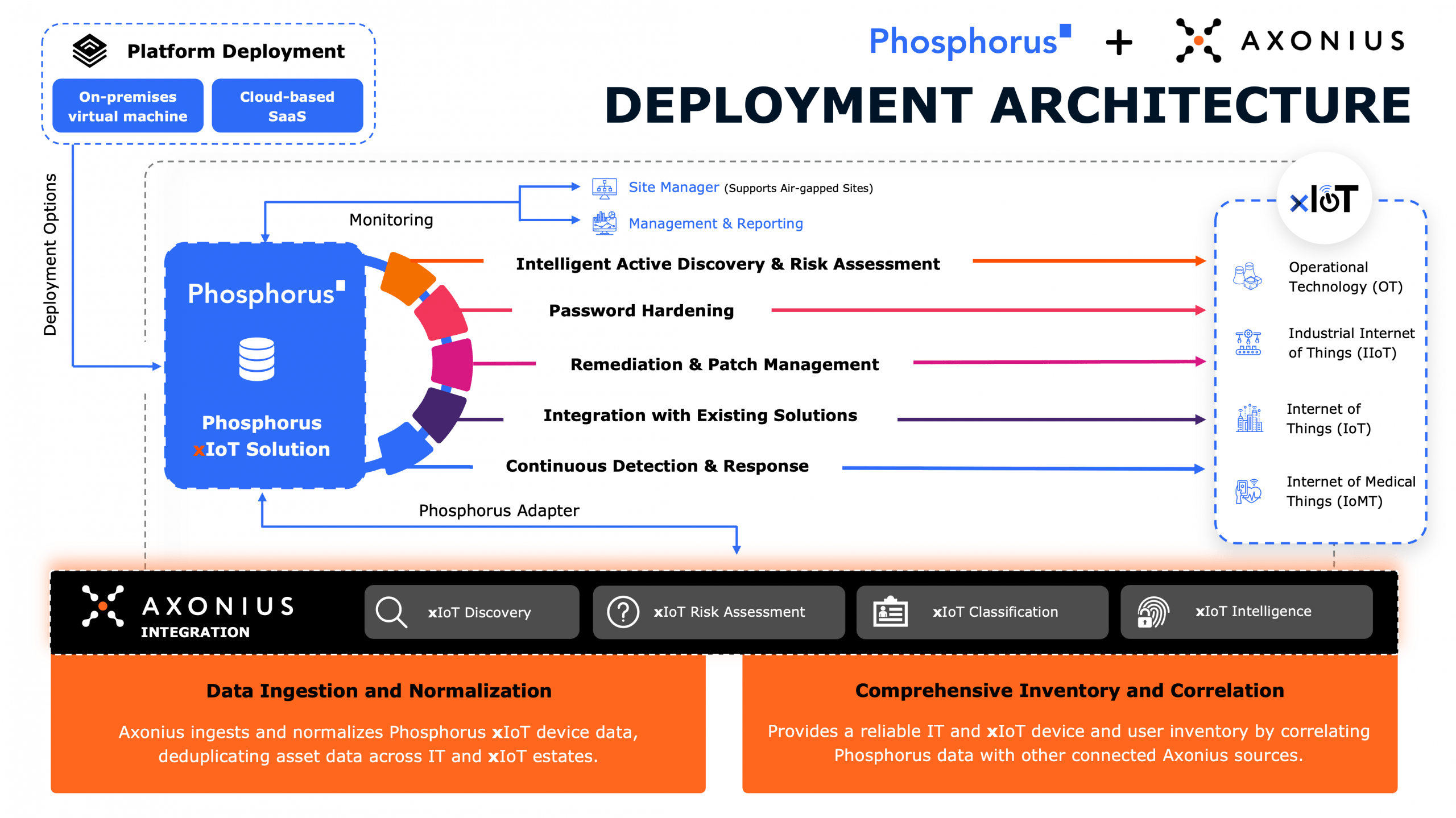
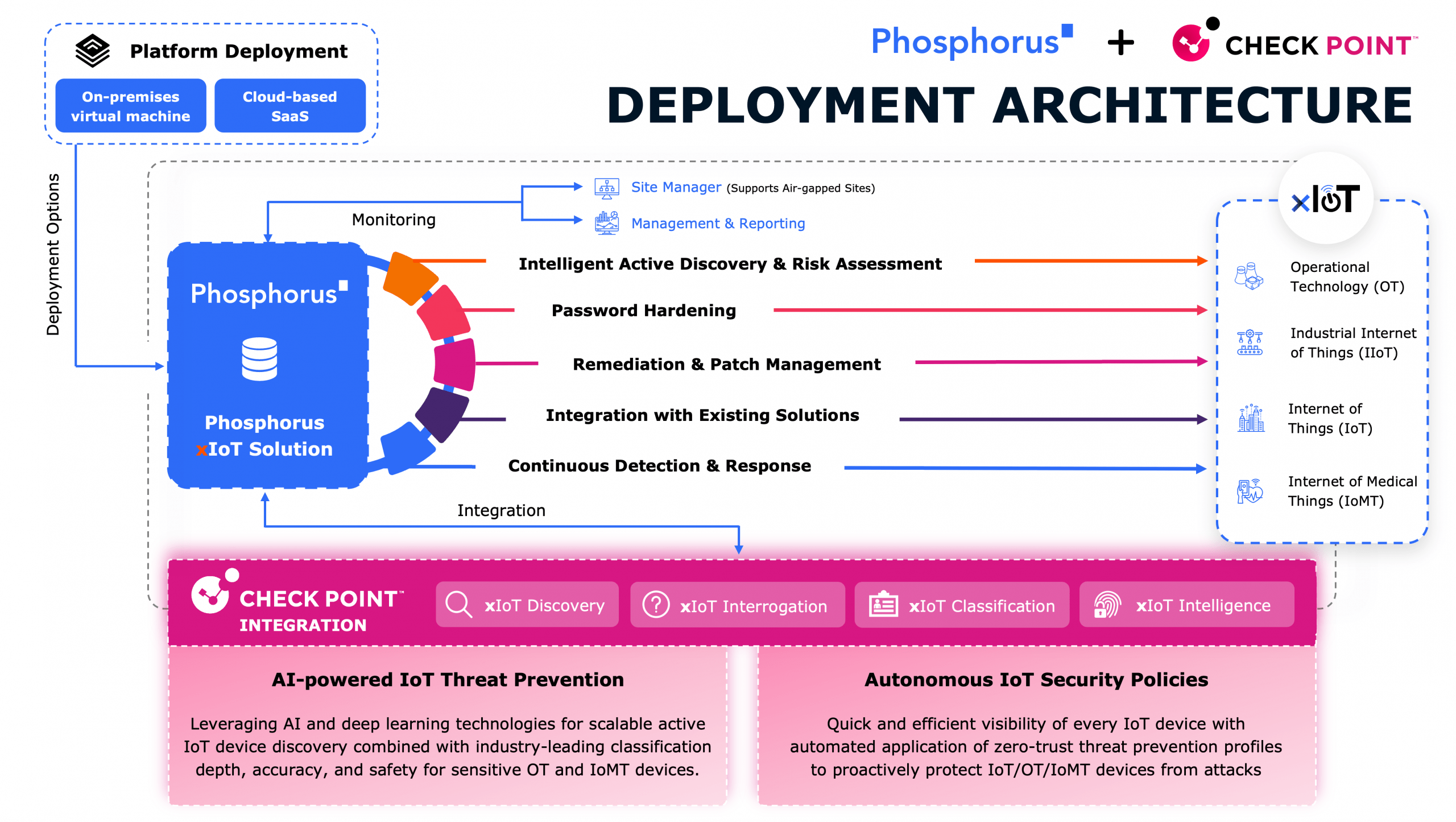
Originally published as commentary for the FCC, Phosphorus Chief Strategy Officer Sonu Shankar writes in response to Commissioner Simington, advocating further for a new security model of Shared Responsibility. Read the original article.
Commissioner Simington¹ has advocated to require IoT device manufacturers (specifically, wireless device manufacturers) to explicitly commit to supporting their devices with firmware updates, an important step in the direction of securing IoT devices at scale.
With the proliferation of IP-connected devices in various sectors such as Healthcare, Manufacturing, Energy, Retail, Hospitality, Financial Services, and several others, emphasizing fundamental security hygiene for devices should be a paramount consideration in any regulatory proposal aimed at securing IoT, including IoMT, ICS, OT, IIoT, and more. From a threat modeling standpoint, three primary areas of significance in IoT are passwords, configuration, and firmware.
Undoubtedly, the use of default passwords² stands out as the most trivially exploitable vector by threat actors when targeting this fast-growing attack surface aspect of IoT. If an IoT device — patched and running current firmware — uses a default password, a threat actor can still effortlessly compromise the device without the need for developing a sophisticated exploit that targets firmware vulnerabilities; they would simply use the default password. Furthermore, the sheer diversity of devices (manufacturers, deployment models, operating systems, communication protocols) in this space also means that there is no body of prescriptive configuration recommendations that map to IoT at scale. Device misconfigurations and a general lack of adherence to best practices continue to leave large critical infrastructure environments at risk³.
Lastly, echoing the concerns⁴ raised by Commissioner Simington, it is worth noting that IoT firmware patching remains a challenging issue, with the practice often not deemed essential in many critical environments across the United States today.
Much like the Shared Responsibility Model⁵ in cloud security that defines the responsibilities of both the cloud service provider and the customer regarding securing and managing cloud environments, the ubiquity of IoT now necessitates immediate attention and underscores the urgency for a similar model of “shared responsibility” with regards to IoT security. While there must be requirements directed at device manufacturers, operators need to understand that they, too, have a role to play when it comes to securing IoT. Any regulation aimed at device manufacturers should, therefore, also highlight the importance of device manufacturers clearly communicating the operator’s responsibility in adhering to fundamental security hygiene activities, including the following:
- Identify the number of devices within an operator’s environment using default or weak passwords, transition them to strong passwords based on each device’s password complexity requirements, and implement password rotation schedules for those devices.
- Determine how many active, operational devices have reached their End-of-Life and establish a plan to remove or replace them
- Identify how many devices are running with risky configurations, update the device configurations to address those security risks, and establish a continuous monitoring model to detect and respond to drift from a stable, secure state.
- Identify how many devices are running with outdated or vulnerable firmware, assess the operational risk of running those devices unpatched, and set up IoT patch management as a business function. While all released patches may not be critical, it is important to identify devices requiring immediate patches and ensure timely updates.
- Determine how many active, operational devices have been banned⁶ for use by the United States Government, and establish a plan to remove or replace them. In the interim, it may be necessary to disable or isolate them.
Leading industry research⁷ indicates that over 50% of IoT devices in enterprise settings operate with default passwords and a quarter or more are running firmware with critical vulnerabilities. There is now increasing evidence that vulnerable IoT devices are incredibly prevalent across U.S. footprints. Given the widespread presence of these devices, the risk of a crippling attack grows as regulatory standards continue to overlook the vital need for fundamental security hygiene practices for both manufacturers and operators.
- 1 Nathan Simington. (2022, December.) Commissioner Simington Calls For Mandatory Security Updates For Wireless Devices. https://docs.fcc.gov/public/attachments/DOC-390173A1.pdf Accessed September 12, 2023
- 2 Danny Palmer. (2017, April.) Is ‘admin’ password leaving your IoT device vulnerable to cyberattacks?
https://www.zdnet.com/article/is-admin-password-leaving-your-iot-device-vulnerable-to-cyberattacks/ Accessed September 12, 2023 - 3 Cybersecurity and Infrastructure Security Agency. (2018, August.) Schneider Electric Modicon Quantum Vulnerabilities. https://www.cisa.gov/news-events/ics-alerts/ics-alert-12-020-03b Accessed September 12, 2023
- 4 Nathan Simington. (2023, September.) Ask HN: I’m an FCC Commissioner proposing regulation of IoT security updates. https://news.ycombinator.com/item?id=37392676 Accessed September 12, 2023
- 5 Cybersecurity and Infrastructure Security Agency, United States Digital Service, and Federal Risk and Authorization Management Program. (2022, June). Cloud Security Technical Reference Architecture.
https://www.cisa.gov/sites/default/files/publications/Cloud%20Security%20Technical%20Reference%20Architecture.pdf Accessed September 12, 2023 - 6 Federal Communications Commission. (2022, September.) List of Equipment and Services Covered By Section 2 of The Secure Networks Act. https://www.fcc.gov/supplychain/coveredlist Accessed September 12, 2023
- 7 Phosphorus Cybersecurity. (2022, December.) xIoT Threat & Trend Report. https://phosphorus.io/xiot-research-lab-report/Accessed September 12, 2023
Author
Sonu Shankar
Sonu Shankar has over 15 years of senior leadership experience in the cybersecurity industry. Prior to joining Phosphorus, he served as the Head of XDR Product at Arctic Wolf, in addition to earlier leadership and strategy roles at Cisco, where he focused on trustworthy technologies, threat detection, and cybersecurity strategy.
Related Posts
Today marks a significant milestone in our mission to secure the Internet of Things:...
Phosphorus Cybersecurity Inc., the leading provider of security and device management for the extended...