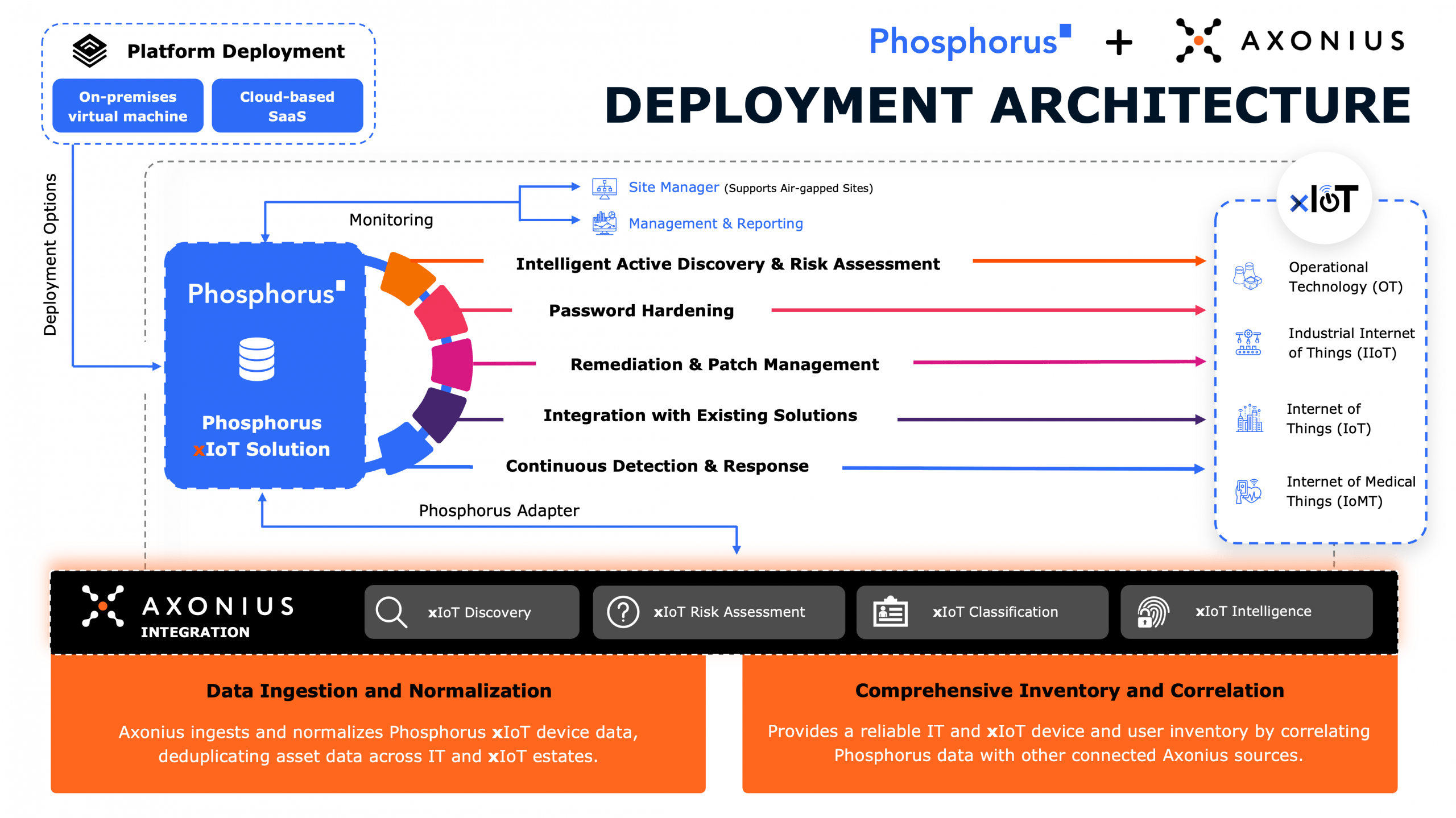
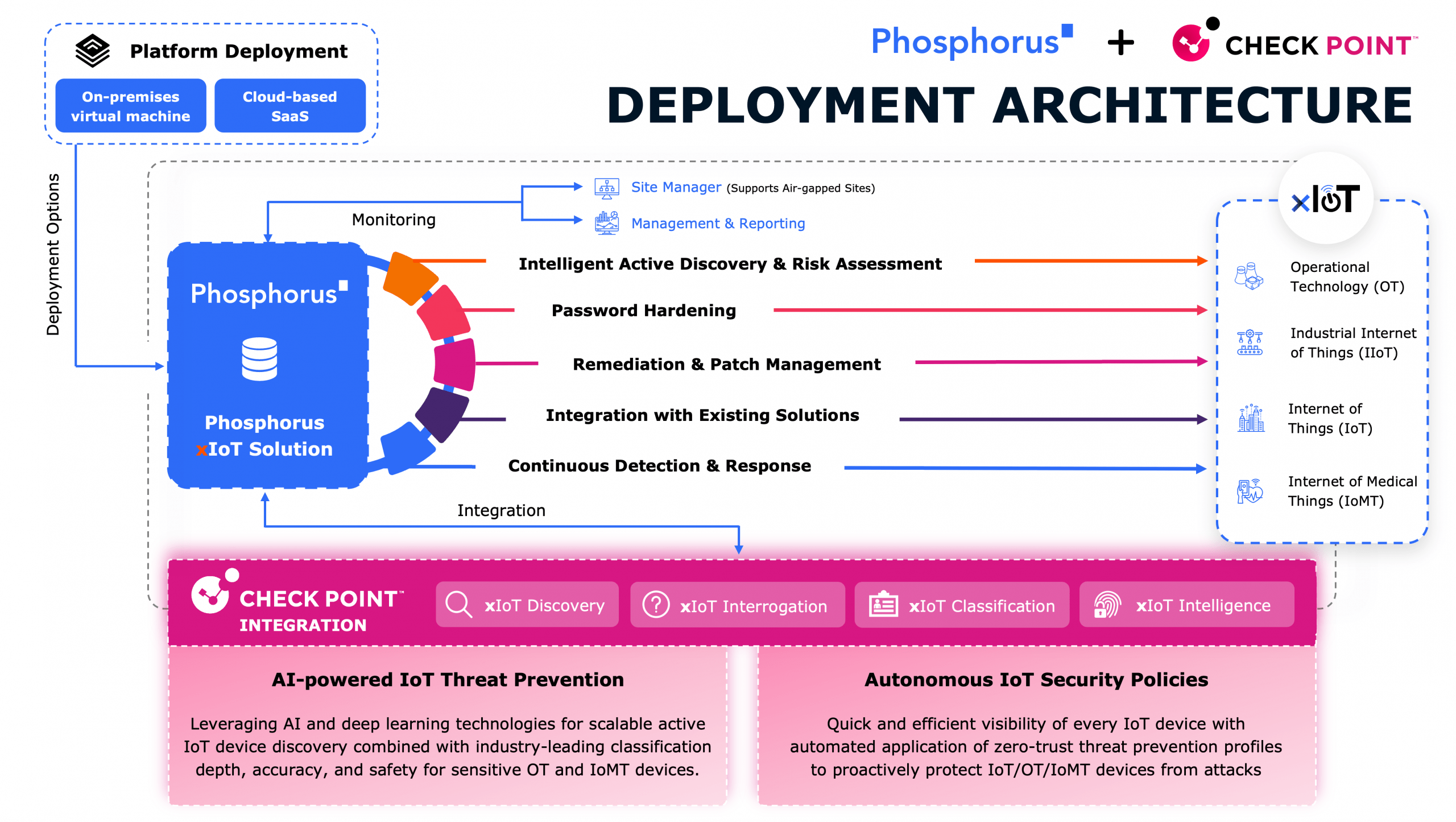
Steve Lodin, a veteran of the cybersecurity industry, embarks on an ambitious mission to protect millions of identities from hackers while his team strives to maintain high-security standards and compliance with regulators.
“The more that we can identify, document, and share, the less attacks that are hitting our colleagues and our peers in the industry.” – Steve Lodin
Lodin’s experience comes with a background in software engineering, system administration, and global IT security. He has worked with General Motors, Ernst and Young, Roche Diagnostics, and Sallie Mae, and has a Master’s degree in Computer Science from Purdue University.
Steve Lodin had been working with electronics engineering and software engineering since he got his engineering degree. He had a passion for computers and decided to focus on security. He went back to school for a Master’s in Computer Science and went on to work at Ernst and Young, Roche Diagnostics, and the world of startups. For the past 10 years, he has been working at Sallie Mae protecting millions of IDs from hackers. With the shift to the cloud, Steve has been advocating for the removal of legacy security debt and providing security opportunities to improve the environment. He is a prominent contributor to the industry, helping to identify and document attacks to protect against them.
In this episode, you will learn the following:
1. What challenges arise when attempting to secure xIoT devices?
2. How can organizations prevent external and internal attack surfaces?
3. How can organizations use the cloud to reduce their legacy security debt?
John Vecchi:
Hello everybody. You’re listening to the IoT Security Podcast live on Phosphorus Radio. I’m John Vecchi.
Brian Contos:
And I’m Brian Contos. And we have an amazing guest today. We have Steve Lodin. Steve, how are ya?
Steve Lodin:
Doing great. Good to talk with you again, Brian.
Brian Contos:
You know, Steve, I can’t remember how many times we’ve done podcasts together. I was trying to think back this morning, but it’s got to be at least three, four times right, over the last couple years?
Steve Lodin:
Oh yeah, definitely.
Brian Contos:
Yeah. And you have a great background, sort of how you came up through cybersecurity and how your career has progressed and the things that you’re doing now, I know you wear so many hats. I was wondering could you take a few moments and just kind of share with our listeners sort of your journey and what it is you actually do today?
Steve Lodin:
Sure. Well, you can’t really tell because this is radio, but I got a gray beard, so I’ve been around a little bit. I started off with an engineering degree, electrical electronics engineering, software engineering was my key. I worked for General Motors and developed concept car vehicle displays, so a head up display, something that made the elderly see better, those types of concepts. While I was managing to do software, I decided that I liked working on the computers just as much. Ended up managing a global Unix environment for some of the General Motors divisions to basically write software.
In that pivot into system administration, I realized that security was a big deal, watching the Morris Worm and other things happen out there I focused on security and got what was called a GM fellowship. I went back to school for a master’s degree in computer science and they paid my salary half and paid all my tuition. Excellent deal, learned so much going back to school, getting a master’s degree. I went to Purdue University under Professor Gene Stafford, Staff as he’s known by everybody. And since then, since the mid ’90s, I’ve been really focused on security. I basically did some consulting at [inaudible 00:02:38] Young, the same time George Kurtz, who runs CrowdStrike, was there. Lots of incredible people working at [inaudible 00:02:45] Young doing consulting. I then followed up by starting up the global IT security team for Roche Diagnostics in Europe, lived in Europe for three years.
Again, met some incredible security people in Europe that have handles that would be names you would know off the top, like FX and Max and all of these guys that are still in the security field today. After doing that, I spent a little bit of time with a startup. We started a company here in Indianapolis, four of us we’re founders, it’s still running strong, doing a great job. They’re focusing on MDR and the SOC data center side. But for the past 10 years I’ve been at Sal Mae. I have been protecting millions of IDs of borrowers and co borrowers from the hackers. And knock on wood, we haven’t had any breaches and we’ve had very few compromised accounts or IDs. So doing a great job there, really enjoying it, I’ve got a great mentor that’s keeping me involved in the community. And today I’m running the cybersecurity operations team, endpoint protection, network protection, secure web gateways, threat and vulnerability management. And then I’m also running the IM team, centralized identity access certifications, all under strong regulatory management, our friends there are the FDIC.
Brian Contos:
Wow. Wow. When I said at the beginning, you do a lot of things there, you wear so many hats and you have worn so many hats there. Just that Sallie Mae, which I think is just amazing I mean, your roles and responsibilities, I don’t think even how you explained it, people grasp how much you’re actually responsible for there, but it’s pretty great. And I didn’t know you went all the way back to Morris Worm. I haven’t actually heard that mentioned in a while. I think a lot of our listeners that go way back, remember his dad worked for the NSA, right?
Steve Lodin:
Yeah, he did. And little slippage on coding there that caused most of the internet at the time to go down.
Brian Contos:
I think it will infect maybe a dozen computers. Wake up in the morning, oops, every computer. And I was using mostly finger in our commands, I think way back then. Yeah.
Steve Lodin:
And the driver there for me was SPA’s response on what actually happened, drove me to follow him even closer. He was only, I don’t know, 40 minutes away from where I worked. So that was a key driver for me, and I ended up learning so much under him and I actually back in the day before CVEs were the vulnerability, I had a US cert vulnerability 96.02. That basically was my research on the random number generator in [inaudible 00:05:55]. They had gone from [inaudible 00:05:57] version four to version five, but they continued to use the version four, random number generator that had about 20 bits of entropy. So it was real easy to break even back in those days with slow computers.
John Vecchi:
Wow. Steve. So man, I mean, you covered so many things that you’re focused on. It’s like if you look at this new kind of area of security we call XTR today, which includes all these things, and a lot of the things you mentioned are kind of within the context of that. And so I’d love to get into all those various areas of security that you addressed, but what’s your team look like? Are they distributed mean? How is your team built around so many areas of security? You mentioned endpoint network, IAM, web stuff, email security, what does your team look like and how do you build it that way?
Steve Lodin:
Well, Sallie Mae is not as big a team as you might imagine, not as big a company, but I have a cybersecurity team that does essentially tier two investigations from a managed outsource tier one provider. And that’s kind of my blue team, red team ,also contains my purple team, and Brian will be really familiar with this. We started off with [inaudible 00:07:15] when it was a startup company. We’re continuing to use the Mandiant MSV product and using that as our purple team to validate that two things, that our security stack is working as intended and that the logs are showing up in our cloud sim sock tool as well. Yeah, I got a team of probably eight people on the cybersecurity side, and I have a team of 12 people.
Those are dedicated full-time on the IM side. It’s a large team, lots of regulatory risk audit, finding compliance side of things to make sure that levers are added correctly to the right groups with world based access control and or sorry, joiners and levers are exited from the system appropriately within 24 hours, 30 days, whatever that regulatory compliance timeframe is. So in addition to all of that, we’ve got managed outsourced providers, and then we have outsourced developers for some of the tools on the IM side. So a lot of outsourcing mixed in there as well.
Brian Contos:
Now, Steve, you were one of the first people in first organizations that, I don’t want to say embrace the cloud because a lot of people have and continue to embrace the cloud, but Sallie Mae has gone all in. I mean, I don’t know what percentage of your business is cloud-based now, but I know it’s pretty large. Maybe you could talk a little bit about that journey and sort of what you went through there.
Steve Lodin:
Sure. Sallie Mae split the company into Sallie Mae and Navient about eight, nine years ago. And in that process we went from a focused internal, everything has to be on-prem, don’t trust anybody else type of company to a cloud friendly type of company. We started off with Office 365 workday ServiceNow applications in the cloud and had a managed data center. After our managed data center contract ran out in five years, we took the opportunity to spend a couple years in that five year process explaining to our regulators that we knew what we were doing and could move our data center to the cloud so the cloud service providers. We spent a lot of time convincing them that we knew what we were doing, put a lot of tools on top, a lot of visibility, a lot of transparency built in on top of that.
We convinced them, and in 2018, at the end of 2018, we moved our entire data center assets into Amazon, Amazon reinvent presentations, FS-ISAC presentations, all describing that as public information. But today after four years we did that lift and shift where you take your virtual images in the data center and move those virtual images into Amazon, peeling off stuff, putting stuff on, but it was basically a lift and shift of those virtual images.
Brian Contos:
It was that easy, right? Just control C, control V, that’s it.
Steve Lodin:
It was a year-long process with a third party assisting us, and basically all the work happened in a month or two to move all of those assets, but it was a lot of preparation to get there. Since then, we’ve spent a lot of time focusing on workload, micro servicing, managed workloads in Amazon. We’ve gone from 20 Amazon accounts when we did the lift and shift to well over 200 now. Each workload has a strongly organized config infrastructure as code-based stack that has dev test and prod for each of those microservices and a ton of automation in there. And again, security on top of that to make sure that developers aren’t doing crazy or stupid stuff.
John Vecchi:
So what a journey. I mean, that’s amazing. And for our listeners, how did your security approach change when you did that? I mean, what are the biggest things that just absolutely changed for you and your team when you moved to the cloud like that?
Steve Lodin:
Well, we didn’t want to go backwards in our security maturity. And that meant that for us, we couldn’t just take Amazon’s native services by default. We had to still put stuff on top, security solutions on top so firewalls, web application firewalls. From our environment, we run about 40% of our end user systems, our laptops, the other 60% are virtual desktop interfaces, VDIs, virtual desktop infrastructure that run in Amazon. But so we still need stuff on top of that, endpoint protection forensic tools, secure web gateways on traffic outbound along with strong network segmentation. Back in the day, if a laptop gets infected, it connects outbound on whatever C2 protocol is out there. And sometimes you see it, sometimes you don’t.
For us, we’ve got strong segmentation. The only outbound traffic for endpoints is 80 443 out through a secure web gateway, that helps us eliminate a lot of that risk. And if you think about the two major exploit points for companies today, it’s emails and web traffic. So if you do a strong prevention of fishing and malware, getting into your emails, and then as a secondary, if you make sure that when they click on something they can’t get there because it’s a bad site, you eliminate a ton of risk into your endpoints. And we spend a lot of time keeping the same tools on top of Amazon infrastructure for our servers and our VDI environment.
Brian Contos:
So Steve, based on your journey, all these years in security, you’ve seen threats come and go, trends, priorities, what do you see today as maybe some of the biggest cybersecurity threats, and what do you see as some of the trends that people like yourself are taking to address those?
Steve Lodin:
So I think and you’ll see this in the news quite frequently, but I think one of the biggest changes over the past few years has been this focus on nation state attacks and extortion or otherwise known as ransomware and even this DDoS for hire. It’s affecting everybody down to the little business. You used to be able to say, I’m a small business, I don’t have any data, nobody’s going to attack me. Well that turned into you have money, so I’m going to attack you anyway. And either DDoS you or ransomware you, freeze up all your systems or extort you on sharing your data. That in combination with this whole nation state attack environment, I think that really hit hard with [inaudible 00:14:42] and has since moved into focus for everybody. Every board is asking the question, who’s going to hit us next and how are we prepared? So that’s what one of the major differences in the cybersecurity landscape that we’ve seen over the past few years.
John Vecchi:
And then Steve, I mean you have from a Sallie Mae perspective obviously, and you mentioned it, right, there’s a lot of regulatory requirements that you have to pay very close attention to given the structure of your organization, how does the regulatory environment kind of impact the way you look at security, select security, focus on security, strategize around it? Does it affect it, say from just a pure company that’s a pure kind of public sector? Does it have as much kind of regulatory areas? Is that makes sense?
Steve Lodin:
Yeah, it does. And so the regulators are focused on what’s your size, what’s your impact, what’s your involvement in the financial services industry? They have what’s called the FFIEC Cybersecurity Assessment Tool, the CAT tool. And it assesses based on, we’re a small bank, so we’re not City, J.P. Morgan, Visa, we don’t have the same attack surface that they do so we’re less risky. We have fewer internet connections. We don’t have branch offices and ATMs and that type of attack. So smaller, lower risk, but then we take a look at what are the tools we need to have in place across the entire security spectrum from third party vendor management, threat intelligence, server and endpoint, vulnerability and patch remediation.
They assess you based on that in a traditional CMM zero to five type of rating from beginner to advanced to see how you’re doing in your tools and we do these types of assessments. The cybersecurity CAT is one of them. The other one we use is the Cyber Risk Institutes profile. Again, focused on the financial services industry in combination with NIST to be able to assess where we are, what gaps we have and what we believe we need to do to address any potential residual risk in that environment.
Brian Contos:
So Steve, let’s pivot a little bit to xIoT because about a year ago I called you up and I’m like, Steve, what do you think about xIoT, this whole world of IOT and OT and network devices, all these embedded firmware things that are out there. And I wanted to get you your take on it and just kind of walk through the total addressable market and the risk posture, et cetera. But why do you think that historically, xIoT has been such a complicated issue for organizations to try to address, especially when they find out, yikes, I’ve got like 50,000 of these things, I don’t have like 500 of them. Why has it been so complicated?
Steve Lodin:
Well, first of all, you hit the key point. In every security surface management, you have to have a good understanding of what your inventory is and IoT devices is one of those hardly managed, hardly inventoried scenarios. You don’t know what you have until you figure that out with some tools and technology, it’s a difficult situation. Back in the day, let’s say in the early to mid ’90s when vulnerability scanners first came out, the first one that came out was Satan, if you remember.
Brian Contos:
Dan Farmer’s-
Steve Lodin:
Dan Farmer’s. Yep.
Brian Contos:
Security administrator tool for analyzing network, is that what it was?
Steve Lodin:
Yes. Or you could change it to Santa if you didn’t like to say Satan.
Brian Contos:
You could run the Pearl Script to Santa is it? Yeah.
Steve Lodin:
So I was a beta tester in that, in a manufacturing environment with a ton of, at the time wasn’t called IOT, but effectively it was. I ran Satan against a global network manufacturing devices that run production lines to put together instrument displays or radios and I managed to take them down the first time I ran Satan. Those IOT devices didn’t know how to respond to an attack tool or a vulnerability detection tool.
Brian Contos:
I’m sure that made you extremely popular with the guys in manufacturing.
Steve Lodin:
Yeah. Yeah. That didn’t, by the way. Yeah, it took down lots of manufacturing systems running Satan on a global network like that. But inventory is the first thing, understanding that I think this new xIoT complication comes from a couple of different things. One, they’re small resources, so they’re not always configured to have the entire security stack in place. Two, there’s definitely a legacy mentality. Put it in there once, 15 years ago, it still seems to work, don’t touch it, don’t upgrade it, don’t patch it, don’t do anything, don’t touch it, it still works. So there’s that legacy mentality.
The other thing is a lot of businesses that are running those types of devices have a, no one would attack me scenario. They think that I’m a small company, I have a small network imprint, nobody’s going to want to attack me. Why would they do that? Forgetting the fact that Mirai Botnet exists. And then there’s this whole concept of, well, we air gap that network, so there shouldn’t be any problem. But air gaps have largely disappeared over the years. So I think that’s really how it’s so complicated is to start off with the basics there.
John Vecchi:
So Steve, given that, and you think in terms of the overall attack surface, we just talked about some of these, it’s hard to get visibility, some of the traditional tools don’t really work too well, you mentioned vulnerability management and the host of traditional legacy approaches don’t work terribly well with these devices. Have you done anything different to get visibility and furthermore, how do you think of your attack surface now relative to these devices?
Steve Lodin:
Well, there’s two ways to look at attack surface, one is internal, yeah, there’s external. Hopefully as a company, you’ve got that external attack surface tools in place, and hopefully you’ve got network segmentation in place that doesn’t expose any of those IoT, xIoT devices to the internet or to the attacker side. From our perspective, we have spent a lot of time doing internal network segmentation to limit the scope and capability to talk between different planes of tools that we have in place. So for us, we’ve got a small limited number of these IoT devices, and we’re trying to do two things on those to limit the attack surface. One is to have good security configuration built in. That’s a challenge in the IoT devices. They’re not always built to support that. And the other is basically to limit through segmentation accessibility. And again, that’s a challenge in order to have the devices work as you intend them to be working. So definitely it’s not a solved easy go follow a playbook scenario.
Brian Contos:
Yeah, Steve, we’ve been doing this long enough where we see these vulnerabilities pop up and trends related to those and it seems like the nation states and the cyber criminals all kind of get fixated on it and just wreak as much havoc as they can, make as much money as they can, cause as much destruction as possible for as long as possible. I’m wondering, because we’re seeing this trend now of pivot attacks where attackers are getting in through IT, usually through a phishing attack. It could be through email messaging, social media, what have you, but they infect a laptop that’s internal to the organization. From there, they start to pivot and look for xIoT devices that could be a printer or security camera, an xIoT device that could be a load balancer or a switch even. And they move over there so they can maintain persistence of aid detection.
Most of them are Linux or Android, VxWorks, BSD, things like that. So they’re regular operating systems with the same ports, protocols, capabilities as a Linux server would. And then they use that again to maintain persistence of aid detection and attack IT assets and then to exfiltrate that data out. Now, it sounds like you’ve done a lot of work in finding those devices and segmenting the network and trying to harden those devices to follow good configuration approaches. I think you’re way ahead of most organizations when it comes to actually trying to secure xIoT. But my question is this, given that no one’s really paying attention to these devices at scale and most organizations don’t know what they have. They have default passwords into insecure firmware, they’re loaded with vulnerabilities and clear checks, protocols and this and that, is this going to be the new new? Get in through it, pivot to xIoT, reek havoc for years, potentially stealing sensitive data, ransomware attacks, things like you mentioned before because people just aren’t ready for this? Is this the new new?
Steve Lodin:
Yeah, I definitely think it’s the new new. Most companies are spending a lot of time securing their endpoints and securing their servers, and they haven’t gotten into the physical world or into the data center infrastructure world. So they’re spending a lot of time just focused on the external presence, the external devices, and missing the core pieces to their environment. If they don’t have segmentation already built in, if they don’t have strong configuration management on devices, if it’s a plug and play, they’re definitely ripe for attack.
John Vecchi:
And have you seen, again, we talked about, I mean you focus on nation states, you talked about that it’s something you pay a lot of attention to, you mentioned the Mirai Botnet. We have a tool called Fronton that the Russian FSB developed that’s now out kind of there in the wild. And Brian mentioned a little bit about the nation states focusing on that. Are you seeing that, are you keeping an eye on nation states now focusing on these type of devices in your environment? Is that anything you’ve seen or are you focusing on that?
Steve Lodin:
Well, we’re lucky that we don’t have a ton of internal devices that would fall into that category. We don’t have ATMs. We don’t have a huge physical presence that might be in their site line. So for us, it’s really making sure that we’re doing best practices in managing those types of devices, but not a huge attack surface hitting us from the outside that concerns us to make huge changes in our environment.
Brian Contos:
Yeah, I think that’s unique about Sallie Mae, Steve. I mean, it’s financial services, but it’s not a bank. You don’t walk down to the local, like you said, the local Sallie Mae ATM machine or go into a branch, at least not yet I don’t know your plans are for the future. I’m not trying to make your roadmap, but yeah, you are a little bit more ethereal, I think, than the local bank. What I will wonder though, because I know you do have this mix of systems and things like that, what kind of stories from the trenches maybe can you share any interesting war stories or use cases as of late?
Steve Lodin:
Oh, good question. For us, it’s regulatory compliance, that’s a key thing for us. We are friends with the financial services ISAC environment. We participate strongly in understanding the attacks, providing that information to our colleagues. We share a ton with the rest of the financial services in anticipation of helping them get ahead if we consider ourselves maybe a little more visionary, a little more ahead, using tools to identify attacks like that, we’re trying to share that information and make sure that the overall environment improves. Is it 100%? No, that would be facetious to assume that, but we’d like to think that we’re a little advanced in identifying attacks, preventing attacks, and preventing them from pivoting into our environment, especially on the managed services side and also on the managed device side. We try to make sure that our devices are configured appropriately using best practices.
If a traditional center for internet security configuration guide doesn’t exist, will still work to identify attack scenarios and improve those. So across the entire environment, we’re trying to make sure that attackers have a reduced surface and that our configurations are set up appropriately. And so that includes having a license plate reader in the environment to check to make sure that cars coming are approved, but making sure that that device isn’t accessible from the internet and able to be hacked. Those are the types of exposures that we’re trying to prevent on the physical and IoT side as well.
John Vecchi:
Steve, it sounds like you’re sharing this information with other financial institutions so sounds like there’s a discourse and you’re talking to other kind of leading financial institutions, and is that safe to say and you’re exchanging information and recommendations? Is that happening? It sounds like that’s happening.
Steve Lodin:
Yeah, definitely. We’re one of the more prominent contributors to identifying attacks and sharing that knowledge to make the whole industry move upwards in their protection mechanisms. Happy to do that, the more that we can identify, document and share the less attacks that are hitting our colleagues and our peers in the industry.
Brian Contos:
Great. Well, Steve, this has been really wonderful, especially strolling down memory lane a little bit there with Morris Worm and Staff and Satan and all of that. But for some closing thoughts, I wonder if you have any advice that you can give our listeners that are working in cybersecurity. You have just as much breadth and depth of anybody that I’ve ever met in the industry. You go way back and you’ve kind of seen it all. So for those listening in, what can you leave them with?
Steve Lodin:
Well, I think one thing is many companies still have a ton of legacy debt. They’re still in their own data center with systems that haven’t been patched, aren’t appropriately configured. I think that the shift to the cloud accelerates removing all of that legacy security debt I advocate that, obviously don’t do it beyond what your company is capable of doing, but for us, basically that shift to the cloud continued to provide security opportunities and improvements in our overall environment. We don’t have legacy systems, legacy operating systems exposed to potential attackers.
Again, even though it may seem like it’s real easy to put up a firewall and call it secure, that’s not an easy thing to do and protect your overall environment, but having a good understanding of what’s out there, where it is, how it’s configured, regardless of whether it’s a window server or a door opening mechanism that connects to the network, all of those devices are at risk if they’re attached to a network and even at risk if they’re theoretically air gapped. So making sure that you have your tools and technology in place to eliminate or reduce risk appropriately is always a strong way to move.
Brian Contos:
That was really interesting, Steve. I’d like to take it one more step, and if you don’t mind, let’s talk a little bit about the [inaudible 00:32:24], maybe you could tell us what’s going on there with all those vulnerabilities.
Steve Lodin:
So that [inaudible 00:32:31] known exploitable vulnerabilities is a tool that we’ve been using to track the vulnerabilities that are most possible to affect us. And one of the interesting things that I’ve noticed on the [inaudible 00:32:43] is that they’re spending a lot of time focusing on exploitable vulnerabilities added in OT systems. If you take a look at some of the data coming out from the vulnerability providers, they’re also focusing on Emerson, Siemens, Schneider, these OT devices that many times get installed and never managed and never patched and never updated. So [inaudible 00:33:11] is really starting to focus on that. If you have those devices, it’s a great way to figure out what the exposure is and what the vulnerabilities are, but sometimes it does hard things for non-IT people, and that’s to update their systems to the latest operating system or version from the vendor. That’s tough for a lot of these people to take systems down, patch them, and get them back up to date. But the [inaudible 00:33:37] has expanded beyond just Windows and Lenox into these IT type devices.
John Vecchi:
Well, that’s very, very precious advice. I’m sure our listeners will greatly appreciate that so thank you so much, and again, thanks Brian, our host, and thanks to our very special guest today, Steve Lodin. Steve, thanks for joining us today.
Steve Lodin:
Happy to be here. It’s great talking with you guys again.
John Vecchi:
And remember everybody, the IoT Security Podcast is brought to you by Phosphorus, the leading provider of proactive full scope security for the extended internet of things and until we meet again, I’m John Vecchi.
Brian Contos:
And I’m Brian Contos.
John Vecchi:
And we’ll see you next time on Phosphorus Radio.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.