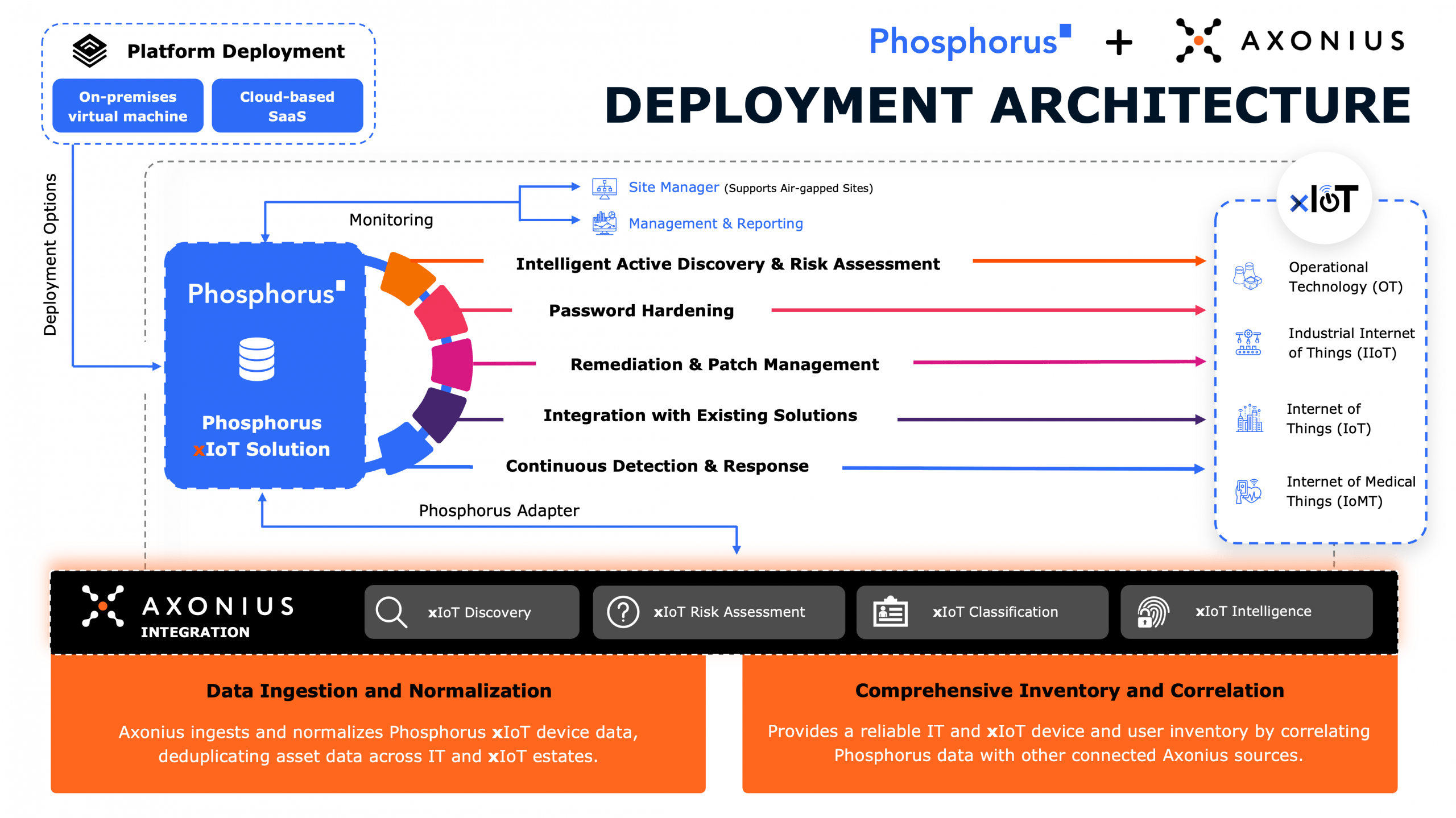
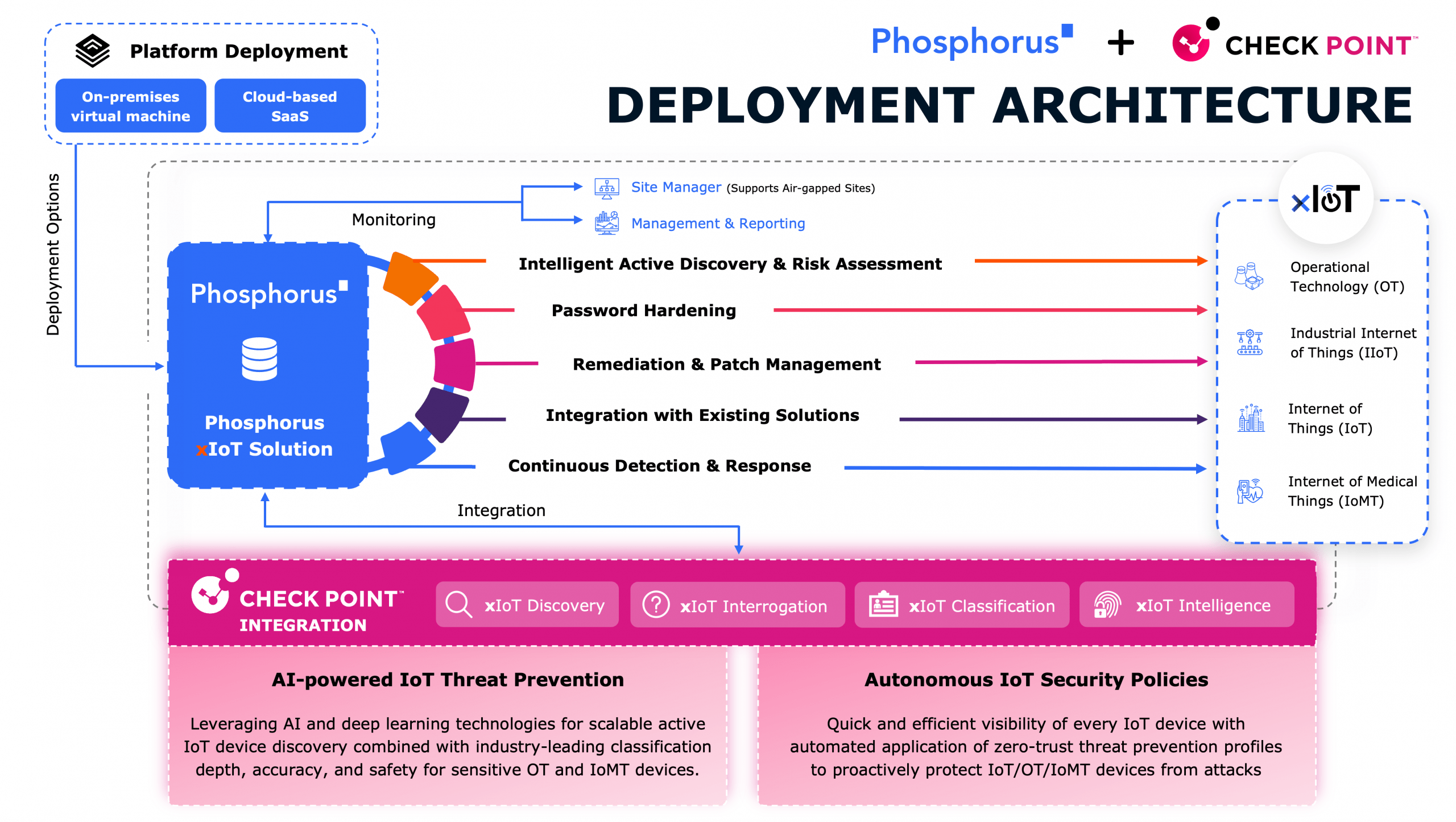
2025 will bring a new wave of OT malware that’s more sophisticated, scalable, and financially motivated than ever before. Threats like FrostyGoop, Fuxnet, and Volt Typhoon’s KV-Botnet are setting new precedents for OT malware as attackers integrate deeper knowledge of OT/ICS systems. While nation-states have traditionally dominated this space, ransomware gangs and other financially motivated actors are now increasing their focus on OT endpoints. We’re seeing a shift towards attacks that exploit native OT device functions—making them more scalable, adaptable, and harder to defend against.
And yet, regulatory efforts continue to lag behind. While initiatives like the UK’s PSTI Act and the US Cyber Trust Mark make progress, they focus almost entirely on consumer IoT—not the mission-critical OT devices (PLCs, HMIs, RTUs, SCADA) that power industrial environments. That leaves a massive gap in security, one that attackers are all too ready to exploit.
The reality is clear: OT security hygiene isn’t keeping pace with the threat landscape. Many OT systems still lack fundamental protections—default passwords remain unchanged, firmware is outdated, and insecure protocols are widely used. Adversaries are learning these environments faster than defenders are securing them, and that gap is only widening.
Read what Phosphorus experts and many others in OT security have to say about what 2025 may bring in this article from SecurityWeek.