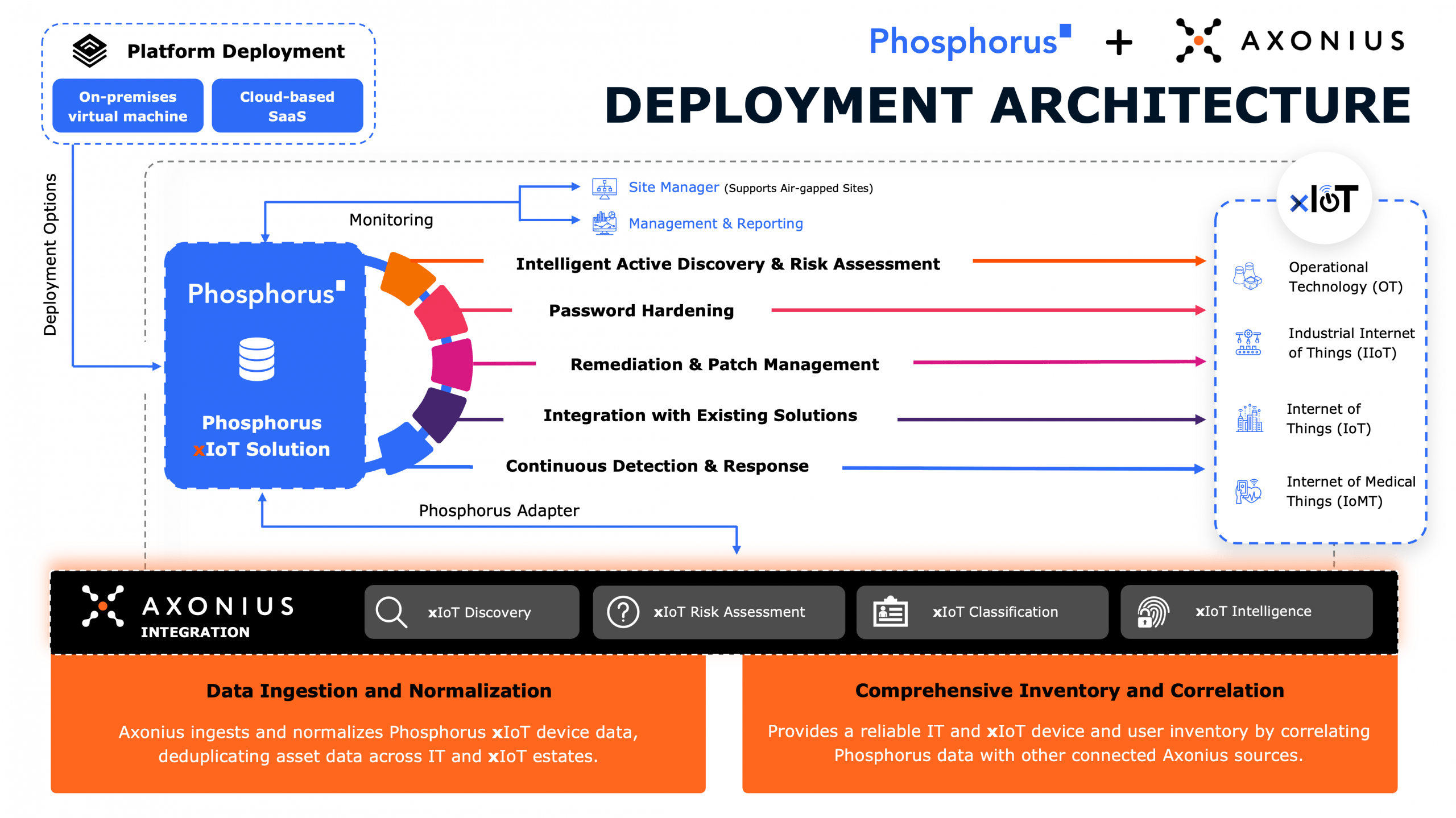
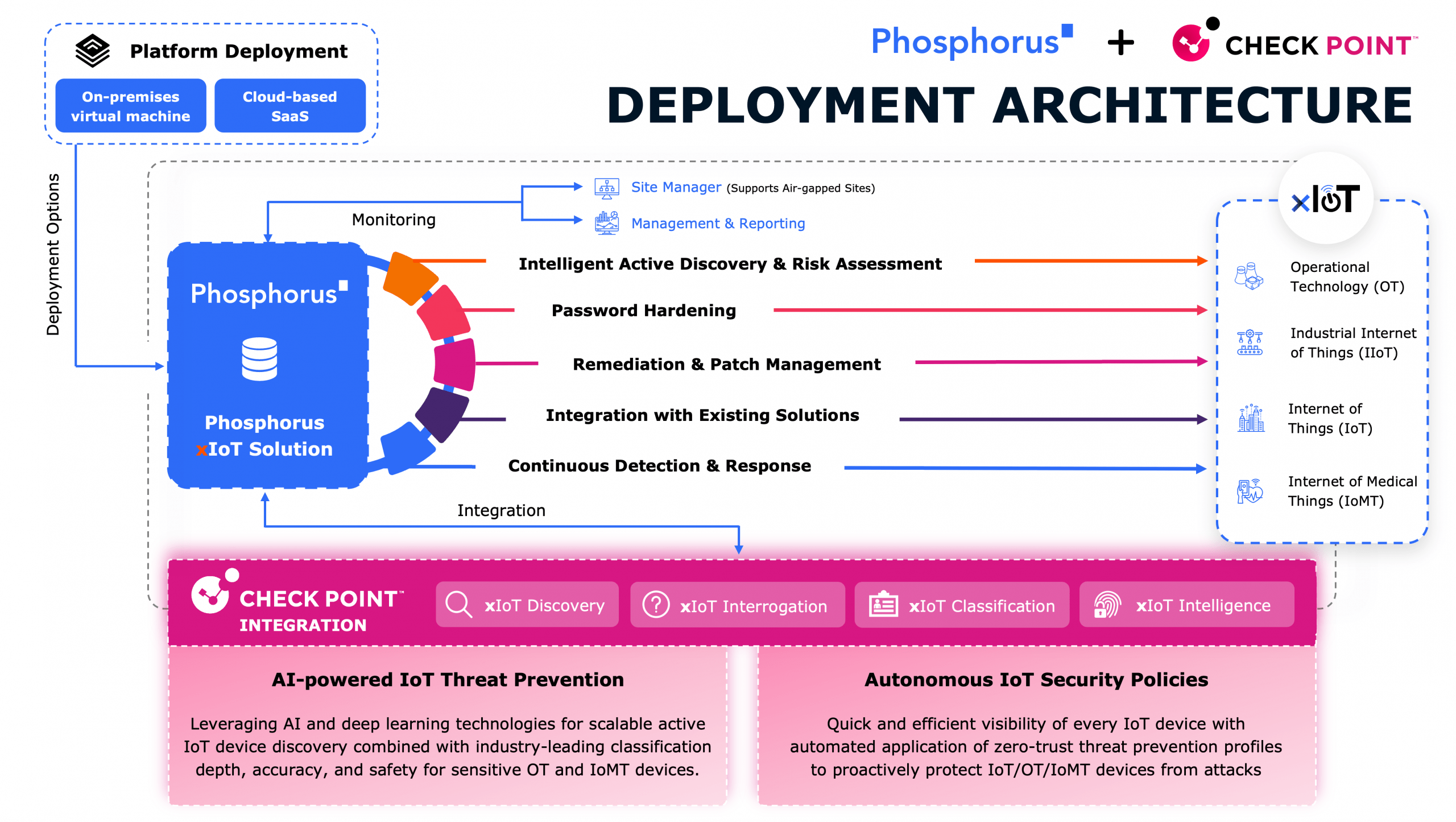
In this episode, host Eric Johansen welcomes Bill Lucas, Senior Director of Cybersecurity at Mastronardi Produce, to explore the evolving security challenges in agricultural IoT. With over sixteen years of experience across the automotive, healthcare, and tech industries, Bill brings a deep understanding of enterprise risk management, endpoint security, and cyber defense—now applied to one of the world’s most critical industries: food production.
Bill and Eric explore the unique cybersecurity risks in modern agriculture, from UV robots to robotic bees, and discuss how automation, sensor networks, and supply chain security play pivotal roles in securing these technologies. Bill also shares his personal career journey, offering valuable insights for professionals looking to strengthen their IoT security strategies.
Join us for a compelling conversation about the intersection of innovation and cybersecurity in the agricultural sector—and what it takes to secure the future of connected farming.
Transcript
Eric Johansen: Hello, everybody. This is the IoT Security Podcast. Hi, I’m Eric Johansson, global Director of Strategic Client Engineering, your host for today. And we have a fantastic guest for you guys today. His name is Bill Lucas. He’s a cybersecurity leader currently in the agricultural space. Bill Lucas is an information security leader with over 16 years of experience in protecting the digital assets and data of various organizations. He has worked in the automotive, healthcare, and tech sectors, where he has developed and implemented effective security strategies and solutions to address complex and evolving threats. Bill’s areas of expertise include endpoint security, application security, cyber defense, and enterprise risk management. Bill holds a, uh, master’s degree in information assurance with a focus on digital forensics, and he is a certified information systems security professional, cissp. Bill is passionate about staying abreast of the latest trends and innovations in the field of information security, and he enjoys sharing his knowledge and insights with others through speaking engagements, publications, and mentoring. Thank you, Bill, for being on the show today.
Bill Lucas: Yeah, Eric, thanks for having me. Senior director of cybersecurity and Mastronardi Produce. That’s the second kind of had a security role. Um, before that kind of. I started in healthcare, went into automotive, um, did a couple years consulting, which really gave me a breath of, from social media companies, airline, t even like glass companies, everything in between. Financial helped me see, like, across the nation, we all kind of have the same problems. And it was interesting to see how different, um, CISOs and leaders were tackling those problems. So, yeah, now, now at, uh, Mastronardi, they’re one of the largest distributors, um, and manufacturers of fresh, um, produce, you know, no pesticides. It’s, it’s ladybugs and, um, honeybees, um, flowing through the greenhouses. 1.2 million acres under greenhouse glass.
Eric Johansen: I’ve got some of your tomatoes upstairs in the kitchen. So I’m very familiar with you guys too. So.
Bill Lucas: Yeah, Sunset Queen of Greens. Um, very world. Lots of good products.
Eric Johansen: Awesome. You mentioned automotive, uh, and then now obviously you’re here on kind of more of the agricultural side. What have you seen? I guess if you take a look at kind of cybersecurity challenges, right. As a leader in that space and you’ve kind of Been in both of those arenas. You see a lot of big differences. Obviously when you talk about you know, automotive, your, your manufacturing, uh, you have a specific output and then you move to agricultural and you’re you know, working with kind of living things and plants and all of that is, is there what surprised you, I guess about moving it to the agricultural side from you know, some of the other stops in.
Bill Lucas: Your background, um, the different, because you’re right kind of manufacturing distributions, um, not unique. And it’s kind of the same across many industries. But what Mead Agricultural unique was kind of less PLCs and robotics to more like a UV robot going down the aisle to kill bacteria and the strawberry plants or like. Yeah, a lot of unique, like very specialized equipment for produce. Um, and, and that was kind of interesting. And why uh, Phosphorus kind of made on the radar was like how do I kind of inventory all these things, mitigate uh them and continuously monitor if the car part or like something happens, you can still ship that car part a week later, a month later, even a quarter later. You know, it’s not bad. And where produce it’s. It takes so long for that plant to grow, mature. And if, if something happens, you can’t ship that a week later. You can’t, you know, just put it on the shelf and say let’s get our operations back in order and then get it out there. So that was a bigger complexity to kind of wrap my head around. Um, and then understand that we need to keep this secure because it grows and you gotta wait the three months for that to regrow again, you know. So it um, can really have an impact on your business bottom line.
Eric Johansen: Has that led you to have more of a safety-first approach? I imagine when it comes to security, you kind of have to have a light touch.
Bill Lucas: Ah, 100%. Yeah. How do we monitor, upgrade firmware, rotate defaults, ensure people authorize the access but not be business interrupt like interrupting the business, um, is top of mind. It’s the same kind of processes, just a lot more unique types of devices uh that you need to secure.
Eric Johansen: And I mean one of the things I’ve noticed that’s I think been a newer IoT trend over the last like five to ten years, particularly in, in farming and agricultural is uh, a lot of utilization of sensors. Uh, for example, um, with you got. You talk about greenhouses, right? And like for me, you know, I think for anyone that even if you’re not a cybersecurity professional, you think about a greenhouse and it’s a Controlled environment, you know, to grow, whatever it may be. Is that something that you’ve been able to take advantage of, like, you know, probably 50 years ago? It, it’s eyeballing, uh, you know, thermometer. But, uh, is that, like, are you guys using those types of things heavily? And is that a, A digital component, like a Internet component for you guys? A network. Network aspect?
Bill Lucas: Yeah, 100%. Um, you know, it’s a lot more or than your traditional kind of H vac. It’s how much hydrogen is going into the plant, how much water controlling that, um, and then you nailed it too. It’s that attack surface where isn’t an outside vendor or supply chain. Um, managing that. Um, so you always kind of look at your ingress egress points, and IoT is that, um, a lot of the times. So being able to kind of just understand all those different types of equipment, whether it’s H vac, germination, um, other unique things to help the plant, um, through its life cycle, we need them to be on our radar.
Eric Johansen: One of the things I’ve noticed in my career is like, as I’ve been in different environments, which is one of the fun things about this job. And I, you know, for you, obviously, having a couple different stops in different types of arenas, whether it’s manufacturing or agricultural being deployed. And then, you know, there’s these moments where you find a device and you’re just like, I can’t believe that they made something like this. From a security perspective. So in my case, the one that always sticks out is finding, uh, a forklift that was controllable by a web browser, and obviously it required authentication. But it’s still just when you think about the safety component and someone using a web browser that directly leads you to the path of like, okay, this person on the web browser may not actually see what’s happening on the floor. And then you have real humans and other individuals that can be, you know, damaged or hurt. Uh, uh, from that. So I guess from that perspective, do you have any stories of, like, devices that you’ve encountered, whether it’s now or in the past, that you’re just kind of like your cyber security hat falls off, you know, because you’re so surprised.
Bill Lucas: Absolutely. I think anyone in the security community can kind of relate to you, kind of always joke that, how do you get off the grid? How do I just become a farmer? And then when you kind of realize how much tech is now there, know, from when we were kids, like, because you’re right, like John Deere and some of these companies, like the farmers in his living room, controlling everything with an iPad, like it just blows my mind. But I, from a shock value, I think, like pollination and maybe like robotic bees, things of that nature kind of was like, wow, that, that’s new. Or like amazing robotic bees.
Eric Johansen: Really?
Bill Lucas: Yeah. Wow.
Eric Johansen: Um, so tell, tell me more about that. So what is that like a, ah, are they essentially helping the hive better produce or something like that or.
Bill Lucas: Well, even if you can kind of automate the pollination, like you need to touch this and then touch this plant and touch this man. So something that can kind of just get that pollen, take it, fly it off to the next one, you know, like, um. So that was kind of interesting.
Eric Johansen: Now drones are out of the job, huh huh? In the bee kingdom.
Bill Lucas: Yeah, yeah, they just get smaller and smaller. Um, you know, and then kind of like from the risk perspective, kind of when you think this, this robot’s killing bacteria through UV going down the line, some advanced persistent threat or adversary takes advantage of it. Let’s just steer this, this way and take out seven rows or take down a greenhouse, like.
Eric Johansen: Right.
Bill Lucas: They’re, they’re different kind of considerations than I had in past kind of work experiences, like you said too.
Eric Johansen: I mean the fact that the process takes weeks or months, I mean you have one aberration and, and that’s, you know, game over.
Bill Lucas: Um, it was interesting to kind of see like how, you know, like Michigan 100% was the king of kind of creating the manufacturing line, but the manufacturing line for produce, you know, like a robot digs the hole, plants a seed, goes to the next piece, drops the seed in, covers the dirt, goes through the grow cycle, gets then chops a plant, if it can regrow, re put it through that cycle. Like the assembly line of that is kind of amazing.
Eric Johansen: Wow. Yeah. That is incredible. That’s another. Yeah, it’s just fascinating learning about how things are, are advancing. It’s, I kind of think about like the movie Blade Runner, the new versions, you know, where they show the futuristic farm and it’s like, we’re almost there, already there.
Bill Lucas: Uh, 100%.
Eric Johansen: One of the things that, that is always a challenge for any organization, whatever they’re in is, is obviously understanding what you have. Right? Uh, and IoT in particular is a tricky one because they’re purpose built. So a lot of people, they have a problem, they go and they try to solve it and they take care of that problem. And it might be an IoT device or what have you kind of like 25 years ago, our worry in cybersecurity would be people grabbing routers and doing a quick wireless connection. In your business, is ownership of devices hard to determine or do you have a really good line of sight who owns it so you can work with them to try to get it resolved if there’s any issues?
Bill Lucas: Um, I think it’s a problem holistically. Um, technology is always the easy part. It’s who owns it, who’s responsible for it, um, where instead of a ah, plant, it’s a farm. Um, um, so, so you do have kind of engineers and people responsible at that level that you know that you can have those conversations with and, and work with as you’re remediating things. Um, so I wouldn’t say it’s a big challenge, um, for us, but it, but it is a holistic challenge, you know, as you kind of. Because you’re right, traditional security was a on prem perimeter edr maybe you know, like you can, you know who to talk to. And there’s departments for each of these things where when you kind of dealing with somebody that isn’t always on a laptop, isn’t always connected, might not be. They’re used to growing plants like they’re not ready to have that kind of conversation. Um, and how do you handle that?
Eric Johansen: Yeah, those devices in the field, which again is, is the other side of risk that, you know, traditionally in cyber security, it’s like you’re trying to contain your risk around the physical access. Well then the nature of IoT is you’re putting these devices in places that are not necessarily within four walls because you’re in a field or what have you. You had mentioned kind of automation sounds like that’s been a big part, uh, in terms of production at a lot of your roles, you know, now and in the past. Where do you see automation? It sounds like automation is pretty heavy, like with you guys today. So how does that balance like with like, are you, are you primarily greenhouse or do you actually have like fields where there’s workers grabbing or does it become very much automated?
Bill Lucas: Yeah, like, uh, we’re so we’re fourth generation over 70 years. Um, the original owner pioneered the greenhouses in um, Canada and North America. So like it. That is our business, like growing with angry analysis.
Eric Johansen: Yeah. Oh, I see. So it’s only greenhouses and then so 20 years ago you may have had, you know, in one greenhouse, 20 or 30 people. And now is it fairly like robotic? Have you seen kind of an optimization in that space or how does that look kind of from the past to the current as far as how, how things are produced and uh, through the line.
Bill Lucas: Yeah. I think, you know, the metrics and measuring and consistency, it’s much more scientific. It’s much more like, you know, exactly how much hydrogen, when to pull back, exactly when to water. Um, and when you think of like 1.2 million acres, but then it’s horizontal too, you know, like these things go up. Tomato plants buying goes up 30ft, you know, down this massive aisle. There’s a lot there, you know.
Eric Johansen: Yeah. Like, how long have you been at your current role?
Bill Lucas: Um, I’ve been here just over a year.
Eric Johansen: Okay, awesome. So what has kind of been, you know, there’s always that those first few months, right, where you’re kind of trying to get your arms around what you’re working with. Um, can you tell us a little about a bit about that journey? Was it a situation where, you know, you came in and there was just kind of your expertise and experience needed, or did you have to come in and there were a lot of, you know, things you had to enact or kind of are the things you could do, talk about around that.
Bill Lucas: Um, you know, in coming from consulting, it kind of preps you for how to tackle a new business. But, you know, the first priority is kind of pick a framework, do an assessment, understand your gaps, prioritize those gaps, create a three-year roadmap. That’s where, you know, when you think Phosphorus. We had a, we were pretty good maturity on a lot of things, but when you take it to the next level, it’s that supply chain, it’s the IoT, it’s, yeah, we have phenomenal EDR. Yeah, we have sim, we do all these other things. But let’s start tackling this risk over here, you know, um, so that I very methodically went through and prioritized, um, the gaps. And when it came time to kind of tackling the IoT challenge, you know, we vetted a few companies against each other and um, Phosphorus is the clear winner for a couple reasons. Not having to deploy something at every switch, at every distribution center or farm, um, to get that instant visibility. But also another differentiator was the ability to remediate. Uh, you know, there’s so many tools that just identify and great, now who’s going to go do the work or who do you hand that off to? To where I can update the firmware within the platform, I can rotate the credentials within that platform, and then the continuous monitoring. What Made it important from agricultural standpoint is we have 500 different varieties under R and D. And potentially you could have. Because there’s so few companies in this tech. How many companies are making UV robots? You know, Mm. You can have a competitor, A and B, doing QCs close to each other. How do you ensure this one didn’t put an access point in the other one’s segmented network and trying to get proprietary information because they were trying to steal that business. So like that continuous monitoring was key for us to detect new devices, understand what’s truly in our farms, what’s truly in our R and D facilities, um, and keep it secure.
Eric Johansen: I think one of the challenges from a cyber leadership perspective is always talking to the business and getting them to understand the risk at hand and not, you know, talking specifically about where you are, where you have been, but kind of what your experience and expertise, what are your strategies about, you know, potentially talking to, you know, everyone says the board, right. Let’s just use the board. Right. And they don’t necessarily understand the risk profile and the attack surface that may be out there, but kind of what’s your style and methodology for helping communicate, uh, a technical challenge that really can affect the business to leadership to, to get, you know, what you need to help mitigate risk.
Bill Lucas: One of the strategies and you. When you think kind of 10, 15 years ago, security was the big no like business function. Like, nope, can’t do that, can’t do that. So it’s, it’s, it’s not. No, it’s how can we do it securely? Um, and when it comes from a executive leadership or board conversation, it’s here are, here are the three options or here, here’s option and the pros and cons and let’s come to consensus and let’s run with it. Um, you know, where I’m at, they understand what a loss of a greenhouse can impact the business or, you know, whether it’s ransomware or tornado or hurricane or whatever. Um, the risk hasn’t been the challenge. It’s. It’s kind of because you have, you have business needs. The business needs to do certain things. And I can’t be the. No, we can’t do that. It’s. Here’s. Here’s a couple ways we can do this and securely, you know, and like, let’s have that conversation on. Maybe we can accept a few of these risk on option P. But still. Or that gets us to an acceptable risk level. Um, but still. Yeah, reduces it, you know, like gotcha.
Eric Johansen: Yeah. And like you were talking earlier about the remediation component within Phosphorus bringing a lot of value when you start. Like usually when I’ve been involved with deployment, integration of our platform, uh, a lot of times it becomes okay, now we’ve discovered everything and we’re aware of the risk, now we have to go to these groups. Um, like in traditional can be easier, right? You’ve got the physical security team and they own the cameras and door controllers and you’ve got the IT team that has the IP phones and the printers. But from your perspective in your chair, what were some of like the business owners of these devices that you had to go to to get permission to make changes? Or is it the other side where you’re like able to have essentially carte blanche?
Bill Lucas: No, it’s definitely not the latter. Um, and you know the key people and um, who are in charge of like the farms overall and, and you know, even as we rolled out Phosphorus as like let’s do this farm because you know there’s the most unique devices there and let’s slow then this device, this farm, this farm, this farm, this farm. And then once you kind of get to a level, okay, now I can go everywhere. Um, so like big believer in that strategy. Kind of think big, start small, scale fast. Like you can overcome some objections like well that’s going to bring the bandwidth down or that’s going to do this or I, I don’t want this to happen and well let’s just try it here and then see that it’s not a fact. Well now let’s do it here, you know. And that process has helped bring new security innovation kind of in um, I’m not sure. I think I totally understand your question. I don’t, we don’t definitely don’t have the freedom and because you don’t want to take a site down or farm down and it’d be your bulk as you were testing some tool or made some wrong misconfiguration. So there’s definitely, you know, very clear we’re doing this at this time, this is how we can roll it back. Um, are you comfortable with it and working with them on this is a peak night or like let’s not do it today. Um, yeah, so, so there is a lot of coordination and um, communication. I guess I can’t speak to the challenge of not knowing who to talk to. That’s not a problem. It’s just, just do it.
Eric Johansen: You know, I mean I guess the what I’ve seen and yeah, or maybe I didn’t Phrase it, uh, correctly, but it was kind of like a lot of times when we talk to organizations or we’re working with them, the past methodology before Phosphorus, for example, is, you know, I’m going to have to manually update these things or I’m going to have to change these credentials or just not do anything. Right. And uh, particularly with manufacturing and agriculture and businesses like that, these devices are now becoming increasingly important as part of the output, uh, from the business. And so I guess the general thought is like, oh, are they happy that there’s someone that can help them at scale with some automation? Or is it more of, you know, hey, we’ve got this in a DMZ and there’s other mitigations, so we’re not as worried about it or kind of, you know, what did you experience? You know, kind of any relief or, you know, because what I’ve a classic story that we hear is, you know, there’s someone using a script or there’s someone just swivel sharing and making changes. Um, you know, that level of automation can really optimize similar to what’s happening in some of your greenhouses.
Bill Lucas: I think for me it was, um, in this environment they were going to do what they were going to do with or without security. Um, and it was more of a, and it was always, you know, when I started it was, hey, the vendor can’t connect to this. What is it? Or had, uh, no idea we were doing that, um, to opening that door or let me show you how to do this. More security. Let’s put on a separate vlan. Let’s do this, let’s do that, let’s, you know, um, and this gives me the visibility to see stuff before it’s like that last minute, the vendor is coming tomorrow and they want, they want to configure this. You’ve had it there for months but had no idea either way, you know, so. And I guess it kind of answers like the previous question. It wasn’t, they’re going to do what they need to do regardless. This is me helping to get a little more visibility and then showing the secure way to kind of do some of these things, you know. Right.
Eric Johansen: Makes sense. And along those lines, um, are there, I guess what keeps you awake at night today? Like, are there emerging threats or, you know, new technologies and innovations in your space that are, you know, what you’re looking forward to? Because obviously you have the now, you have the past. And then someone like you and your role, you’re, you’re, you have to be Always looking forward. Is there kind of, I guess what gives you heartburn or concern today if you’re, you’re, you’re thinking towards the future?
Bill Lucas: Um, um, I would say the one that’s given me the most right now is AI and very beneficial. Can make the businesses life very easy and automate a lot of stuff and help speed up a lot of processes. The challenges are when you think shadow, like shadow it. So AI and cloud, like if you say no, I’m just gonna fire up my own C2 instance in AWS and build it out anyways or I’m just gonna send the data out to an AI that’s not your tenant and have it tell me the answer. So leaning more on the AI, it’s, it’s this data egress that, that scares me and wrangling that and um, because it’s, it’s a delicate conversation. Well this, this has helped me do my job um, better and more efficiently. So you have to point them like, well here, here’s the, the, here’s the AI, ah, that we have in our enterprise. Um, or let me point you to a more secure way to do that. It’s always been insecure, you know, when you think it’s from a SIM and user behavior analytics and what email gateways do and DNS gateways. AI has always been there. It’s the pre-trained transformation that’s just became so mainstream that now everyone’s just hey, compare these two documents. Hey, do this for me. Hey Data. Yeah, yeah, that, that’s been a big initiative kind of data production, um, and has me worried.
Eric Johansen: How have you like, I guess from when I look at, when you look at like your team structure, are you, you guys have like a OT or IoT security expert or is that kind of you or where are you looking kind of forward as far as like managing the challenge of IoT security? Is that a current role for you or is it a role that will be dedicated or kind of. How do you look at that?
Bill Lucas: Would love to have a dedicated role. Um, the reality is, you know, there’s only so many employees in the whole enterprise and only so many employees in security. Um, it’s kind of living within the SOC team from a detect respond, um, kind of piece right now. Um, you know, from working at companies with 200,000 people or even consulting on ones at 300,000. You had security teams bigger than our IT department, you know, like, but it’s a different world. You wear multiple hats, you know, when you’re not a smaller business.
Eric Johansen: Yeah, and then so like as a smaller business, you mentioned a Soc. Uh, you guys must have like a relatively like 247 type scenario. Are you using Phosphorus data to kind of enrich asset knowledge and tying that in with other components or kind of. How is, how is that looked at? Like, if you don’t necessarily have a dedicated person that’s in charge of the business relationship and kind of the daily running is it. It’s kind of a SOC function then?
Bill Lucas: Um, Yeah, I mean we are 247 managed techno response and then internal SOC to work on things like this. You know, where there’s a lot of. And MDRs can’t just update the firmware, they can’t do things. You know, like you need that human interaction to kind of have those conversations.
Eric Johansen: Uh, Bill, you’ve been in your own journey with IoT security and you’re, you’re kind of on it now. Um, a lot more mature than a lot of other organizations. Um, because at least what we’re seeing as an organization, there’s a lot of companies out there that are kind of not doing much. Um, so like, if you’re like looking forward and giving advice as uh, someone that’s kind of been down this path at a couple different uh, stops on the way, what would you recommend that organizations prioritize when they’re looking at this IoT and OT side of the house? Uh, as far as like security measures and everything that they should be doing to be secure and have an agile.
Bill Lucas: Approach from a SNP perspective. Pick a framework, start building your security program, start knowing what your gaps are, work to close those. Um, CMC has been 10 years kind of. And will it ever happen? I heard just recently like the government finally did approve some of that stuff and I previous role, you know, uploaded perfect score to spurs and you were just waiting. Um, now this is actually getting finalized and getting pushed. Part of that is look at your supply chain and every company that’s probably listening is some either is tied to the supply chain. Either you have a ton coming to you or you’re supplying someone else. So at some point through those layers, the government will demand you have a basic level of security hygiene and um, so, so that’s kind of the advice. Get the framework. You, uh, know even if you start at CIS controls and top 20 then you kind of mature to ISO 2700 and then you kind of matured in this CSF and then maybe special publication 800 171. It’s a journey but like start there because it will be required soon. To be able to prove that?
Eric Johansen: Absolutely. Do you have any, I guess, horror stories in your career around a device? You know, I think with IoT and OT, everyone kind of points to Stuxnet as, as one of the big moments. Another one of course is just, you know, the pandemic. Right. We were all kind of shifting very quickly. We all realize, you know, the importance of things like toilet paper that we never thought of before. Uh, is there any particular, uh, device horror story from your past? Um, obviously that you can obfuscate and make anonymous, but uh, any interesting along those lines?
Bill Lucas: Not that I can think of right off the top of my head. Um, I’m sure there’s one out there. I just can’t. There’s been some interesting things, but um.
Eric Johansen: Maybe nothing you can share. We, Yeah, I, I would. You know, one of the, one of this, like. So when I mentioned earlier, we got sent on some deployments and IP cameras is kind of uh, an area that is very interesting. You know, these devices are um, as you can imagine, high horsepower. And you know, you’re talking about a earlier. You know, a lot of them are now starting to have like facial recognition technologies and, and things like that in them. And particularly around manufacturing, you know, you have um, sometimes, uh, folks from all walks of life. And so there’s an organization we were working with uh, a year ago or so and they were actually having problems when. This is kind of around the time where the FCC, uh, put that ban on some of these Chinese manufacturers. And uh, a lot of the reasoning behind that ban for those companies was because they were essentially assisting Beijing with exfiltrating data from their devices. And so one particular client, uh, of ours, they actually had, people would show up to work one day and they just wouldn’t be there in the days after. And so that’s one area where I’ve been, you know, really passionate around IP cameras because I think a lot of us, like you think about the common risks, right? And we’ve all heard stories, you know, where there’s a hacked IP camera in legal, uh, counsel’s desk, uh, or, or environment. And, and you know, people can. It’s essentially like a wiretap that you deploy. Like it’s for your security, but if someone could get access to it, you know, there’s all these different additional layers of, of information that can be gathered even before you start thinking about this device and its power. And if you can own the device, then you essentially have a Linux machine that can utilize uh, as well. So um, that was at least One that was most interesting to me because I think all of us, like, we live in this world. You walk around and I can see three cameras right now, just. And obviously I’m a geek, but it’s like, you know, there’s, it’s like they’re just there and we just kind of take them for granted. And uh, that’s at least some area that I just see, like, unlimited potential for challenges, you know, especially with the amount that’s out there.
Bill Lucas: Uh, 100, like all those movies kind of come to mind, you know, like, it’s scary. Data is king and how is it being gathered, you know, and the privacy concerns and that’s a whole ‘nother podcast.
Eric Johansen: Exactly. Yeah. Um, you mentioned you guys are, you know, uh, you’re not a 200,000 person company. So I guess with that, do you have, like, is there advice you can give or, or do you have a program you can talk about with interns or anything like that that kind of would help people that may be listening that are interested in getting into this field or. Um, like you mentioned, AI Obviously there’s a big, big future looking concern, uh, for organizations, uh, which obviously would likely provide a lot of employment opportunities today and tomorrow. Um, but any kind of like, advice, uh, for, for budding security professionals.
Bill Lucas: That’s m. A good question. Definitely start listening security podcasts. There’s tons of them out there. Security now. Um, great security debate. Um, I mean, there’s just so many plethoras and maybe you don’t have a degree in cybersecurity or it’s kind of a budding passion right now, but listening to those weekly daily will open your mind to like, other possibilities. What’s the risk? How are people handling it? And then you decide, yeah, this is something I want. I want to get a degree in it or I want to get a job in it. But, uh, I would start there. Makes the commute go by really quick and easy. You know, I usually put it on 1.2 or 1.5 speed and you need room, you know.
Eric Johansen: How did you start in your career, Bill? Did you. Were you always going to be in cyber or did you kind of, uh, diverge or, you know, what was that like for you?
Bill Lucas: I really wanted to be electrical engineer. And like, I love like taking apart things and putting things back about there. And I was totally like geek at like healing me on lasers. 30,000 volt shockers, Ian Ray guns. Like, wow, those are like the things I asked for when I was like 12, you know, like, um, selling uh, wireless mics, you know, that you could tune in on a frequency. And I would sell them at school as like spy devices, you know, like, hey, find your parents. You have this. Ah. But then that kind of mindset of like taking things of our understanding really leads you into that hacking kind of mindset.
Eric Johansen: Yeah.
Bill Lucas: Um, and then started taking degrees in it. Then you take quite a few ethical classes and then you realize, okay, let’s not be. Let’s maybe help prevent this, you know? And that’s when security kind of all came together. But, uh, yeah.
Eric Johansen: Did you start out and kind of, uh, were you. So then were you an electric electrical engineer starting out or did you get into.
Bill Lucas: I know I took classes. Like we were designing the motherboard and all the different layers and they had a lot of fun there in there. But yeah, security just took
00:35:00
Bill Lucas: over.
Eric Johansen: Yeah. Yeah. Oh, uh, it’s awesome.
Bill Lucas: Yeah.
Eric Johansen: I mean, I, I’m. I personally came up via an internship and so I’m a big fan of those. You know, it just gives you that opportunity to get in with an organization while you’re going to school and studying, you know, that component. And then, you know, they get to know you as an individual. Because, you know, one of the things you hear today is there’s just so much competition and, and how do you stand out? And, and nothing stands out like a relationship and, and, and being there and being a known person that they think, oh, yeah, this, this person does a lot of good work and you have an opportunity that, you know, that comes from that. Do you guys do, you know, like, like here in Phosphorus. We’re lucky to be headquartered in Nashville, so we have like, programs with band, Vanderbilt and stuff like that, which is, which is great. You know, like a lot of brilliant people coming in and out. Um, you guys have like a similar program or something that you’ve thought about?
Bill Lucas: No. 100%. We do internships and we’ve already been kind of stacking who will be the security ones for the summer. Um, and last year, not in the security team, but some other teams, you know, they became full time employees and, and you’re right. And you kind of nailed the challenge with work from home for a young person. Like, there’s so much power and just like, I didn’t know we did that. Like, oh, what’s that? You know, and like, yeah, you just need that visibility and networking and talking to people and understanding what’s behind the business. Um, you know, arguably when you get to a certain age, work from home works because you have that foundation. But we need to give back to that next generation. Um, it’s hard to pick that stuff up when you’re not in office, you know.
Eric Johansen: Yeah, it is. Interesting. I mean, uh, you mentioned kind of going to school and, and all of that, and obviously very, very important. But you also, in the same breath, we’re talking about, you know, electric and electrical engineer. And even prior to that, tearing stuff apart, breaking it. I mean, that was one of the ways I learned so much. And I think that’s what, you know, I’m into IoT because, like these, you know, when I, when I was a teenager and I broke my dad’s Mac, he was a little more mad than, uh. Now if I, if I break, you know, a little IoT device. And, and that’s one of the things that’s funny is I’ve had people tell me like, well, we’re not worried about those because they’re like 30 bucks each. And it’s like, well, yeah, that’s the whole thing. They’re 30 bucks each. You’ve got 500 of them on your network. If somebody pops one, it’s got the ability to exfiltrate data. Like, it’s. It’s still a very powerful device. And so it’s kind of. Kind of. What’s amazing now is, is just really IoT is not printers and cameras, like we’ve always thought. It’s anything that has firmware and IP address. And that is just changing so much. I mean, even today, learning from you, like the types of things that are part of your production, it’s like, I mean, those are all new things I had no idea about. And it’s just fascinating. Like, we could go and talk to people in other companies and have those same realizations probably every day for two years as far as all these devices that are coming online and, uh, the farm automation and all that. So it’s pretty incredible.
Bill Lucas: And you kind of nailed it too. Because even though. And I feel like this says it doesn’t matter. It’s just doing this one thing. It’s just this device. But is it writing data back in your erp? Is it writing back data to a data warehouse for KPIs or metrics like that lateral movement is what makes these devices scary. You know, what else is it connected to? It’s just supposed to measure the temperature, but is it dropping that data here? That also connects to here.
Eric Johansen: I have a buddy who’s in manufacturing, and I heard a horror story from him. Is they. We were talking about sensors and monitoring, like, very, very Important for. For everywhere, right? I mean, we even. I think, you know, I know. I don’t know about you, but I have, you know, temperature sensors in my house for various rooms, especially for my young kids, because I don’t want my, you know, I want them to be comfortable and not wake up in the middle of the night and, uh, you know, so all that good stuff. But he was. They were working with a smaller company that did collected metrics with these little boxes, and I actually have one in the other room because he just sent it to me, you know, like, it’s like I’m not working with them anymore. But he was. Long story short, he was getting a demo from these guys, and they were bopping in between all this customer data without any obfuscation, without any segmentation, without. I mean, that’s really kind of going off of what you just mentioned, where it’s like these little devices, they collect a data. Data point. And so, like, for example, I have a sensor. It’s a US Company called Sensor Push. And I have that upstairs, uh, in my son’s room. And it just collects. Every really 30 seconds, it collects the current temperature, the, uh, barometric pressure, things like that. But it aggregates all that data and it shares it out and. And, you know, so there’s that risk factor with your data, depending on what it is. And in my home, the risk factors is lower. But if I’m a manufacturer and someone can understand that yesterday, and I’m a
00:40:00
Eric Johansen: meat company, all of a sudden my freezers were, you know, 45 degrees, then that might be a concern, you know, so it’s just all these different kind of layers that come from, you know, you’re the product, you know, in a lot of ways.
Bill Lucas: So, I mean, what’s scary, too, is the, uh, mergers and acquisitions. Like, you. Like a company, they’re doing things securely, but then a big company buys it out, and now is it still secure? You know, like, it is super scary. Um, and we see it all the time. Like, I used to. Well, yeah, I won’t get that example. But, yeah, it’s scary.
Eric Johansen: The security guy mindset, you’re like, oh, I have this story. And I’m like, oh, wait, I can’t. I can’t quite share that. So, uh, any closing thoughts or any, you know, nuggets of wisdom? Whether it’s IoT or, you know, we’ve talked about careers, we’ve talked about risks in the future. Any other items that you think, you know, you want to share or talk about at this stage.
Bill Lucas: I um, mean, if you’re, if you’re struggling to understand your threat landscape, um, with non standard devices, you know, I highly recommend giving Phosphorus a call. Um, if you, if you know your subnets. And um, it’s amazing how quickly you can get the visibility and instantly you’ll know, you’ll see the value. And only warning is, yeah, that there’ll be some work behind that. But we can’t hide behind. Ignorance is bliss, you know?
Eric Johansen: Yeah, exactly. Well, and even if you don’t know your subnets, one of the, the crazy things is I’ve actually had clients that they’ll do large scans like slash 16, slash 8, and then they’re finding subnets they didn’t even know they had. Like, because some organizations, they have partners, partnerships with other companies and stuff like that. And so sometimes that segmentation isn’t what you thought. So there’s some things you can find there, like cameras hanging out where they shouldn’t be and all of that. So it’s, it’s pretty incredible because, you know, like we talked about earlier, these devices are purpose built. They’re doing something, somebody needed it and they put it out there. And that somebody that deployed it isn’t always the person that managed it and it, and usually is not the person that has to secure it. So there’s always all these people that are, uh, kind of involved in that scenario.
Bill Lucas: So, uh, 100%. No. I really appreciate you having me. Um, I’ve really enjoyed kind of utilizing Phosphorus and excited to grow with you guys and get secure, stay secure.
Eric Johansen: Thanks again, Bill, and thank you for watching. The IoT Security Podcast is brought to you by Phosphorus, the leading provider of, uh, proactive, unified security management for the extended Internet of things. I’m Eric Johansen and we’ll be back again next time with the IoT Security Podcast.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.