Do you know every IoT device on your network?
Most organizations today unknowingly leave themselves vulnerable to attack. The source of this threat: connected devices. As the number of devices connecting to the network grows, so does the threat they pose to network security. However, CIOs and CISOs greatly underestimate the number of IoT devices in their organization. By how much? A lot. Why? Auditors aren’t informing them––they don’t even know themselves.
Most CISOs we speak to think that roughly 1 percent of their network is made up of IoT, but in actuality it’s more like 20 percent or higher. In fact, IBM X-Force recently estimated that devices make up 43 percent of the access points on the average organization’s network.
To make matters worse, this number is constantly increasing, oftentimes with devices being deployed as shadow IoT unbeknownst to the CIO. A CIO recently told us that his company’s physical security team put in 20,000 cameras that are full stack Linux, connected directly to the network, and didn’t think to give him a head’s up. Thus, those rogue devices were all unprotected.
So, how can a network be secured when hundreds, if not thousands, of access points are unknown? In short, it can’t. You have to have an accurate picture of all network access points to ensure each and every device is secured.
Device discovery
With the rapid rate of device proliferation, and the ease with which different departments can deploy shadow IoT, it’s imperative to have a clear understanding of how many and which devices have access to your network.
Device inventory is step one in basic security hygiene and by all accounts might be the most important piece of the puzzle. If you are conducting patching and access management properly on all known devices, but are unaware of a large swath of devices connecting to the network, you are still vulnerable to attack.
However, device discovery can be harder than you’d think. NBAD products require expensive span ports to sniff traffic, and vulnerability scanners knock over IoT devices by blasting out malformed packets and exploits hoping to get a return. Neither of these tactics are efficient nor do they return results that actually inform IT teams of anything more than just MAC and IP addresses. In both cases the result is the same–– inactionable data.
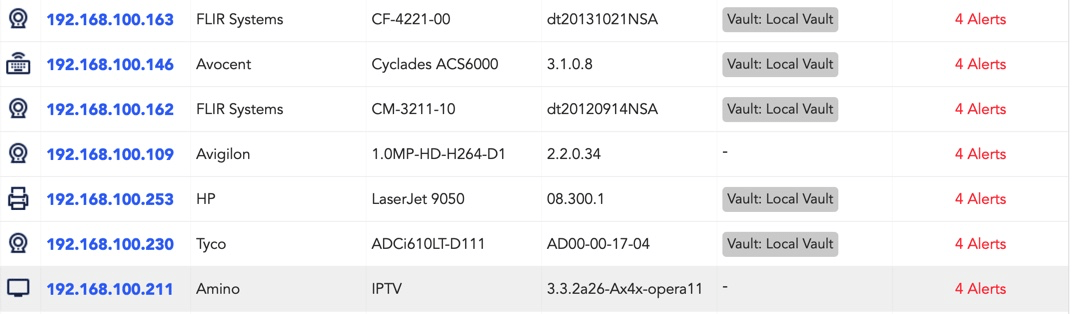
(caption: Typical device discovery results)
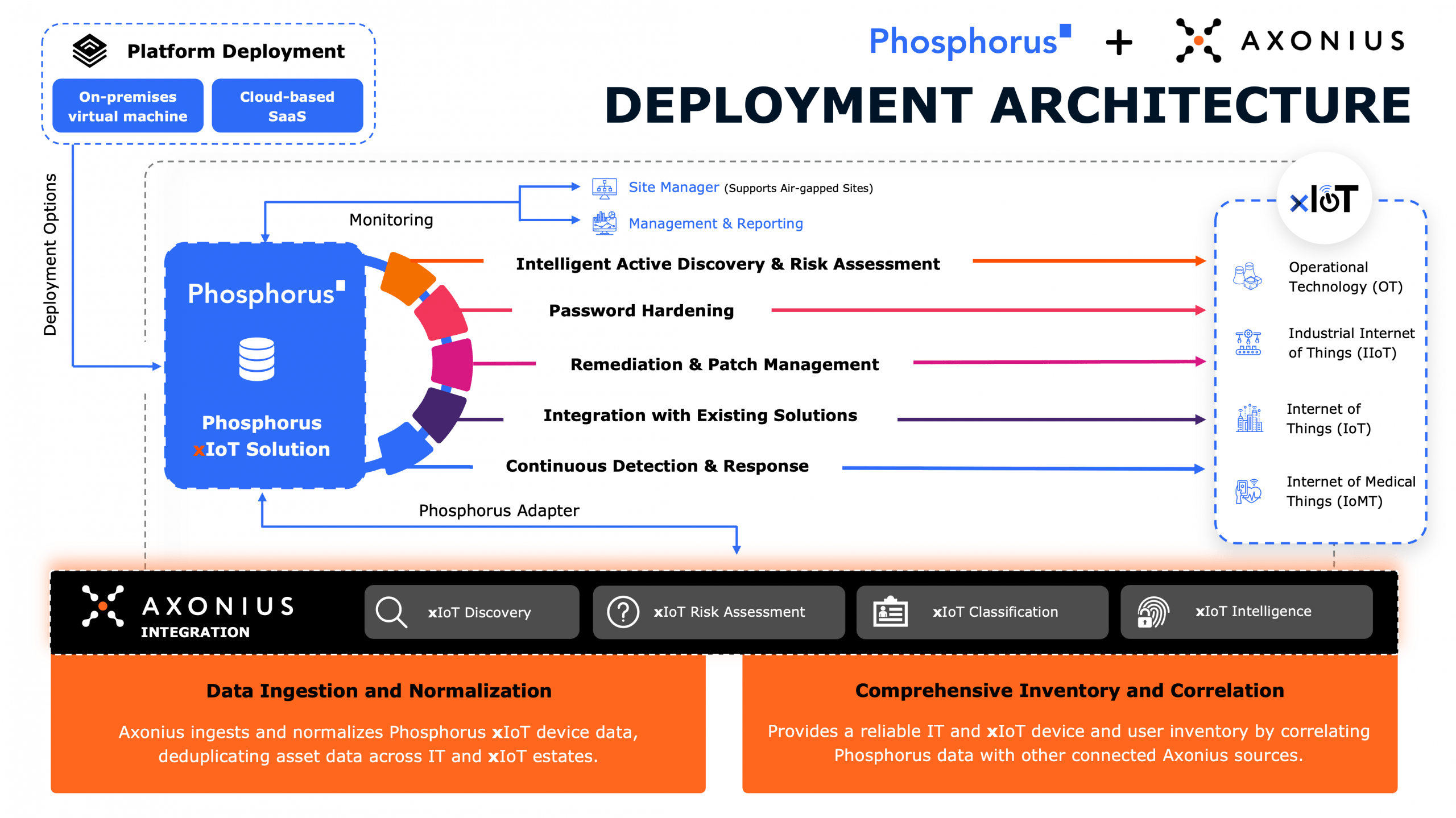
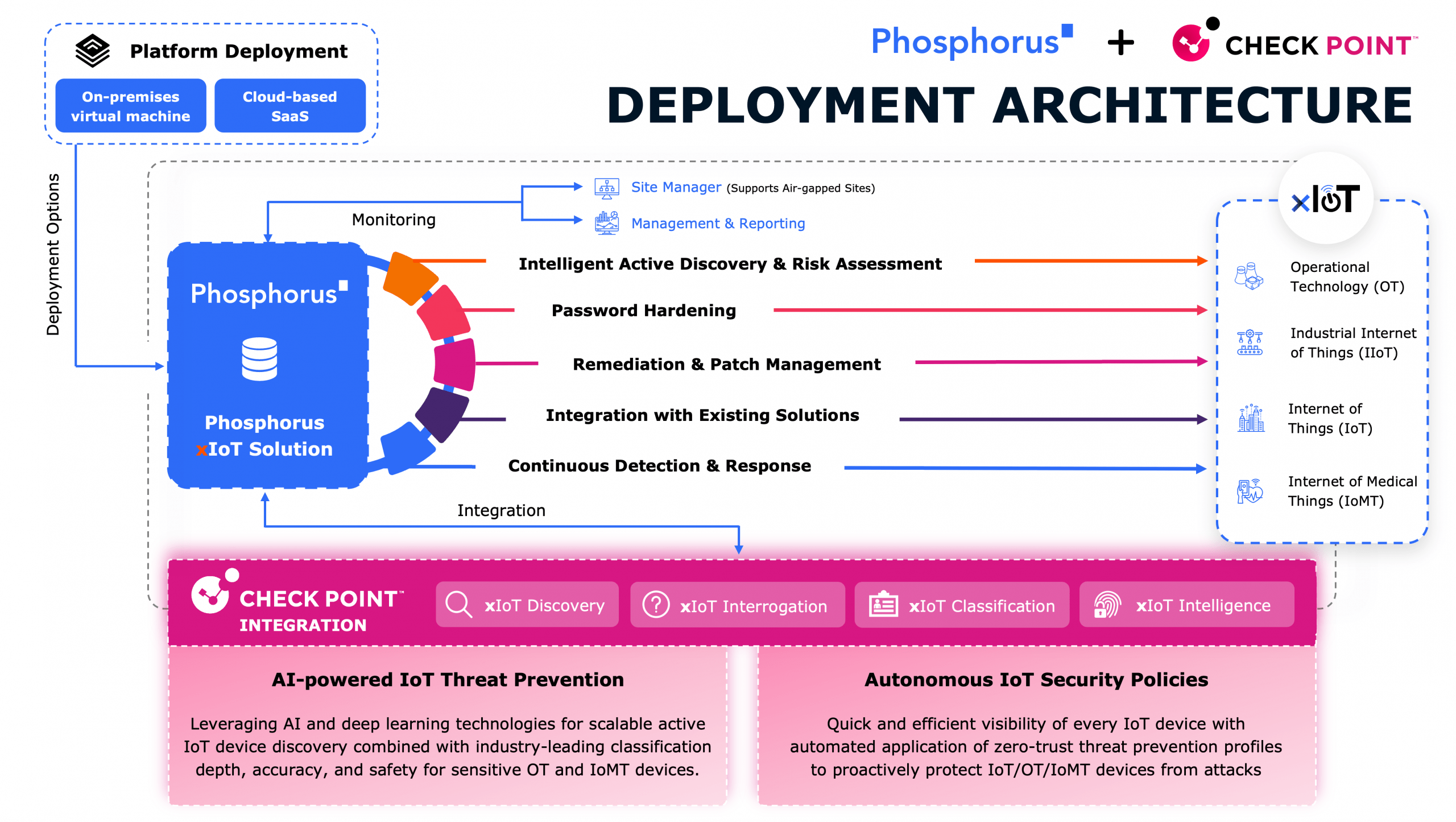
Achieving complete IoT visibility
In order to detect all IoT devices it’s necessary to communicate with them in their native protocols. And, in order to provide actionable insights the output needs to identify details about every device down to the make, model, firmware version, and CVEs. To secure a device throughout its life in the enterprise as it moves physically and logically over time, deep metadata is required––which neither NBAD nor vulnerability scanners can deliver.
To accomplish this charge, Phosphorus uses a combination of two internal mechanisms to talk to IoT devices: scanning and interrogation. Scanning is used to gather data about a device by discerning which services are running on various ports, ultimately determining the general class of device. Interrogation accesses the management interface of a device to gather more detailed information such as the specific model, and can actually login to the device to perform in-depth identification of credentials and firmware status.
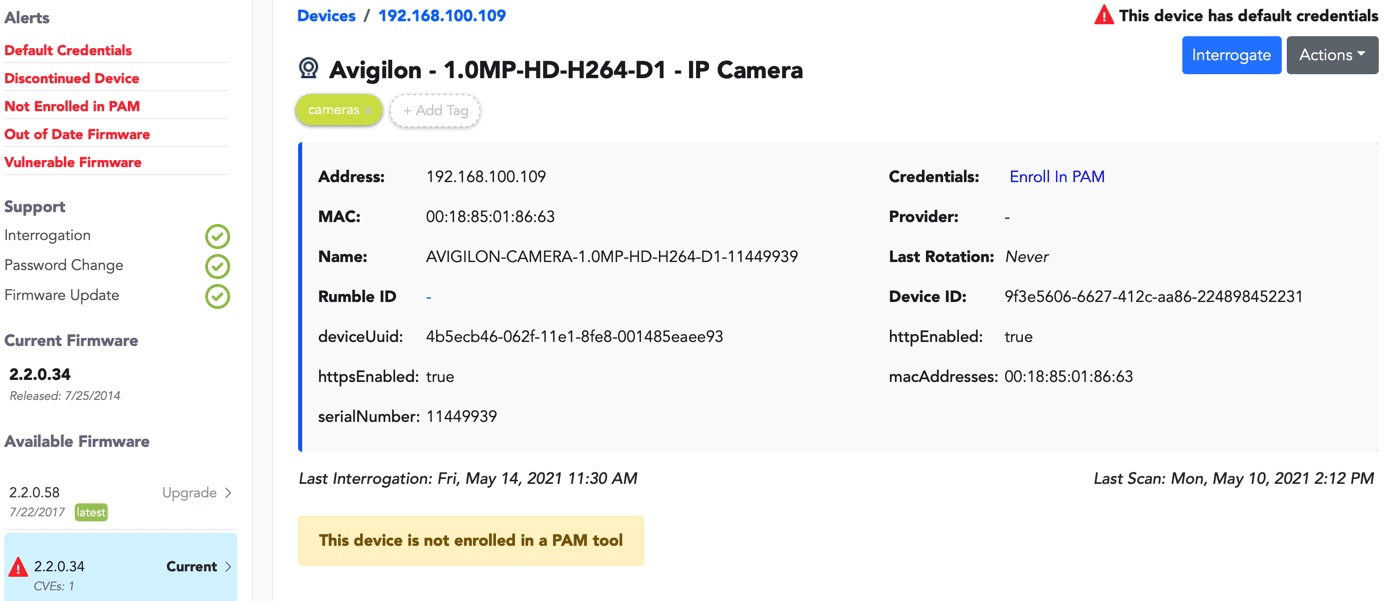
(caption: Phosphorus device discovery results)
Phosphorus provides complete visibility and greater awareness of every connected device. Using tools that are uniquely designed to communicate with and identify IoT devices without overpowering them, Phosphorus provides a complete inventory of IoT devices with all the information required to maintain them.
IoT devices likely make up a third of your enterprise, but securing them doesn’t have to mean doubling the work––we measure our work in milliseconds, not man hours. Phosphorus integrates into existing tools, so you can eliminate the IoT security gap all within your existing security environment. To see just how many vulnerable devices are lurking on your network, please join us for a demo of Phosphorus Enterprise.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.