better data you can have, real-time data, and of course, make better decisions, save money, increase safety. All these great things, right, that come with IT OT convergence. And then also secure remote access.
So, when I started building networks, we called them just the plant network, again, we didn’t call them OT back then, were physically separate. Their own switches, their own fiber, their own ethernet. And typically had no Internet connection unless we had to do temporary remote access. Over the last 10 years or so, things have just started getting connected.
A lot more IoT devices going out on the plant floor, and carpeted side, like you mentioned. And then COVID happened. So, now you have to work remotely, global pandemic. So, now your automation engineers from Germany, or Austria, or Canada can no longer travel to the US, or vice versa. And plus, your employees working from home need to weigh in. So, best thing to do is to hook up OT to IT, and let’s go in through the IT VPN, have direct access essentially into these typically flat OT networks.
So, yeah. I think COVID really drove that convergence, which has driven a lot of new threats and new vulnerabilities, new exploits, everything. Increased business risk dramatically for everybody, and especially in critical infrastructure.
John Vecchi:
Yeah, there’s no question, right? And having you say that was reminding me, we used to we had the S4 conference, which is the big ICS conference. And I was chatting with a CISO who works for a major, major utility in the South. And he laughed at the statement of, “Air gapping and isolated.” And he just said, “Trust me, I’ve been in this business my whole life. There isn’t such a thing anymore.” And we kind of know you’d like to pretend there is. And often when I speak, I talk about air gapping isolation.
And I just say, “Well, Stuxnet. I mean, they thought it did work out too well for them. They thought that was air gap.” And so, right, it’s kind of interesting that everything’s kind of connected, right? I mean, given that you’re in these companies, you’re consulting with them, you’re doing pen testing, is that can be officially validate that air gapping is, there’s not much of it anymore?
Patrick Gillespie:
Yeah, the term air gap can mean different things depending on who you’re talking to.
John Vecchi:
Yeah.
Patrick Gillespie:
So, they may say air gapped, and that means, oh, IT and OT can’t talk to each other directly without going through maybe an industrial DMZ. But a lot of times they’ll block outbound access from OT, but then IT can still connect, and all these things. But even if the Internet connections you know you have and the connections or the conduits to the OT environment, there are still asset owners on the plant side or the OT side that are not security people, right? They’re trying to do their job. They’re trying to be more efficient, increase quality of the product, and keep safety going. OT is all about safety and availability. Because an exploit or an accident in OT could cause physical harm or death, right?
John Vecchi:
Yes.
Patrick Gillespie:
Because all about safety.
John Vecchi:
Yeah.
Patrick Gillespie:
But so, I guess, I don’t know if it’s not a war story, but when I was in rail car manufacturing, for example. We had dozens of rail car manufacturing facilities and rail car repair facilities across the US and Canada. So, I would go and do an IT project, for example, maybe replacing an analog phone system with voice over IP. I’d go out on the plant floor just to kind of check out the plant, or maybe there was a phone out in the warehouse or something that I need to replace.
And I would literally find cable modems that either the plant manager or the controls engineers would order their own ISP from the local provider, install it, and plug it straight into the PLC rack. So now, they can work from home. They can get their remote users or their vendors to remote in, save costs on travel. So, they’re saving the business money. They’re being more efficient. But they don’t want to deal with IT.
So, they brought in their own Internet lines. And again, so now you’ve got IT security who has no idea of that IP address that that’s connected at all. They have no idea on asset inventory for those devices or that PLC rack. And now you’ve opened up your entire OT network, typically a flat network, especially back then, to externally for essentially the public, the whole world to see.
John Vecchi:
Yeah. So Patrick, I mean, right, it’s like the OT teams kind of for the first time understanding what shadow IT is, right? And it’s happening now on the OT side. So, look, tell us a little bit about the pen test. You do pen testing, right? When you walk into these organizations, obviously you’re going to test them. Talk to us about that.
And specifically, about the operational technology, the IoT, the OT, the industrial control systems, those specific type of systems, which lets face it, oftentimes are difficult to find and see when you’re just coming in and doing a typical kind of standard pen test, right? So, how do you work with that? And how do you help organizations gain visibility of that side separate from say the traditional IT kind workstations and all those things on that side?
Patrick Gillespie:
Yeah. So, a lot of clients will ask for an OT pen test. And pen test from the IT side, especially in some industries that require it like PCI or banking, pen test is typically more for a more mature organization or a mature architecture. So, when a client asks for an OT pen test, we’ll typically state that a lot of exploits, even port scanning can be dangerous to OT assets. So, we talk about the dangers, the things that typically happen in OT that don’t happen in IT.
Just the sensitivity of the devices, a lot of proprietary services, proprietary software, all those things. So, one of the things we look at when a client wants an OT pen test or maybe once they’re mature enough for an OT pen test is do you have an incident response plan in place, right? So, if we do reboot something or break something, do you have a plan on to get the operations back running, right? Or, if we cause an issue with a safety device, that we can get that back on quickly.
John Vecchi:
Yep.
Patrick Gillespie:
So, that’s one thing that we look at. Another thing is do you have a defensible architecture? So, if you don’t have good segmentation. If you have a flat network and you’re running clear text protocols, an OT pen test is going to tell you 100 things that I can tell you right now.
John Vecchi:
Yep.
Patrick Gillespie:
That you have devices that do not require authentication. You have devices that are sending clear text protocols that have no data integrity whatsoever. That we can modify data on the wire. We can see clear text passwords, if there’s even passwords on there to begin with.
John Vecchi:
Yep.
Patrick Gillespie:
And so, a lot of things that don’t go with like the CIA triad, right, confidentiality and integrity. Those are the big ones on IT. So, and then we also ask, “Do you have any visibility in monitoring? Are there any systems in OT that’s watching the traffic, that’s monitoring the assets, and doing vulnerability management?” Because if we come in and do a pen test, again, you have nothing in place. There’s not a lot to test except for maybe some Windows NT boxes, Windows XP, PLCs that you can connect directly to.
So, if you don’t have these systems to test against to make sure that they’re working properly for visibility, and monitoring, and vulnerability management, that a lot of times, again, an OT pen test is not going to provide a lot of value. There are other services that we can provide that will bring much more value in your journey of an OT security program. So, I would definitely recommend OT pen testing be taken very seriously. Yes, we do them a lot. But again, we definitely recommend you be a bit more mature in your OT security program first.
John Vecchi:
Yeah. And there’s so many things there in that description that I want to dive into because it’s just so rich. I mean, right away, like you said, Patrick, the sensitivity of these devices, right? So obviously, this has been, I call it, if you think of it from the now, next, never, right, and that never bucket, right? This is never, never, ever, don’t touch it, don’t do anything.
And obviously, I think historically, the idea of quote, unquote, “scanning these devices, discovering these devices,” the traditional way to do that, obviously as we know, doesn’t work. I call it waterboarding. It basically tips the device over and waterboards it. But they don’t like to be talked to like that. You can’t scan thousands of ports of protocols or ask it if it’s running SMB. It just falls over, right?
So, what are your thoughts on that? From my perspective, I think that it’s changing a little. A, there are technologies now that can actually intelligently, actively pull to discover in a safe kind of way. So, on one hand, I’m seeing a crack in that reluctance. But what are you seeing relative to active, which is a very bad, horrible term? Do you see any change in position on that, given some technologies now that could do that in a safe way?
Patrick Gillespie:
Yeah, a lot of that goes back to wording.
John Vecchi:
Yeah.
Patrick Gillespie:
If you tell an asset owner of an OT environment that, “Hey, we want to do active scanning,” a lot of times they’re going to have nightmares of a time when a IT security guy ran a vulnerability scanner in their network.
John Vecchi:
Yep.
Patrick Gillespie:
And I have a lot of times environments and people like myself learn the wrong way to do it before you realize, “Oh, these devices don’t like this,” right?
John Vecchi:
Yeah.
Patrick Gillespie:
So, for pen testers, they’re all familiar with Kali Linux, right, comes with a set of tools. But before that, when I got into security, Kali Linux didn’t exist. It was BackTrack Linux. So, when I started going back to school for my master’s in security, I started testing my local networks at the rail car manufacturing facility I was at. So, I started testing IT. Well, the OT was a separate physical network. But of course, I had a desktop with dual NIC. So, I plugged the OT network into my dual NIC IT computer, and set up a BackTrack Linux server, and put OpenVAS on it.
John Vecchi:
Oh, boy. No.
Patrick Gillespie:
So, I was like, “Well, it worked well in IT. Nobody cried.” So, then I decided to scan OT with OpenVAS just to see what was out there. And the devices did not respond well.
John Vecchi:
Yeah.
Patrick Gillespie:
And actually there was a printer, I don’t remember the brand name, but when I scanned it, we got a frantic call to the help desk. A lady, I think it was in purchasing out in the plant at one of the paint facilities for the rail car, called and says, “Her printer wouldn’t stop printing papers and they all said are you dead?” She thought somebody was attacking her personally. And so, I had to go apologize profusely.
But it was because of OpenVAS scan on that network that not only caused the weird printing, but caused some outage, denial of service essentially for those devices. So, that was a lesson learned for me. And then once convergence started happening, especially during COVID, a lot of people started doing full-blown enterprise vulnerability scanners, in-map port scanners. And yeah, like you mentioned earlier, those devices do not behave well against that kind of traffic.
John Vecchi:
Right. Right. Yeah, yeah, yeah. It’s so, so true. So, what do you do? Are you leveraging any technology? Are you looking at leveraging technology that’s available that can actually, I like to call it pulling a little bit more than just the active scan. It’s intelligently having levels of pulling, especially for the sensitive devices.
So, we can just quickly determine that A, it’s a sensitive device. I know what you are. I’m going to stop talking to you now. And I’m going to move on to a next tier, which could take in a few more protocols, ports, so forth, right? I mean, is that viable? Are you looking at those kinds of technologies in the way, whether you’re doing pen testing or more other services you’re providing?
Patrick Gillespie:
Yeah, of course. We work with multiple technology vendors. Technology for OT and IoT security has come a long way in the last year. Every year, I mean, it gets better. But compared to 20 years ago when I got in, there was, again, open source stuff that would blow everything up. But, so yes, we use tools like Phosphorus in doing IoT assessments. We use them for OT pen test.
We use them for primarily asset discovery. Because a lot of times an CISO or an IT director that also handles security will inherit OT security, or once they converge, they’re now responsible for the security, even though they do not own the assets. So, what we do is we use these tools like Phosphorus to do those intelligent queries. So, when we’re scanning, a lot of times we can’t wait for downtime to do the asset discovery, right, because a lot of manufacturing facilities are 24/7.
So, we’re able to use tools like Phosphorus to come in, get it on the switch layer, and to determine, look at the traffic or maybe span ports, mirror ports to get that traffic. But we’re able to use those tools to discover, “Oh, this is an Allen-Bradley PLC. This is a Siemens PLC.” So, if it connects, once it discovers that through broadcast traffic or some other fingerprinting method, then it’s able to communicate to that specific device like Allen-Bradley PLC, Rockwell PLC, on port 44818, for example, and talk to it just like that RSLogix would.
So, it’s not an in-map port scanner sending 65,000 requests to a single PLC that can’t support that, that many connections. It’s one request. It talks to that box on that one port, just like the software would. Then it’s able to get the firmware information, model, serial number, all this stuff we need for an asset inventory. It’s able to pull that through that intelligent query. I hate to use active scanning because again, it brings up nightmares for people.
John Vecchi:
Yeah.
Patrick Gillespie:
But yes, it’s definitely intelligent scanning. Or, intelligent querying, I guess, is maybe the best way to put it.
John Vecchi:
Yep, exactly. Yeah. Well, that’s interesting. I mean, I think it’s coming back around. I think hopefully we’re making some progress there. But let’s talk a little bit about the threat landscape. It’s fascinating, right? I mean, like I often say, the last six months specifically, if you just look at the activity of someone like CISA, right? Putting out all the notifications of vulnerabilities, and all the ICS, and PLCs, and all the things, right, it’s a dizzying number that has been kind of increasing.
And then that couples with some of the threats we’re seeing, right? I mean, oftentimes, there’s the pipe dreams from Shurnavite, and the Industroyer2s, and these kinds of things. You see Christopher Wray and everyone sitting before the House talking about the fact that our critical infrastructure is already compromised by nation-states, right. You’ve got the Pennsylvania water facility attack and things like this. And now recently, the Fuxnet by Blackjack, right?
Interesting because I want to talk a little bit about as you find and discover these devices on the OT side and even some of the IoT stuff that happens to be potentially critical in OT environments, like maybe a ruggedized printer, or a printer, or a camera, the Fuxnet targeted, right, that gateway, that IP-connected gateway, that’s kind of that bridge between say the Modbus and all these kinds of protocols on the OT side, right?
And they attacked that gateway primarily leveraging default passwords, right? Something just the most basic kind of hygiene that’s just wide open, right? So, it’s Internet connected. It’s got default credentials. It’s kind of wide open, right? Can you talk a little bit about what you’re seeing, what you’re finding, the state of those devices? And how you tend to think about it matching up to all those threat activities, and threat actors, and all this stuff going on? Do you bring those two together when you’re talking to your customers?
Patrick Gillespie:
Yeah. So, the threats are kind of twofold. So, there’s more threats. So pre-COVID, there was typically probably one major attack on critical infrastructure every year. You already mentioned Stuxnet, Colonial Pipeline. There seemed to be, like I said, one major event per year. Now it seems like it’s every month, every week.
John Vecchi:
Yep.
Patrick Gillespie:
It’s overwhelming. And you mentioned CISA putting out guidance. You got the White House putting out regular guidance on cybersecurity. I mean, yesterday they put more out.
John Vecchi:
Just yesterday. That’s right, yep.
Patrick Gillespie:
There’s Executive orders. It’s overwhelming for security teams, especially that don’t understand how manufacturing works, how the power side of an electric company works, how OT devices transmit and generate electricity, how they make sure water systems, or the chemical makeup of a PEEL of a prescription drug, right?
So, the IT people don’t understand that part of the process. They’re not engineers from that perspective. They’re not scientists. So, it can be very overwhelming when you have so many new threats, so many new vulnerabilities. And then also the second factor of that is just the sheer number of IoT devices that get connected every day.
John Vecchi:
Yes.
Patrick Gillespie:
So, when we do an IoT assessment or OT assessment, part of that asset discovery is what devices are talking to other devices and which ones are trying to go to the Internet? So, when you put an IoT device on the network, if it has hardware from China, a lot of times we will see outbound connections to China. We’ll see these, which will allow a Telnet session back in or an SSH session back into your network doing a reverse connection out. It goes out of your network. You may just allow port 443 encrypted outbound.
John Vecchi:
Yep.
Patrick Gillespie:
Well, if it could get out on 443, connect back to a server in China, reverse shell back in, now they’re in your network.
John Vecchi:
Yep.
Patrick Gillespie:
We have a lot of clients that have Chinese made machines in their plant environment, and they allow these vendors to connect into their network using a team viewer or some other remote access that is part of their service maintenance agreement.
John Vecchi:
Yes.
Patrick Gillespie:
They have to allow them to be able to have support and to keep the machines running. The Chinese vendors have remote access.
John Vecchi:
Yes.
Patrick Gillespie:
And if you don’t have good segmentation, microsegmentation, you’re allowing them to access not only that machine, if it’s running Windows, or Linux, or some operating system, they can then laterally move to other devices in your network and then steal proprietary information from other vendors and from your own manufacturing process essentially. So yes, when we’re doing these assessments, we’re seeing a lot of devices that are connecting to countries that are very surprising to the IT users or the IT security users.
John Vecchi:
Yeah. And in fact, that’s interesting. I mean, a lot of times when I go talk, I do a demonstration of hacking a Hikvision Chinese camera. Obviously, a lot of this equipment is banned here in the country as a threat to our national security. But in many cases, organizations don’t know if they have it, right, or how many, where it is. But it’s funny you mentioned Kali Linux. That demonstration of hacking, I use Kali Linux and just an exploit to go compromise the camera.
And I show how you can not only take command and control of it and upload anything, hacker tools, password crackers, ransomware, but actually xFill, right? xFill down and data out on a camera, which is basically, like I say, you see a camera, I see a Linux server. A lot of these devices are kind of like that. It’s really interesting, especially kind of that some of the manufacturers and the types. And I talk a lot about, again, the fundamental kind of hygiene that’s missing on these devices.
You mentioned some of the difficulty. I mean, you’ve got manufacturers, third parties, who are coming into these devices to manage them and they need to have access. But we find a lot of these devices just in a terrible state, like we say, 70, 75% of these devices are deployed with the default credentials. If they can take credentials, ports and protocols are open. They may have Telnet open or some other type of Internet-connected protocol that’s open that doesn’t need to be, right?
Obviously, we know the firmware on these devices are seven plus years old, unpatched, and terribly vulnerable. These are the kinds of things that nation-state hackers, or ransomware gangs, whatever it might be, it seems to me those are the things that they will go for pretty quickly as opposed to trying to get through a bunch of other layers of sophisticated security. Do you think that on the OT side that is something more and more they’re understanding from a risk perspective?
Patrick Gillespie:
Yeah, they’re understanding it because especially manufacturing gets hit every year with ransomware pretty hard.
John Vecchi:
Yeah.
Patrick Gillespie:
It typically spreads from IT to OT. So, we’re seeing, again, a lot of Windows 98, Windows NT boxes still on these machines that there’s no EDR on them typically. There’s no detection that, “Hey, ransomware is starting to encrypt files,” or PLC programs that are on maybe an engineering workstation running Windows 98. When I left the rail car manufacturing business in 2016, our primary system for testing the brakes on a rail car before we put it on the rail to go to the customer was a system running Windows 98.
So, they would still come to us when issues happened. But the software vendor had went out of business a long time before that. So, they just kept it going, right. We just supported it the best we could using floppy disk of Windows 98 as we could help them. And sometimes they just had the shared devices once one finally died. But you’re talking operating systems and firmware that are decades old that’s running our critical infrastructure. Not only that, like you said, if some even had authentication, a lot of times vendors will put in hard-coded passwords into the firmware to allow them, again, the ease of remote access.
That way if a user locked the account out or change the password and forgot what it was and can’t get into the system, they call support. Support’s able to remote in through that one of those reverse shell connections. And then use a hard-coded password that only the vendors or the manufacturer’s supposed to know, but eventually gets leaked, right? And then attackers are able to use these hard-coded credentials or no credentials to access these old operating systems or old cameras, like you mentioned.
John Vecchi:
Yeah, yeah. It’s just the challenge is it’s really amazing. You can really understand why all of the agencies, quite frankly, whether it’s NSA, CIA, FBI, are all raising that alarm of the vulnerability of our critical infrastructure. And again, that’s why we call them cyber-physical systems, right? The attacks can be physical in nature. These devices are controlling some type of physics or physical element. And bad things can happen, obviously, if you want to attack for that purpose.
And I think some of the things you’re talking about that just make that so challenging for some of these operators and organizations that are running this OT and ICS stuff, it’s really deep. I mean, you could just go… And I’m sure you’re seeing it every day. So, tell us, I mean, since you’ve been the OT Lead at GuidePoint, any kind of from the trenches, is there horror stories from that? Or, just anything that you’ve experienced that would be insightful for our listeners in your current position?
Patrick Gillespie:
Yeah, I mean, from mistakes I’ve made that I’ve already shared on this podcast. Yeah, other stories are just seeing devices, like you said. You already mentioned Hikvision.
John Vecchi:
Yeah.
Patrick Gillespie:
That the cameras get placed onto maybe an OT network or its own security VLAN. Some people think air gap is just putting them on their own VLAN. However, there’s no access control list at layer three to prevent that connection from going to maybe an IT device or to other OT devices that have those connections back to China. We met with a client, it’s been a couple months, but they had set up remote access for all their vendors using multifactor. They had secure remote access.
But they could not get the ones from China to follow the policy. So, they’re still using TeamViewer without multifactor authentication coming into this network. And they had no segmentation. So, essentially there have been cases, and I haven’t seen this personally, but cases where a vendor is connected to a manufacturing floor network that’s flat, and then they’re able to steal that data or proprietary information.
And then the client gets sued because they did not segment and secure that vendor’s proprietary information from other vendors. So, that is something we’ve seen. And then just the sheer number of, it’s tough to follow regulation as it is, but like you mentioned, there’s several government agencies putting out cybersecurity, either governance, or compliance, or guidance. You even have the FDA, Food and Drug Administration, in the past year-and-a-half or two years put out regulation on IoMT devices.
John Vecchi:
Yeah.
Patrick Gillespie:
Any for manufacturers that are building a new IoMT device, so think a new pacemaker, a new tool maybe to test bone structure, whatever it is, has to have a cybersecurity program. So, having the ability to do remote access, the ability to do vulnerability management, the ability to do remediation is coming from the FDA.
John Vecchi:
Yeah.
Patrick Gillespie:
And then you also have Department of Homeland Security through CISA putting out guidance. And for these IT security teams, they’re putting out fires. They’re trying to keep up-to-date on the IT devices. And now you throw in devices that have 10-year-old, 20-year-old, 30-year-old firmware operating systems, and they’re struggling to keep up.
John Vecchi:
There’s no question. And even you mentioned kind of healthcare and the IoMT site. I mean, some people don’t think about it often, but healthcare organizations have OT, right? I mean, they’ve got robotics and industrial stuff. They’ve got OT devices. It’s just mix. And of course, they think of an IoMT device similar as an operator will think of a PLC.
It’s also very sensitive, life critical. I guess the point there is, right, you don’t necessarily always have to be in what you would just go to as a manufacturing maybe industrial control environment to find OT, correct? It can be in many different types of industry segments. Are you finding that?
Patrick Gillespie:
Yeah, it’s definitely all the critical infrastructure industry. So, the one we probably deal the least with is probably finance.
John Vecchi:
You hadn’t?
Patrick Gillespie:
So, typically banking. So, it’s more traditional IT. I mean, yes, finance and banking is a critical industry. However, we don’t see as much. And then healthcare, the frameworks around that are compliances, HIPAA related, confidentiality of patient data essentially. But yes, there are hospitals that use these medical IoT devices, IoMT devices. Like you said, they use robotics during surgery.
So, now you have these devices working on human bodies or inside a human body. There’s now sleep apnea devices. There’s pacemakers that are regulating your sleep, your heart. Yeah, there’s so much that are inside people that have to communicate because when these devices have an issue of malfunction or a patient is starting to have anomalies, essentially.
John Vecchi:
All right.
Patrick Gillespie:
Something going on with their body. They need to communicate that to their care team to be able to do that. Well, is that traffic encrypted? Are they using clear text protocol? So, when we pen test these IoMT devices, we still see that data going over clear text protocols or near field communication. There’s just a lot of basic hygiene that does not get, or has not been implemented in the last 10 or 15 years for all these new IoT devices.
And the government’s usually slow to respond. So, attackers typically figure out the holes. And then government responds over the next few years to try to keep up with all the new attacks. But there’s new zero days. There’s new, even on things that are updated, that a software company still exists. They could put out a new firmware version today and there’d be a new remote code exploit in there, RCE exploit.
John Vecchi:
Correct.
Patrick Gillespie:
So, even with the overwhelming compliance, the overwhelming sheer number of IoT devices, and vulnerabilities, and updates, you could still be introducing new threats or increasing risk to your environment even with a firmware update.
John Vecchi:
Yeah, it’s so true. It’s just it’s fascinating. I mean, Patrick, we could talk for hours on this and just dive into it. You are on the front lines. You are just seeing this every day. And we talked about just the challenges, the threats, the state of these devices, the difficulty to even find them and see them, and they’re all Internet connected, and just all of these things. And it is just quite a set of challenges to really secure this stuff.
It’s why we’re all focused on this and in this industry. But as we kind of wrap up, Patrick, given all that you’re doing, any parting thoughts to our listeners who might be in the OT side trying to manage this, trying to deal with this convergence, trying to kind of think through a lot of the things we touched on today that are challenges? Any advice from your perspective, even the most basic kind of things that you feel is very important for everyone to think about and know?
Patrick Gillespie:
Yes. A lot of it goes back to basic cyber hygiene, right, whether it’s IT, or OT, or IoT, or XIoT, right? So, a environment, whether it’s IT or OT, an asset, a system will never be 100% secure. So, you’re never going to hit that end state of, “Oh, I’m secure now. I can go to bed.” Right?
John Vecchi:
Yeah.
Patrick Gillespie:
There’s always going to be risk. There’s always going to be threats. There’s always going to be threat actors. You mentioned some earlier. You got Volt Typhoon the last few months. And like I said, a lot of it started with Stuxnet. But that was truly an air gap system through USB devices. But there’s always a way in, right, even if it’s a machine that’s not on the network whatsoever, a USB stick coming in with malware could cause havoc, right, cause downtime, cause safety issues.
So, the one thing I would recommend is to start somewhere. If you don’t have an OT security program, you have no idea what assets you have out there, just pick a place and start somewhere. Pick a framework, like mid-cybersecurity framework. Do one control at a time. Because the secure direction you’re moving in is better than doing nothing, right? And you’re not always going to make the right choices. You may not pick the right vendor the first time, or the right tool, or the right partner to help you.
But start somewhere and don’t be afraid to ask for help. That’s where we come in as at GuidePoint Security. We’re able to work with great technology like Phosphorus to help ease that burden. So, if we have a client with 200,000 cameras globally, then we’re able to use Phosphorus to identify them and patch them much quicker than having to go to every one dealing with local authentication at every device. And we’re able to save our clients a lot of time and a lot of money for just coming and asking for help.
John Vecchi:
Yeah. And that’s a great example. If you get low-hanging fruit like a camera, again, we’re talking OT and industrial control systems that you forget cameras everywhere. And oftentimes, that’s your weakest link, right? They’re basically a bunch of very powerful computers with IP addresses, right? And so, that’s certainly great advice to think about it.
And great, GuidePoint doing amazing work. And so, Patrick, OT Lead there at GuidePoint. We’re so happy you could join us. I appreciate that so, so much. And before we say goodbye here, Patrick, are you talking anywhere? How can our listeners find you? They may want to follow you and find you, and read what you’re saying, and maybe go see you places. How can they find you?
Patrick Gillespie:
Yeah, LinkedIn. Yeah, definitely connect with me on LinkedIn. You can send messages there. We also have, GuidePoint has a lot of conferences called GPSEC. So, they’re all over the country. So, I spoke at Boston GPSEC recently, was in Omaha, was in Denver. So, we have those typically every month. I think the next one is in actually Chicago this week. I think it’s tomorrow.
But yeah, look for your local GPSEC. I’ve also spoken at events in different regions like Cleveland. I was in Cleveland a few months ago speaking. But yeah, follow me on LinkedIn because I share a lot of GuidePoint marketing materials and things related to OT and IoT. And then also speaking engagements, I’ll usually post on LinkedIn as well.
John Vecchi:
Wonderful. Well, everybody follow Patrick. Catch him. It’s going to be worth it. Fantastic discussion, Patrick. Thanks so much for joining us today. And remember, everybody, the IoT Security Podcast is brought to you by Phosphorus, the leading provider of unified, proactive security and remediation for the extended Internet of Things. Again, thank you, Patrick Gillespie, for being our guest today. And until we meet again, I’m John Vecchi. And we’ll see you next time on Phosphorus Radio.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.