“NSA and CISA encourage network defenders to implement the recommendations found within the Mitigations section of this advisory… to reduce the risk of malicious actors exploiting the identified misconfigurations.”
– CISA Cybersecurity Advisory AA23-278A
Only since September of this year, the Cybersecurity and Infrastructure Security Agency (CISA) has released a dizzying number (more than 50) of Industrial Control Systems (ICS) Advisories covering a broad spectrum of mission-critical OT, ICS, and IIoT Cyber-Physical Systems (CPS). These advisories provide the public with important information on security issues, vulnerabilities, and exploits targeting ICS devices.
I spend a lot of my time speaking at security industry events – including many focused on the OT, ICS, and Healthcare verticals – where I talk about the state of these xIoT devices (which include IoT, OT, IoMT, and IIoT Cyber-Physical Systems), the threats and threat actors who are targeting them, and the modern/proactive security measures that are critical to protect them. I also demonstrate how easy it is to hack a security camera and industrial FANUC robot (which is often shocking to even the most experienced network defenders).
I won’t bore you with the details, but let’s just say the security state of these devices is worse than the state laptops were in back in 1994. Gartner summed it up very well in their recent Market Guide for CPS Protection Platforms:
“Operational systems are deployed with their default credentials unchanged,” “Ports on all kinds of systems in all kinds of remote locations are wide open,” and “The number of vulnerabilities continues to grow at the same time as CPS patching remains very difficult."
Gartner Market Guide for CPS Protection Platform
MORE ICS DEVICES MEANS MORE MISCONFIGURATIONS
There are now 10x as many xIoT devices worldwide as all traditional endpoints combined. Yet, the challenge of finding, fixing, managing, and monitoring these CPS devices has left a massive attack surface targeted by threat actors, nation-states, and ransomware gangs. And, as the shocking number of CISA advisories has highlighted, the vulnerable state of our Industrial Control Systems has put these ICS/OT devices square in the crosshairs of these malicious threat actors.
This is why CISA’s recent Cybersecurity Advisory, titled “NSA and CISA Red and Blue Teams Share Top Ten Cybersecurity Misconfigurations,” is not only a forewarning to network defenders and xIoT device manufacturers; it is tremendously insightful, relevant, and instructional in highlighting how organizations can reduce the risk of malicious actors exploiting OT, ICS, and IIoT Cyber-Physical Systems.
In their October 5th joint cybersecurity advisory (CSA), the National Security Agency (NSA) and CISA highlighted the Top 10 most common cybersecurity misconfigurations in large organizations, which included the following:
- default configurations
- insufficient monitoring
- poor patch management
- poor credential hygiene, and more.
As outlined by NSA and CISA, the misconfigurations above illustrate “…a trend of systemic weaknesses in many large organizations, including those with mature cyber postures.” We not only agree but also highlighted many of the same risks in our xIoT Threat & Trend Report 2022, published by our research division, Phosphorus Labs.
Having interrogated millions of OT, IoT, IIoT, and IoMT CPS devices, our research indicates that more than 70% of xIoT devices are deployed with default credentials, and 68% have CVEs of 8 or above. As well, the average age of unpatched firmware on deployed xIoT devices is 6 years, while 25% of all devices are end-of-life by their manufacturer.
MORE ICS MISCONFIGURATIONS REQUIRE MITIGATING ACTIONS
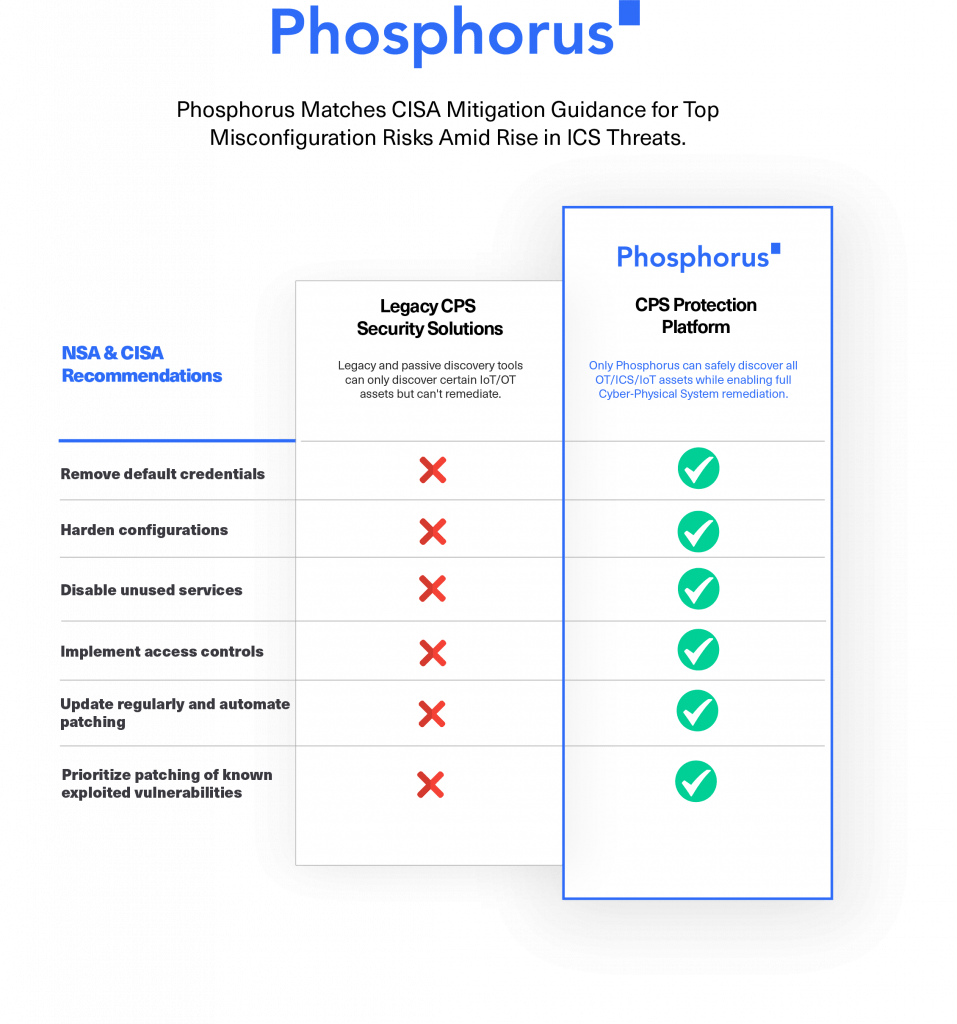
In their same joint advisory, NSA and CISA recommended network defenders to implement a set of important mitigations “to reduce the risk of malicious actors exploiting the identified misconfigurations.”
CISA’s recommended mitigations included the following list:
- Remove default credentials and harden configurations.
- Disable unused services and implement access controls.
- Update regularly and automate patching, prioritizing patching of known exploited vulnerabilities.
- Reduce, restrict, audit, and monitor administrative accounts and privileges.
SIDEBAR
CISA and the WaterISAC Respond to Cyberattack on the Municipal Water Authority of Aliquippa
Nation-State actors targeted a Unitronics Vision Series PLC by exploiting cybersecurity weaknesses, including poor password security.
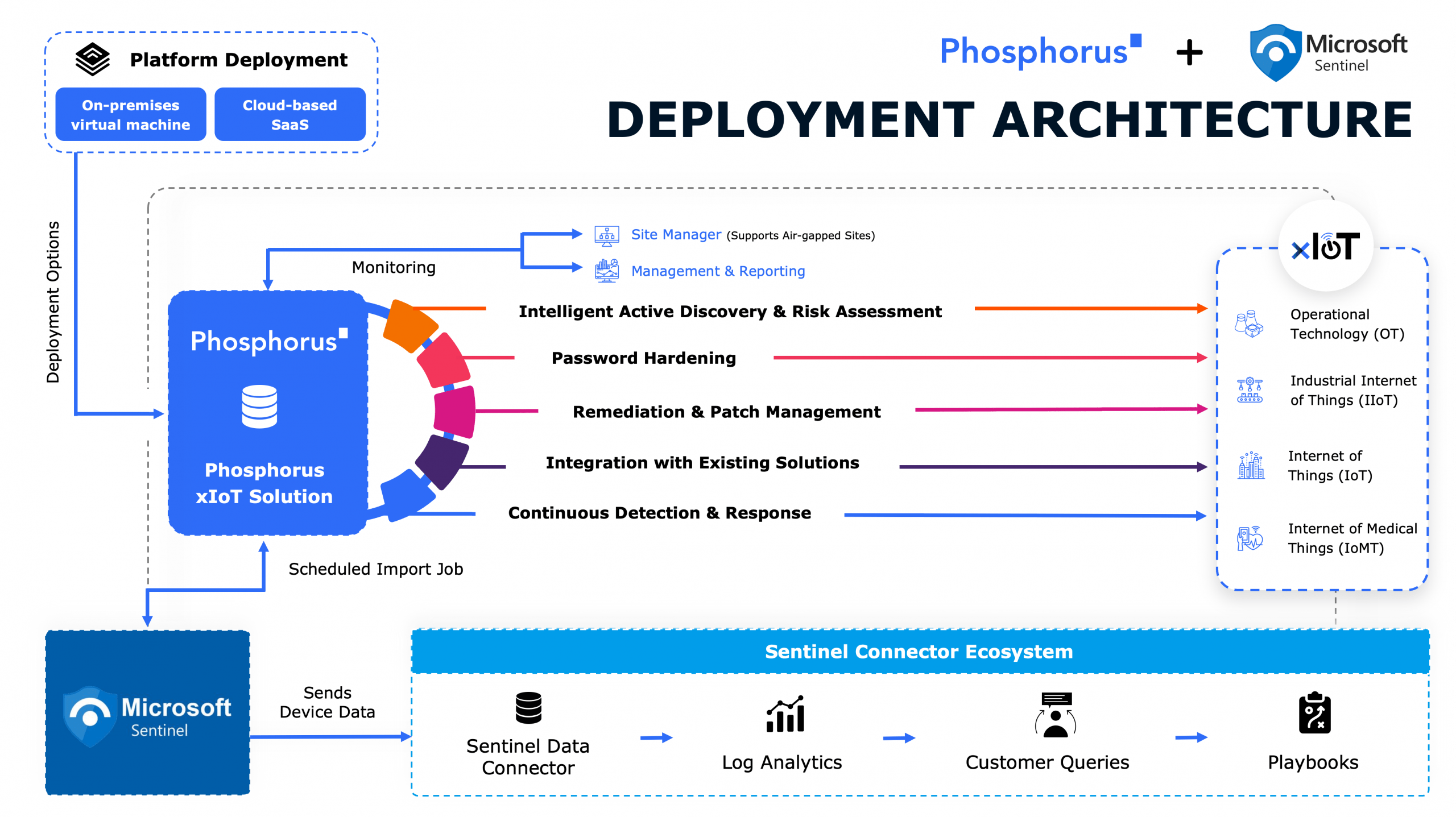
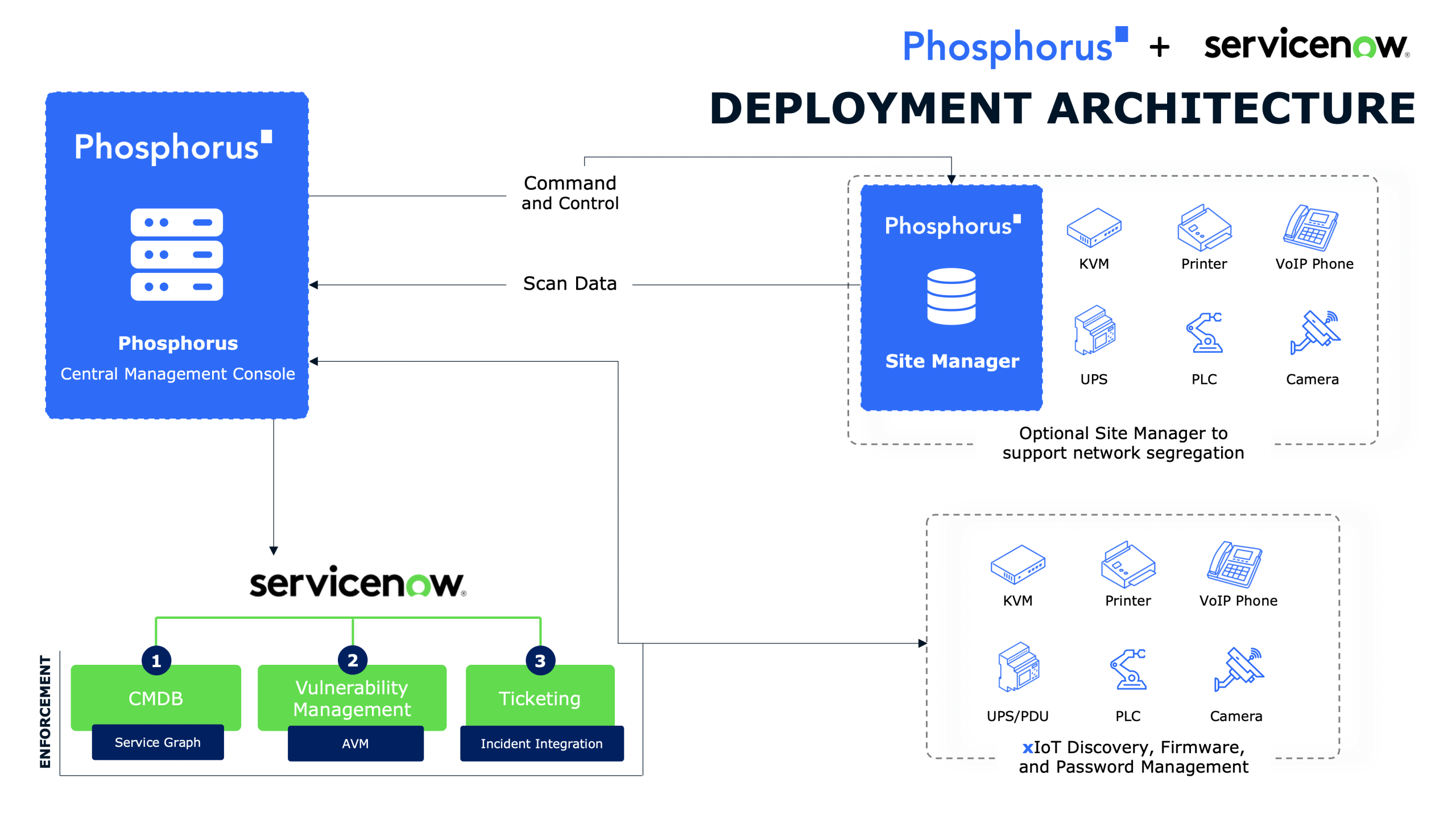
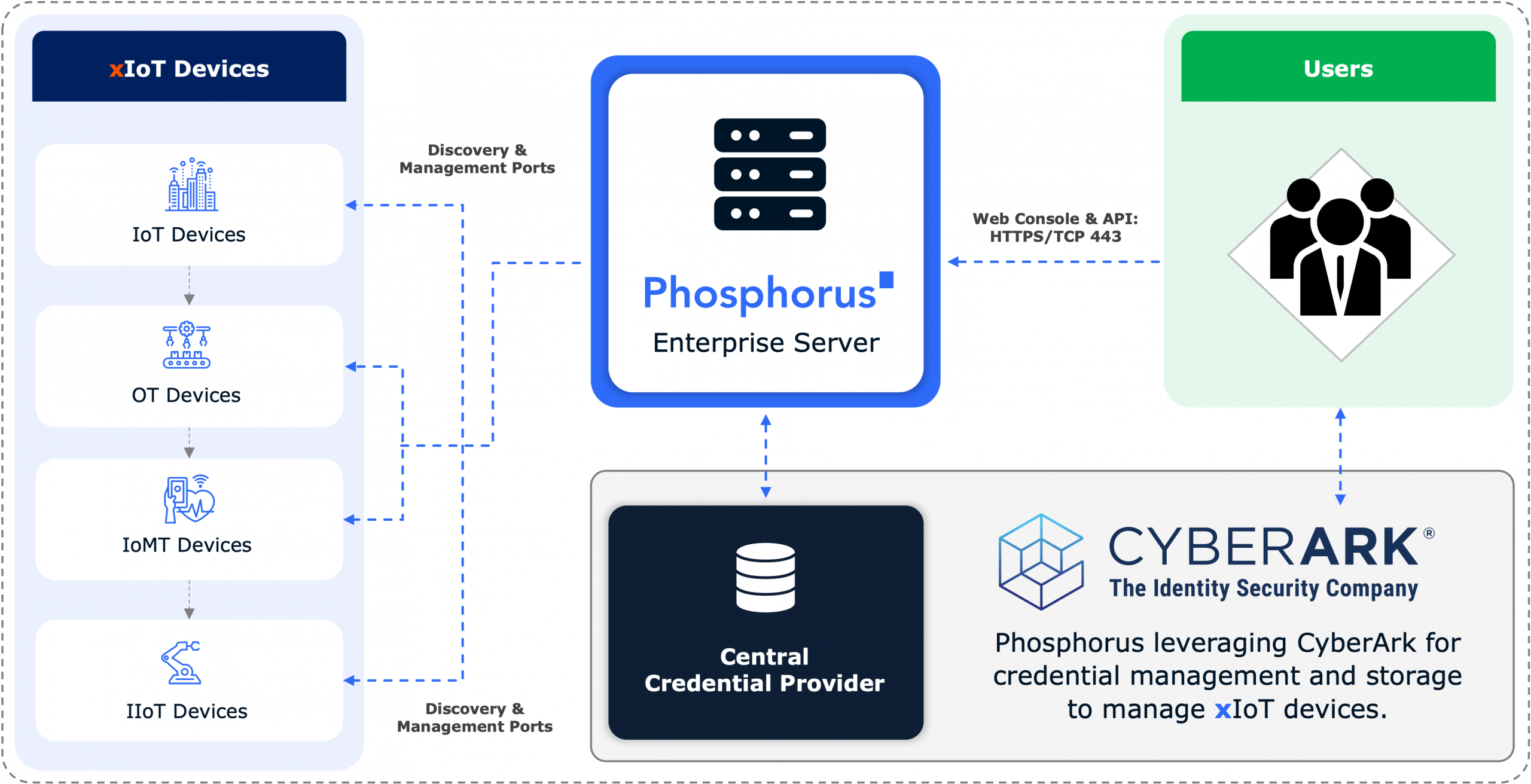
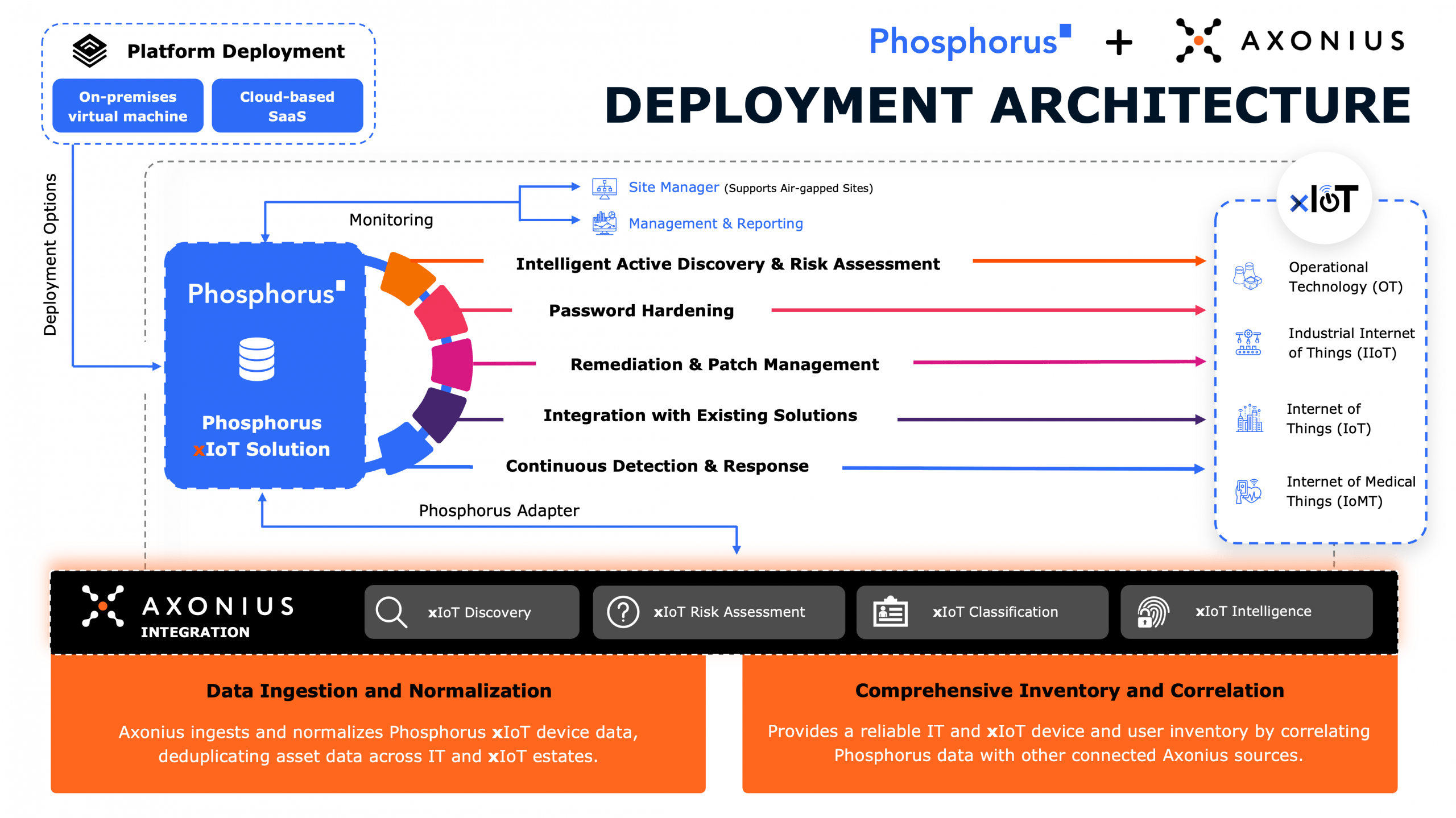
Nearly all critical recommendations that NSA and CISA encouraged companies to implement represent capabilities that Phosphorus has long addressed through our best-of-breed Unified xIoT Security Management & Breach Prevention Platform. It is the industry’s only CPS Protection Platform covering the entire security and management lifecycle for xIoT devices—including OT/ICS, IoT, IIoT, and IoMT estates.
The Phosphorus software-based and agentless xIoT security platform integrates seamlessly with existing security stack technologies, like NGFW, ITSM, CMDB, PAM, etc., and enables these patented, proactive functionalities:
- Safe and efficient Intelligent Active Discovery
- High-Fidelity Device Posture Assessment
- Credential and Device Hardening
- Remediation and Patch Management with full control
- Operational Monitoring & Predictive Maintenance
- Ongoing Monitoring and Management
As we enter the next evolution of IoT/OT/IoMT device security at a time when the enterprise attack surface is evolving beyond traditional endpoints to 10s of billions of new Cyber-Physical Systems, it is more important than ever that we bring the management processes and procedures of these devices forward from those of the 1990s to a better and more secure state, mitigating the ever-increasing threat by hackers, Nation States, and ransomware gangs.
Author
John Vecchi
As Chief Marketing Officer, John brings more than 25 years of experience in high-tech marketing, strategy, product marketing, product management, sales and consulting. Most recently, John was Chief Marketing Officer at Anitian, ColorTokens, and Anonyome Labs.
Related Posts
Today marks a significant milestone in our mission to secure the Internet of Things:...
Phosphorus Cybersecurity Inc., the leading provider of security and device management for the extended...