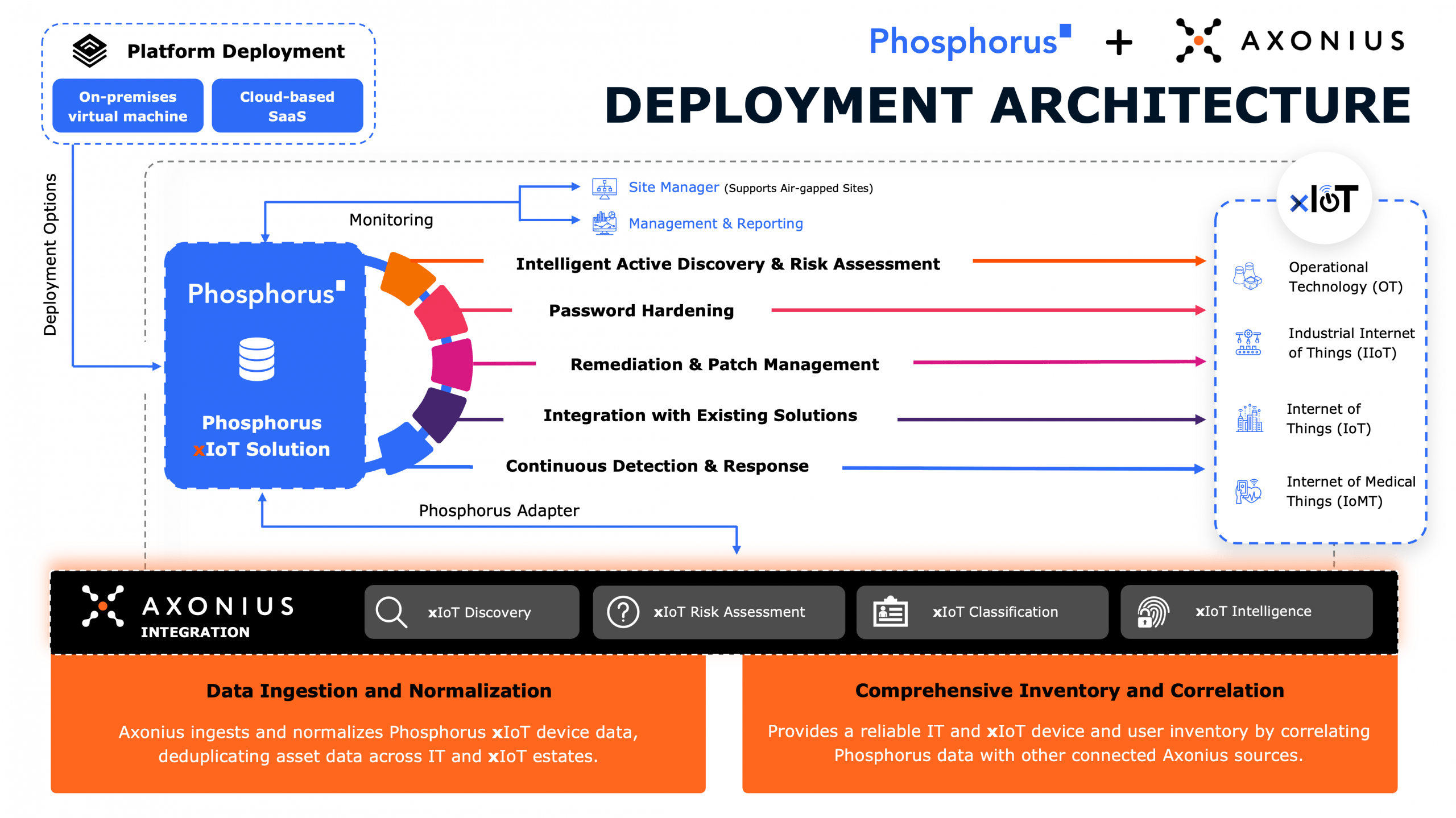
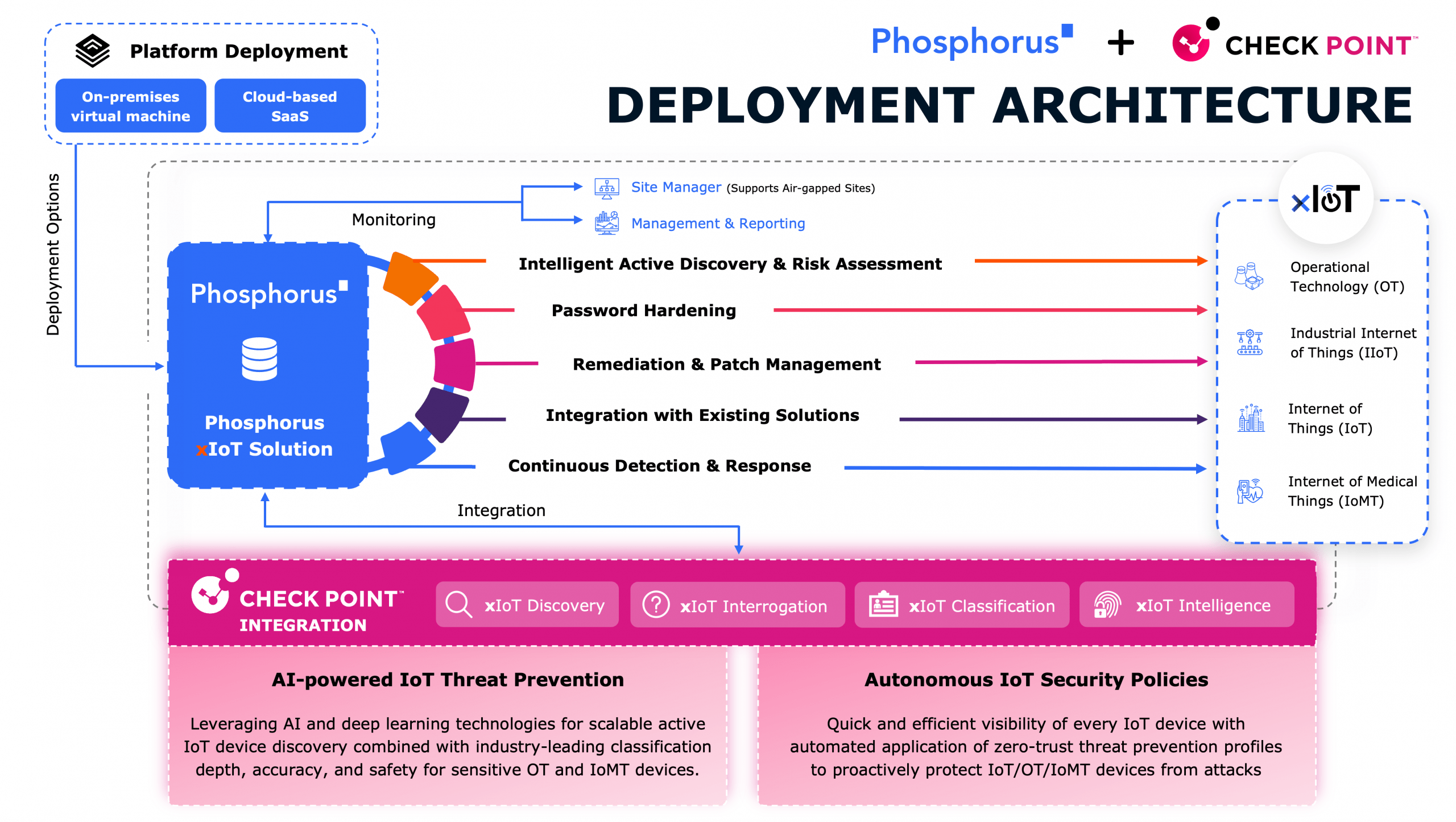
- Delving into the world of IoT security threats and the risks they pose in our digital landscape
- Unraveling the complexity of cybercriminal activity and how insiders contribute to security breaches
- Realizing the importance of taking a proactive approach to secure IoT devices
- Examining the role of IoT devices in organizations and the potential risks they carry
- Gaining insight into the necessity of staying informed and vigilant in the fight against cyber threats
TRANSCRIPT
John Vecchi:
Well, hello everybody. You’re listening to the IoT Security Podcast live on Phosphorus Radio. I’m John Vecchi.
Brian Contos:
And I’m Brian Contos, and we have a really amazing guest today. I’m so happy to have her on the show. Welcome, Tammy Hawkins.
Tammy Hawkins:
Thank you so much, guys. I’m so glad to be here.
John Vecchi:
Welcome, Tammy.
Brian Contos:
Tammy, it’s probably been a little over a year since we last… Well, maybe even two years actually since we were last on a podcast together. But for our listeners that didn’t hear the last one, maybe you could give a little bit of background about yourself, how you came up, how you got into cybersecurity, and what exactly did you do today?
Tammy Hawkins:
Absolutely. I’ve been so lucky to live a varied career, thank you to cybersecurity. I started an information security about 20 years ago working as an analyst and a test automation engineer. I’m originally from St. Louis, Missouri. In 2008, I interviewed at MasterCard as a business analyst for a financial risk scoring artificial intelligence system. And that job changed my life. I was at MasterCard for over a decade. And as you might imagine, working for the second-largest payment company in the world, there were a lot of different opportunities that I got to observe in the world that threat actors will put forward. I had the opportunity in working in identity and verification, fighting some of the best fraudsters in the world.
Brian Contos:
Wow.
Tammy Hawkins:
And getting to create security products that were so cool that people wanted to pay for it. They made amazing revenue. They were so strong. By 2019, I was in Dublin, Ireland. I had, at that point, made it in my career at MasterCard to being vice president of engineering of cybersecurity functions and cyber intelligence functions. And then I wanted to do something radically different. I went into gaming. I went to Activision Blizzard for a couple of years. That’s the last time that I talked to you, Brian, was when we were working on some anti toxicity solutions, helping people play nice, play fair in chat and verbal interactions with each other, which is really fun in the gaming world.
And today I serve as the director of cybersecurity and fraud at Intuit. I’ve been with Intuit for a couple of years helping protect their small business segment. And I’ve now in California. So I’ve gone from St. Louis to Ireland to California, all thanks to cybersecurity and information technology. So I feel extremely fortunate to be in this field. It is certainly a field that keeps giving more and more opportunity. It seems like every time we turn around, threat actors are finding a new way to take advantage of some vulnerability, whether that vulnerability is in your application, your infrastructure, or your humans.
So I just want to say thank you to you guys for having a podcast like this. I think it’s incredibly important that we as security professionals continue to share our knowledge because everyone needs to know how to be a little safer. So I’m really looking forward to talking more.
Brian Contos:
Yeah, no, you have such a great background. I love the fact that you’ve touched so many different types of business. I mean, I’ve never worked for a credit card company, I’ve never worked for a gaming company, but I expect they’re as bad as opposite as you could get in term of operations. But I do wonder, you mentioned working with fraud. And boy, just all the different types of security risk compounded by all the different types of fraud that you have to deal with when working in security for a credit card company.
I remember when I was in Brazil, I lived in Brazil for a couple years and I was working from some banks there, and skimming was a really big deal. As you know, people would go up to ATM machines and they’d basically stick these devices on top of the machines that look… They’re perfectly colored and perfectly fit, and people would swipe their cards, type in their pin, but it was actually a computer on top of it that was recording it all and sending it off. Did you ever get involved in that physical side and securing it? Because I just remember they had these awesome labs where they’re taking this stuff apart and seeing… Do we weigh it? Does the machine weigh a different amount now and all these things? Did you work on that at all?
Tammy Hawkins:
So I didn’t personally put my hands on them. What I helped protect though were the signals that would come over our network because we would have different signals that came from those, because they’re still credit card processors, right? They can be just sniffers, but some of them are also processing credit card transactions at the time to get as much money as they can at the time.
Brian Contos:
Wow.
Tammy Hawkins:
And it’s amazing, as you said, they can be incredibly thin, very imperceivable to the eye. One of the most common places for skimmers today that folks should be aware of are gas station pumps. Those are the most prevalent where folks put skimmers as well as ATMs.
Brian Contos:
I thought you were going to say the Vegas airport during Blackhat and Death Hunt, but okay.
Tammy Hawkins:
Yes. Yes. Yes, absolutely. You should be paranoid of everything at Blackhat. So I’m very well known to, anytime I walk up to a gas station pump or an ATM, I’m jiggling things before I insert my card into it because it’s so imperceivable to the eye. It looks just like your normal device that you would put your card into. But unfortunately, when you stick your card in that device, either it will do a real time transaction to try to take advantage and get as much money at the time they can. Or they’re sniffing, they have a little radio very nearby where you’ve just stuck your card in and they are grabbing every single card number of every single individual that slides it through.
I did battle an attack when I was at MasterCard in relation to that. They would gather all of these credit card numbers. And unfortunately, not only can you buy the skimmers online, you can also buy online the equipment to then produce credit cards. So they would produce fake credit cards, they would then hire people to go to ATMs and to drain them of money for any cards that would work, or they would go online and buy things and resell them. So those were some of the patterns that we would look for. We would understand legitimate purchasing behavior versus what does this illegitimate purchasing behavior look like. And the artificial intelligence system that I had the amazing opportunity to work on could detect in real time and block them from being able to process these transactions because it’s all about as return on investment for these criminals. As wild as it is to take a step back and reflect, they’re all doing it to get a return on investment. They run their fraud rings like tiny businesses.
So the more that you can impact their scale, both in how much they have to invest to conduct the attack successfully, as well as reducing the scale by which they can make money, you chase them away to hopefully other places and not your network or not your products. You’ll never get rid of all of them, but hopefully you make it harder for them to do damage and they go do damage elsewhere.
John Vecchi:
Yeah. Wow. I mean, I think looking at your background, I mean really I think a podcast like this is really built for a guest like you because you’ve been in different industries and you’re not only looking at the security side, the tools, the systems and software and things, but actually the threats themselves, the threat actors, the exploits, all of those. As you step back and look at the MasterCard, your touch on the gaming environment and now things like Intuit, how have the threats changed? I mean, are you still chasing the same types of actors? Are you still dealing with similar types of threats? Or how have the threats changed based on the different environments and companies and environments that you’re working in?
Tammy Hawkins:
It’s a great question. Having the fortune of being in this industry now for two decades, it is mind-boggling the difference. The scale and the sophistication by which these threat actors are performing today is radically different than what we saw a decade ago. A decade ago, you saw a lot of what we affectionately call script kitties who were playing around kind of trying to figure out how to do things, often buying things or using things from other people that they trusted would work. Today, it’s an enterprise. Literally, there are threat actors that are standing up small companies and they are hiring people and training them how to be the best at fraud. They will create campaigns, literal adverts saying, “Hey, want to make money at home quickly?” Sounds legitimate. You’ll show up to this interview. They’ll have you read a script. The script is pretending to be a tech support individual. And they have you read the script and they say, “Be really convincing. We really want the person to follow the steps that you’re guiding them with.”
What they’re doing is they’re training them for tech support fraud, which is really prevalent today. It comes in the form of phishing or smishing or vishing. And these folks are hitting corporates, companies that have large databases of customer relationship management type details, large telephone operating companies that have lots of phone numbers of everyone in the world because this is a self-perpetuating cycle. They want to get more and more and more phone numbers so they can send more and more phishing, vishing, smishing in the form of texts, phone calls. And ultimately, what the fraudster is trying to do is either get the targets’ credentials so then they can log into your financial banking site or they can log into whatever application that may be monetarily beneficial to them.
And they also want to know your number is working. They want to know they have a live connection at the end. And they want to see what further fraud they could potentially conduct. And they will share. Once they know your number and if they find a target that may interact, they may share your number with other threat actors. So the guidance that I’ve really been giving folks is very skeptical of any unfamiliar text message or any unfamiliar phone call that you get. Really double check. If it’s a text message, did it come from a number that you know? Did it come from an email?
There’s a lot of threat actors that are sending fake texts via email. They’ll pretend to be a reputable company that they know a lot of people use. They’ll pretend to be Amazon. They’ll pretend to be the United States Post Service or UPS. And they’ll ask for an immediate response or action. They’ll threaten you saying, “You have lost money or you will lose money, or we’re going to immediately suspend or terminate your account.” They’re trying to get you to interact to know there’s a live human on the other end, and then they’re going to take that conversation wherever they think they can take it.
What I always encourage folks to do is don’t interact. If you really think your Netflix account is getting ready to be suspended or terminated, take a step back. Go to Netflix’s original authentic website and go to their customer support there. Never give any of your details over a text message. Never give any of your customer details over a phone if somebody contacted you. You don’t know who’s at the other end.
Brian Contos:
Yeah. That’s such good advice. I know that people that are elderly are really being targeted because they haven’t necessarily grown up with this or experienced it or heard about these issues. So they’re going after these individuals and like, “Oh, if I don’t do this, I’m going to get a tax lien against me or something like this. I have to send this person $20,000 or some ridiculous thing.” Or, “Yeah, I guess it does make sense that I’ll go to Walmart and buy a bunch of Google Play cards to give to my tech support person.” They don’t know. So that’s really sad that they’re going after the most vulnerable people.
What I’m also seeing is there’s a lot of specialization. So we’ve been in security for a couple decades. And the cyber criminals, they’ve been in cyber crime for a couple decades. So they’ve gotten really, really good in their little niche areas and they’ve developed trust networks within different criminal organizations. One group here is really good at carding. Another group here is really good at transactions over crypto and how to hide your funds and money laundering. And another group is great at making malware, managing botnets. You have all these specialized groups.
And I love how you said that they run it like a business. And it sure is. Because we were involved with a takedown for a very large botnet that was focused on OT systems, so SCADA devices, PLCs, basically digital devices that control physics, flow voltage, temperature, things like that across manufacturing, power and energy, things like that, as well as some enterprise IoT stuff, the printers, the cameras, and some network devices, layer 2 switches, wireless access points. So the whole spectrum of xIoT if you will. But it wasn’t to destroy anything. They were simply installing malware. They’re actually getting malware on these devices. A lot of them were Linux, some of them are Windows, some of them were VxWorks, but a lot of them were these embedded smart devices, if you will.
What I thought was really interesting about this is these massive botnets that were made up of all these disparate kind of smart devices, they’re renting them out for about $30 a day. And for $30 a day, you could use this botnet to do DDoS attack, phishing, Blackhat, search engine optimization, malware distribution, you name it, any type of nefarious activity, which requires a large amount of devices. But this is where it gets to the part that they operate like a business. For $100 a day, you got 24 by 7 chat tech support to assist you with whatever campaigns you are actually doing. So they’re actually giving tech support like, “I really want to do a DDoS attack. And sure, for $30 I can have access to the system, but where do I start?”
John Vecchi:
Right.
Brian Contos:
[inaudible 00:14:29] “Well, for $100 a day, you get our gold service.” And I’m like, “This is no joke.” And when you start looking at the folks running these organizations, it’s certainly not the Hollywood image of the high school kid in his mom’s basement drinking Jolt Cola and playing video games, although there might be some of those. These are people that oftentimes have master’s degrees in computer science or finance. They’re living in countries where they have safe harbor. So there’s like, “Look, hack all you want, do all the crime you want. Don’t hack in our country or any of our allies, but as long as you’re doing it to other people, we don’t care. We’re not going to arrest you,” things like that. So are you starting to see in your sort of day-to-day operations a blurring between those threat actors that are nation state actors and maybe cyber criminals and finding that a lot of the times it’s actually the same people doing this?Tammy Hawkins:
Yeah. Yeah. And I always remind people I’m paid to think about the dark things and I live and breathe the dark things all the time. Everything you’ve said is absolutely true. And unfortunately, a trend that I’m also seeing increase is insider workers.
John Vecchi:
Mm-hmm. Insider threats.
Tammy Hawkins:
They will literally recruit folks that are insiders in customer support already or insiders in an organization and take advantage of that, which it gets really, really scary to be able to parse what is legitimate behavior for your employee base versus illegitimate behavior so that you can protect your customers. And also the threat actors are attempting to always get a foothold to try to appear like an insider as well. And as you’ve said, it’s just so much more sophisticated.
Some of our methods to deter and protect included knowing phone numbers, knowing identity. They can rent out identity, they can rent out VoIP, voiceover IP type phones. I mean, as you said, you can hire fraud experts to do everything for you. And if you can figure out how to get your return on investment, well it’s worth the investment If I have the money. And often, the money is illegitimate funds they’re starting with anyway, so they’re not that concerned if they lose a little bit of it. So it’s a different time to be operating in. And with that level of growing threat, companies and individuals really have to think different about risk posture and know a little bit more about security that maybe we didn’t always know before.
And you said it so well in that I love what I do because I get to protect folks. The part that breaks my heart is seeing the folks that are taken advantage of, and it’s often those that are less tech savvy, those that are elderly, but I’m also going to say they also take advantage of periods in which we potentially may go through a recession or folks are having tougher times in an economic space. I’m seeing a lot of folks… Like I went and got a facial the other day and the lady, I told her I worked in fraud, and she said, “Oh my goodness, I fell for a Bitcoin hack the other day.” There are so many people that have fear of missing out relative to making money on crypto. They hear that people can invest in crypto and make a bunch of money. Threat actors are taking advantage of that, and they’re sending folks messages in their DMs on whatever social media saying, “Hey, if you just put X amount of money in my wallet, you’ll get Y amount of money back to your wallet.” And it’s all a scheme, right?
I don’t even want to think about the millions that they’re making with those little bits of money that they’re draining off of people. And so it gives me a lot of joy that we shut these people down at scale, but the scale that I see them operating at makes me know we need a lot more security professionals in our industry to continue to battle this arms race.
John Vecchi:
Yeah. Let’s talk a little bit about the IoT. We call it xIoT, Tammy, just simply because there’s so many of these devices and you’ve got the enterprise IoT, the usual suspects, your printers, cameras, phones, but also door controllers and all kinds of things. And you’ve got the network side. I mean, a layer 2 switch is an IoT device. You can’t put endpoint security on there, but you also have things like KVM switches and network attached storage and all. Then you’ve got all the OT stuff. Brian was just talking about one of the exploits there, like a big botnet ring that targets OT devices, PLCs and HMIs and pumps and all those kinds of things.
But what’s interesting about that, I’m interested to get your thoughts on that, is you talked earlier about just the way the threats have changed and the sophistication of them over the years, and you think of how sophisticated they are now. And then you look at those devices today. And the state of those devices is like you’re back in 1990, right? The average age of firmer on those things is over seven years old. I mean, could you imagine a phone where you didn’t update the firmware? It’s like running NT 3.5.1 or something. They’re all default passwords, credentials are all default. They’re loaded with vulnerabilities. Mostly these things ship with them kindly out of the box. And so you’ve got this interesting kind of paradox. You’ve got a very sophisticated threat actors with these devices that are back in the ’90s in their state. Is that something that worries you? Is that something you see with the kind of devices that you’re dealing with? What are your thoughts on that?
Tammy Hawkins:
Yeah. In short, it’s terrifying, right? You described the situation so well. I affectionately call it the internet of insecure things. It’s for all the reasons that you listed, right? Some don’t phone home, some will never have updates. Just because a risk posture was okay even a year ago, it may not be okay a year later if I can get some kind of network connectivity or even if it’s air-gapped, right? There have been proven situations where something is air-gapped or DMZ’d and folks still got into it. It’s a foothold into your network, right? If it’s connected to the rest of your systems via a network, it is a potential foothold.
So the first guidance that I always give… And it’s not a silver bullet, we all know in security there are no silver bullets. That’s why we need belts and suspenders, many layers of protections and everything that we do. But the thing that I do, I do have IoT devices in my home. I’m a tech geek. Of course, I do. One, I research, research, research, research any device before I will bring it in my home. There’s, usually these days, oodles of security articles. Folks are very interested in internet of things and the security associated. Look up Google what the security posture is for the device that you’re thinking about bringing into your home and go in with eyes wide open of the security risks that you’re bringing into your home because there’s a risk with everything that you use. So understand the risk and then manage the risk of appropriate to the posture that you want.
For myself, when I look at the risk, I want devices that regularly phone home on the internet that are getting patches regularly. Ideally, I review what type of data does this IoT device gather and send and what type of data does it store in any type of cloud. Do I have an opportunity to not store in a cloud? Do I have control over the retention of that storage in the cloud? If you’re a bit more of an advanced user, I also segregate my network. I will only put IoT devices on a guest network that I’ve stood up that has extra protections. I also like to use Wireshark on my own network. Never use it on anybody else’s network. That’s not legal. But you can use it on your own network. And I do so.
I like to use Wireshark and do some packet sniffing relative to that guest network and see exactly what that IoT device, if I can see… First of all, I like to see, “Can I see it?’ Is it encrypted? Because that’s another kind of security step for me for this particular IoT vendor. How far can I sniff your traffic? And when I sniff your traffic, what are you actually sending versus what you’ve told me that you send? Right? I patch the device regularly. I also will research the devices regularly, all of the devices on my network and decide, “Does this meet my risk posture anymore?” Right? Because things change over time. Maybe something that was secure a few months ago is proven now not to be so much.
So those are some of my recommendations just so that you go in eyes wide open. If some of those techniques are a little beyond your capabilities, call your tech friend. I’m sure they would be delighted to help you or show you and talk to you until your eyes glaze over about how insecure your particular IoT device is. And then you decide what the right level of security is for you. I’m not here to dictate to other people what the right level of safety or security is for them. Mine’s a little bit different just because of what I know and what I do. But ask your friends to help guide you if you have doubt about security, especially with your IoT devices. What I don’t advise is just go buy the cheapest device that you can and hook it onto your network. That’s just a recipe for disaster. Go in with eyes wide open.
Brian Contos:
Yeah, no, those are good points. It’s funny that line between enterprise and consumer, there are so many products that are used on the consumer side in xIoT that are also used on the enterprise side, security cameras, layer 2 switches. Just a couple examples. But I know after the holidays, there’s always this big influx because people got all these cool new devices and they’re like, “Hey, I’m going to take this to work with me.” And now it’s all plugged into the network and the IT security team’s like, “What’s all this stuff?” But one of the things that I think John and I found interesting now that we recently published a report, The Threats and Trends for xIoT, and we published this in late 2022, it was based on five years of research and several million devices that we analyzed in enterprises. I think the most compelling stat for me, and there was a lot of interesting stats, but there’s about three to five xIoT devices per employee in an organization. So a company of 10,000 people has somewhere between 30,000 to 50,000.
You’re usually not going to guess that because you’re, “Oh, I forgot about all the voiceover IP phones. Oh, I forgot about the 3,000 cameras and all the digital door locks and all the KBMs switches.” And nobody has a good inventory around these. Probably the one that stands out in my mind the most are security cameras. We work with large financials and manufacturing and gaming and casinos for example. Casinos, they have security cameras, which as far as I can tell, all they do is watch other security cameras. They have so many security cameras. And for them, spying is certainly an issue. If somebody could get access to those devices and record the audio in the video, that’s certainly an issue for large businesses. Cameras in boardroom or manufacturing facilities, defense, things of this nature.
Cryptojacking’s another one because they’re just Linux servers. At the end, you log into these things that are in BUN 2, they’re BusyBox. It’s a Linux server, you can load tools, you can compile stuff. And in many cases, they’re more powerful than a laptop. So I can go ahead and mine crypto on these devices. But what I think was really interesting, and this is kind of… You never really get to say that much, “Hey, the United States government did the right thing when it came to cybersecurity.” You don’t get to say it as much as you’d like.
But a couple years ago, the United States banned certain cameras, Huawei, Hikvision, [inaudible 00:25:53] and a few others for use in government facilities as well as government contractors. Because when you turn that camera, you say stop recording, it turns the light from green to red, but it still records, it still grabs video, it still grabs audio, and it streams it to a remote location for analysis. Again, these are cameras that are quite popular. And in fact, one of the most popular cameras on Amazon for several years came shipped out of the box with this type of malware on there that allowed this type of activity.
So fast-forward to, I think it was November of 2022, the US government finally said, “Look, guys, these are just two dangerous, these devices. We’re actually making it illegal now to import or to sell with the United States.” And I was like, “Wow, they really stepped up.” I didn’t expect that. I thought more regulatory mandates and this or that. But no, they actually made it illegal. And you can’t get these devices anymore. You can still find them all over the rest of the world. People are still using them. But now I’m starting to see other countries kind of follow suit.
And just yesterday, Australia… It was in CNN News or CNN Business. They said Australia is purging Chinese-made cameras from all Department of defense systems just because of that massive risk. And not only the spying capability, but the fact that let’s say I get in through a phishing attack and I’m on your laptop, I don’t want to stay there because you have all these security controls. I want to pivot from there to a camera, to a printer, to something else where you’re not really paying attention. I know I can get in because you probably have a default password or no password. If you did change it, there’s tons of vulnerabilities. So I know I can probably get into at least 10,000, 15,000 systems to hide. And then they’re attacking IT and cloud assets and siphoning that data out.
This is such a huge backdoor. And we’re seeing cyber criminals in nation state saying, “This is the new new. They’re not banging their head against the front door and the firewalls and the IPSs in the stores and all that. They’re saying, “Hey, you got 50,000 unsecured Linux boxes.” I’m pretty sure that’s the easiest way to get into your organization. So my question that’s buried in this diatribe of talking about these cameras is you’ve worked at a senior level in security for quite some time across these different organizations. Is that threat/ the fact that these xIoT Linux boxes and this mass volume are sitting throughout the enterprises, do you think that that’s being grasped by, one, the security professionals in the organization, and two, by business leaders in this organization? Do they realize that there’s this big back door? Or like John said, are we back in the 1990s and we still have to evangelize and increase awareness and education as it relates to this big hole?
Tammy Hawkins:
Well, I’m going to do the typical security professional thing and say, it depends. It depends on the organization. It depends on the security professional. My humble opinion is I tend to lean more towards John’s opinion in that we are not where we need to be as a security profession in general and as an industry and really being skeptical. I still remember, and frankly, there’s still a lot of companies that support BYOD, bring your own device, and still don’t have great controls relative to all those devices that they’ve allowed now to get onto their network.
I’ve seen organizations that have allowed these BYODs to be on their network with no guest password, no reset of guest password. Who knows what devices are attached from whom on that network, depending on how close they could get to your network, right? So I don’t think folks have… One, in my humble opinion, I don’t think folks have helped humans in the organization understand safety holistically and really continue to real time educate employees in their corporate life as well as in their personal life, the things that we need to really think about to keep ourselves, our family and our corporation safe. So that’s part of the trust in education.
I also feel that organizations haven’t done enough of the verify. What is on my network? Do I understand everything that’s on my network? And if I don’t, have I kicked it off until I can understand what is on my network, what is the risk posture and how I contain that risk posture? Because you said it incredibly well, Brian, all I’ve got to do is get one foothold, just one, and then figure out how to pivot laterally. And then if I can find a special place to go, I can take you down, right? Don’t give them the opportunity. Don’t give them the foothold. Be really thoughtful of anything that you’re letting onto your network. Be able to validate that risk posture and act on it. I don’t know that we’ve done that well enough to your point and the internet of things.
John Vecchi:
Yeah. Well, and you touched on something there, Tammy, which is very interesting. You kind of referred to this collision. It’s like a double-sided coin of the actual threat to the data, the business, and humans. The threat to humans. I mean, do you see that? An example of this is recently, very recent, this is ripped from the headlines, a very prominent city. I won’t say the city. I found that the district attorney in that city had his team deploy cameras. And as Brian referred to, what people don’t often realize is these cameras actually capture audio. Most people don’t quite think of that. They actually installed these cameras in the DA office outside and around specifically to not only watch but to listen. And it was just discovered.
So when you think about that and the fact that frankly, a good majority of these cameras, and we see them all, actually record audio, this is where the human element comes in. And it obviously it’s out in the public forum. And Brian referred to the fact that there’s a ban on these devices because they’re spying on you. But most people think that that spying is just simply capturing the video. Sometimes they don’t understand it’s actually listening to them, right? So this is now happening where it’s not just outside on a street. It could be inside in a building, it could be in the district attorney’s office. This is now where you might get this collision of the security threat and the privacy and the human element of it. I mean, is that something you see that is a factor in just the progression of the awareness, all of that, the human side of it? Does that come into play?
Tammy Hawkins:
Yeah. My opinion is, I think a lot of folks think, “Somebody else is thinking about that. Somebody else is making sure that we’re safe and secure.” You can’t assume that. You really can’t. There are so many different methods that unfortunately threat actors are trying to take advantage of, and especially trying to take advantage of human goodwill, that we’ve got to do a better job as security professionals. We can’t protect them all. We’ve got to teach them how to protect themselves. And I believe that’s in real time training within corporations of the great IoT lessons that you all are teaching on this type of podcast, doing regular phishing type of exercises within your OR organization to teach people these types of things before they really happen to them because it’s so…
I have to talk to people when they’ve had the worst day of their lives so often after they have been taken by a threat actor, and the first thing they say is, “I just wish I would’ve known. I wish I would’ve known how to protect myself.” And that’s on all of us as security professionals to demystify what it is that we know and to just offer it constantly in consumable ways that people can help up their own security posture. We all play a part in this. There are not enough security professionals to protect everyone else, and there are far more threat actors than there are security professionals, and unfortunately, far more targets than there are security professionals.
So we’ve got to help everyone understand and come up with more scalable protections to help the humans protect themselves. And that’s something that I would love to see every company, every security professional, everyone lean into, is just being more giving of our knowledge and more giving of our capabilities to scale up security knowledge and tooling for folks that are not as savvy with technology or security as we are. How are we breaking it down for them and giving them tools that help them protect themselves? We shouldn’t lecture them. We shouldn’t judge them. What we should do is try to educate and help them.
Brian Contos:
And let’s be very honest, the amount of security experts and tools and consultants and outsourced services that a large financial corporation can hire juxtaposed to Bob’s Bagels down the street, which has a bunch of computers and some IoT stuff and some things to protect, it’s quite different. And they might get hit by the same types of fraudsters trying to do the same types of malicious things, right? So everybody needs to be aware of this.
Well, Tammy, we could talk for hours. Your stories are so fascinating. What I like most about them is you can tell they’re all nested in these real life conversations and incidents that you’ve been dealing with for so long. And I love the people perspective you bring to this. But as we wrap up, just one last question. You’ve alluded to some of this throughout the conversation, which I love, but what sage words of advice can you give to our listeners out there, whether it’s their work concerning about their individual security at home or a medium or a large sized organization?
Tammy Hawkins:
My guidance is always trust but verify. I don’t want everyone to walk around being paranoid about everything. I do that enough. But I do want people to be a little bit skeptical, to just be a little bit thoughtful before you click the link. Before you give away your very special information, like your social security number or your login details, be skeptical of who that person is on the other side. If you’re not looking them in the eyes, if you’re not physically with them, it could be someone that you do not want to hand that information to or that you do not want to interact with. If you even have a moment of doubt, just pause. Just take a pause and think about what you’re doing before you act.
There are so many people that I speak to after a security event, and that’s one of the biggest reflections is, “Gosh, why did I click that link? Why did I talk to that person? I should have known better. I should have just waited a moment,” right? So often, threat actors will say things to try to get you to quickly act. No, that’s a clue. If somebody’s telling you you’ve got to immediately do something, don’t immediately do it. Take a step back, take a click and just think about it. Maybe go talk to a friend about it, right? Ask for some guidance. Taking that extra minute to think something through can be worth a lot of avoided regret. Just be a little thoughtful before you act.
John Vecchi:
Yep. Well, wow. Very practical, but powerful advice. Fantastic, insightful discussion. Tammy, thanks so much for joining us today. Thanks to my co-host Brian. But Tammy Hawkins, thanks very much for being our guest today.
Tammy Hawkins:
Thank you, John and Brian. I assure you the honor was mine. And I will come talk to you anytime. You will have me here. Thank you so much for what you are doing.
John Vecchi:
We will have you back. There’s no question. And remember everybody, the IoT Security Podcast is brought to you by Phosphorus, the leading provider of proactive, full scope security for the extended internet of things. And until we meet again, I’m John Vecchi.
Brian Contos:
And I’m Brian Contos.
John Vecchi:
We’ll see you next time on Phosphorus Radio.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.