Conversations about the cyber risk of smart, connected playthings and electronics may have been on the back burner for Christmas and Hannukah, 2022. But there’s little reason to believe that any measurable improvement has been made in the cybersecurity or privacy protections of connected toys and personal electronics. That’s what Paul F. Roberts of SecurityLedger.com writes in his recent Forbes piece called “Smart Toys Are Still Hackable (We Just Don’t Talk About It).”
In this excerpt from the article, Roberts talks to Phosphorus CSO Brian Contos about the ongoing risks presented to businesses even from personal xIoT devices and the research coming out of Phosphorus Labs.
For example, a recent study of the security of IoT devices by Phosphorus Labs, a cybersecurity company, found that 68% have high-risk or critical vulnerabilities. That’s consistent with other studies of IoT insecurity. For example, a 2020 study by Palo Alto Networks found that 57% of IoT devices are vulnerable to medium- or high-severity attacks while 98% of all IoT device traffic is unencrypted, exposing personal and confidential data and allowing attackers the ability to listen to unencrypted network traffic and collect personal or confidential information.
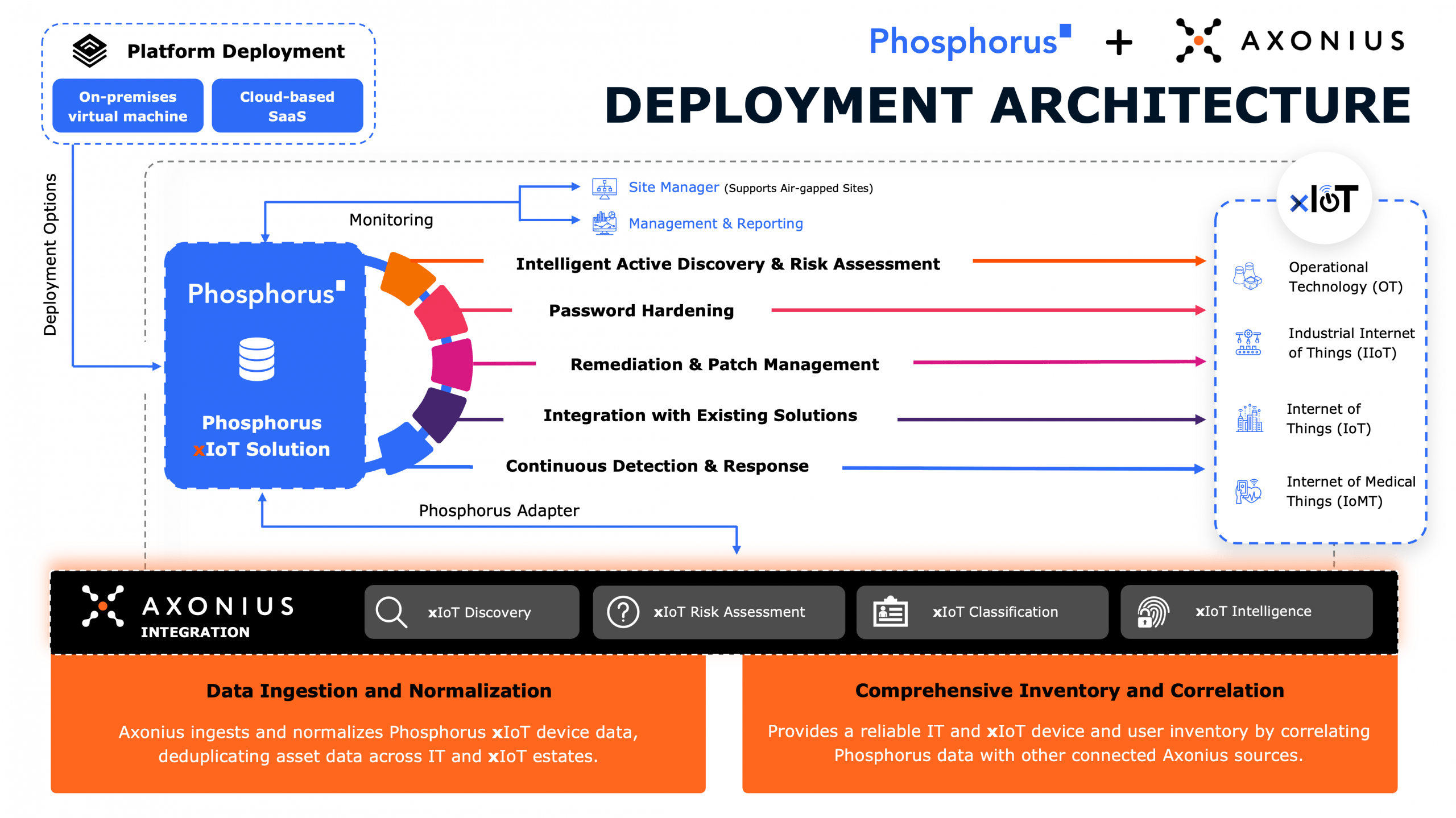
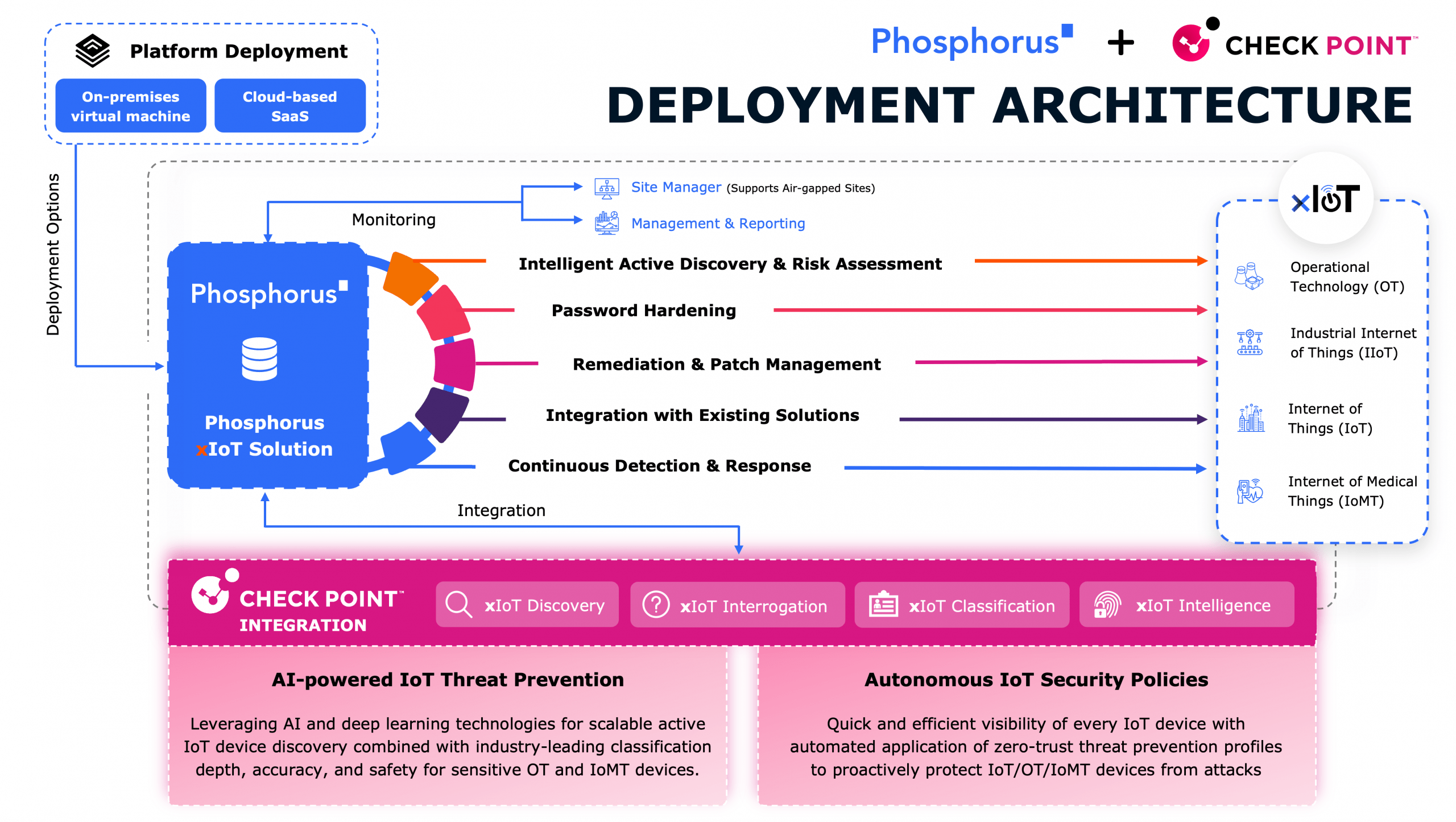
While Phosphorus’ research focused on the kinds of devices and technologies used by businesses and government (like printers, voice over IP phones and physical access systems), the broader Internet of Things – what Phosphorus refers to as the xIoT – isn’t limited to those devices. The IoT is estimated to have a population of 50 billion devices globally and is growing rapidly, even as traditional IT endpoints – desktops, laptops and servers – are on the decline, said Brian Contos, the CSO at Phosphorus. Security issues with the xIoT matter, also, because the problems facing smart, business technologies like VoIP phones, security cameras and printers aren’t limited to those product categories.
Phosphorus’s research noted a number of factors contributing to the security issues on the IoT. Among them: a lack of secure development practices and experience at connected device makers; a heavy reliance on shared software and components (often open source); and a business culture that emphasizes time to market and feature development over robust security. The past year has shown that vulnerabilities in software supply chains are a major source of cyber risk for organizations.
Credential mismanagement is just the most obvious byproduct of that general lack of security. Phosphorus notes that many xIoT devices come with default passwords which users frequently forget to change, while other devices don’t support complex passwords.
In short: the IoT is a major blind spot, which hackers can use to infiltrate both home and business networks. With access, they can pivot to other assets, steal information, launch attacks, carry out physical sabotage, and achieve long-term persistence, Contos said. And businesses are notoriously bad at tracking the IoT devices deployed in their environments. By Contos’ estimate: every employee has between 3 and 5 IoT devices they use at work, while companies regularly underestimate the size of their deployed IoT device population by 50% or more.
And the risk posed by vulnerable gifts under the Christmas tree impacts businesses as well – as workers carry personal electronics in to the office, he said.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.