On December 16, 2024, the FBI issued a Private Industry Notification (PIN) alerting organizations about a surge in HiatusRAT scanning campaigns exploiting vulnerabilities in Chinese-branded xIoT devices, like banned IP cameras from Hikvision, and DVRs. The warning highlights that threat actors are actively leveraging default passwords, outdated firmware, and risky configurations to gain unauthorized access to these devices. Once compromised, these devices can be used for broader malicious activities, including network infiltration, data exfiltration, and launching distributed denial-of-service (DDoS) attacks.
The FBI’s PIN emphasizes the urgency for organizations to act against these threats. HiatusRAT itself is a Remote Access Trojan (RAT) that’s been out and in use since 2022, used to take over outdated devices and put them to use for malicious purposes. The FBI PIN indicates that the threat actors targeted IoT devices in the US, Australia, Canada, New Zealand, and the United Kingdom, scanning for devices with specific CVEs and weak passwords. In particular, they note, “actors targeted Xiongmai and Hikvision devices with Telnet access.”
The FBI’s recommendations include patching vulnerable firmware as soon as updates are released, changing default device passwords, and reviewing device configurations for insecure settings. Without proactive measures, the attack surface posed by unmanaged xIoT devices remains highly exploitable, increasing organizational risks.
Organizations should implement the recommendations, paying particular attention to these affected devices, which have also been widely distributed by OEMs.
- Hikvision Cameras: Models including DS-2CD2xx2F-I Series, DS-2CD2xx0F-I Series, DS-2CD2xx2FWD Series, DS-2CD4x2xFWD Series, DS-2CD4xx5 Series, DS-2DFx Series, and DS-2CD63xx Series.
- TBK DVRs and Rebranded Devices: Models such as DVR4104, DVR4216, and devices rebranded under Novo, CeNova, QSee, Pulnix, XVR 5 in 1, Securus, Night OWL, DVR Login, HVR Login, and MDVR Login.
- D-Link Cameras: Models including DCS-2530L (before firmware version 1.06.01 Hotfix) and DCS-2670L (up to firmware version 2.02).
Implications for Organizations
The FBI’s warning sheds light on the systemic security challenges inherent in xIoT (xTended Internet of Things) devices—yes, including IP cameras and storage systems but ranging from printers to infusion pumps to HVAC controllers—due to decades of neglect, poor management practices, and outdated security models. Unlike traditional IT systems, IoT, OT, and IoMT Cyber-Physical Systems (CPS) often operate with default settings, contain critical vulnerabilities, and are left unmonitored for years, if not decades. As a result, cybercriminals and nation-state actors exploit these weaknesses for persistent access to networks and to carry out large-scale attacks.
Organizations must take this alert seriously: a compromised xIoT device can act as a beachhead, allowing attackers to pivot deeper into sensitive networks. This can have significant consequences, including operational disruptions, financial losses, regulatory penalties, and damage to reputation.
The notification also underscores the evolving nature of the xIoT threat landscape. With increasing reliance on IoT and OT (Operational Technology) devices across industries—such as critical infrastructure, healthcare, manufacturing, and transportation—the potential attack surface continues to grow by orders of magnitude. Without a proactive, scalable security approach, these devices will remain vulnerable, wide-open doors.
The Phosphorus Perspective: Proactively Securing xIoT Devices
The recent cyber campaign detailed by the FBI directly targets xIoT devices like Hikvision IP cameras and digital media storage systems—key components of enterprise and industrial ecosystems. These attacks are not isolated incidents but represent a growing trend in xIoT exploitation. Phosphorus Cybersecurity recognizes that such campaigns are made possible due to long-standing neglect of the xIoT attack surface, which has remained largely unmonitored and unmanaged in most organizations.
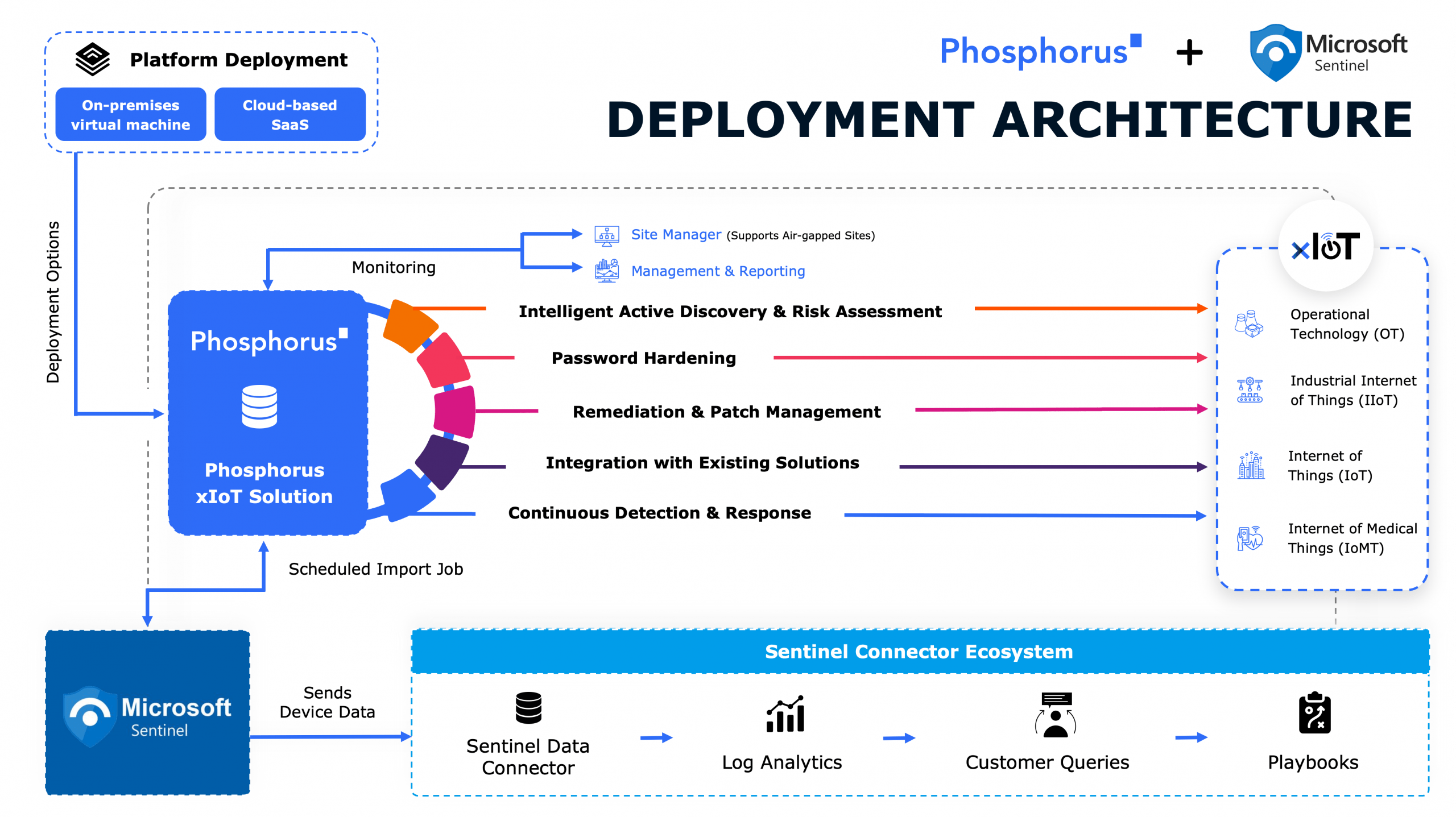
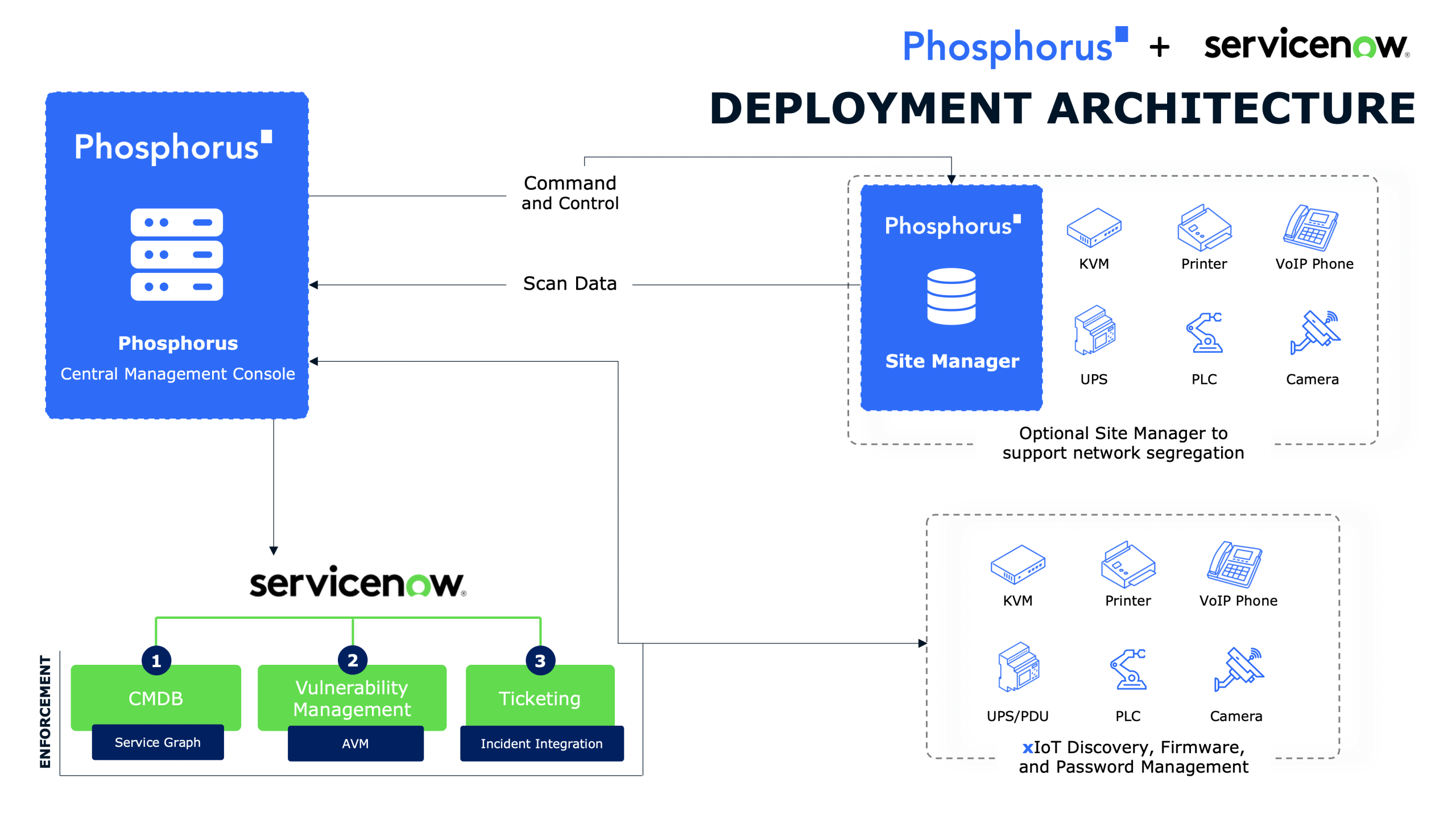
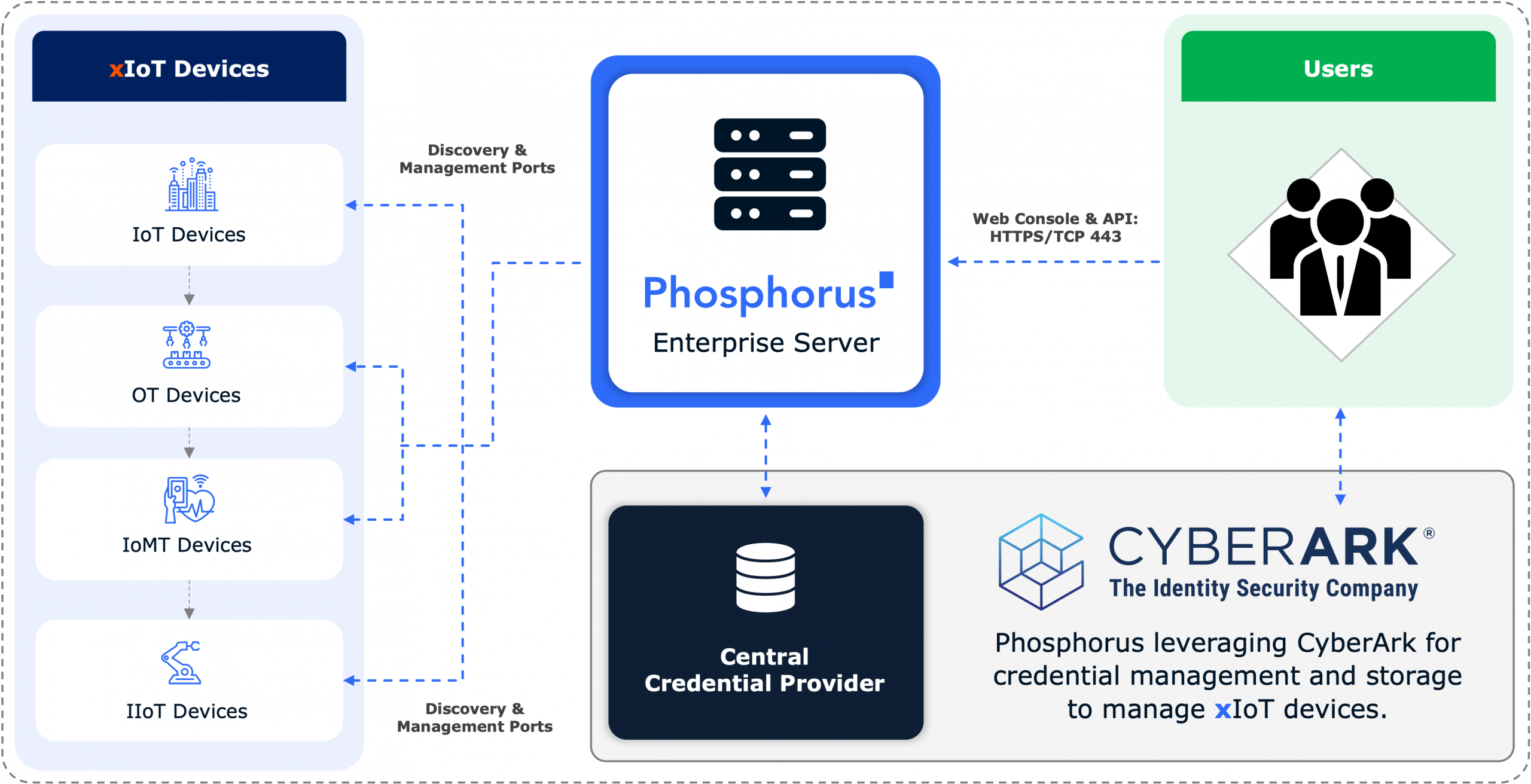
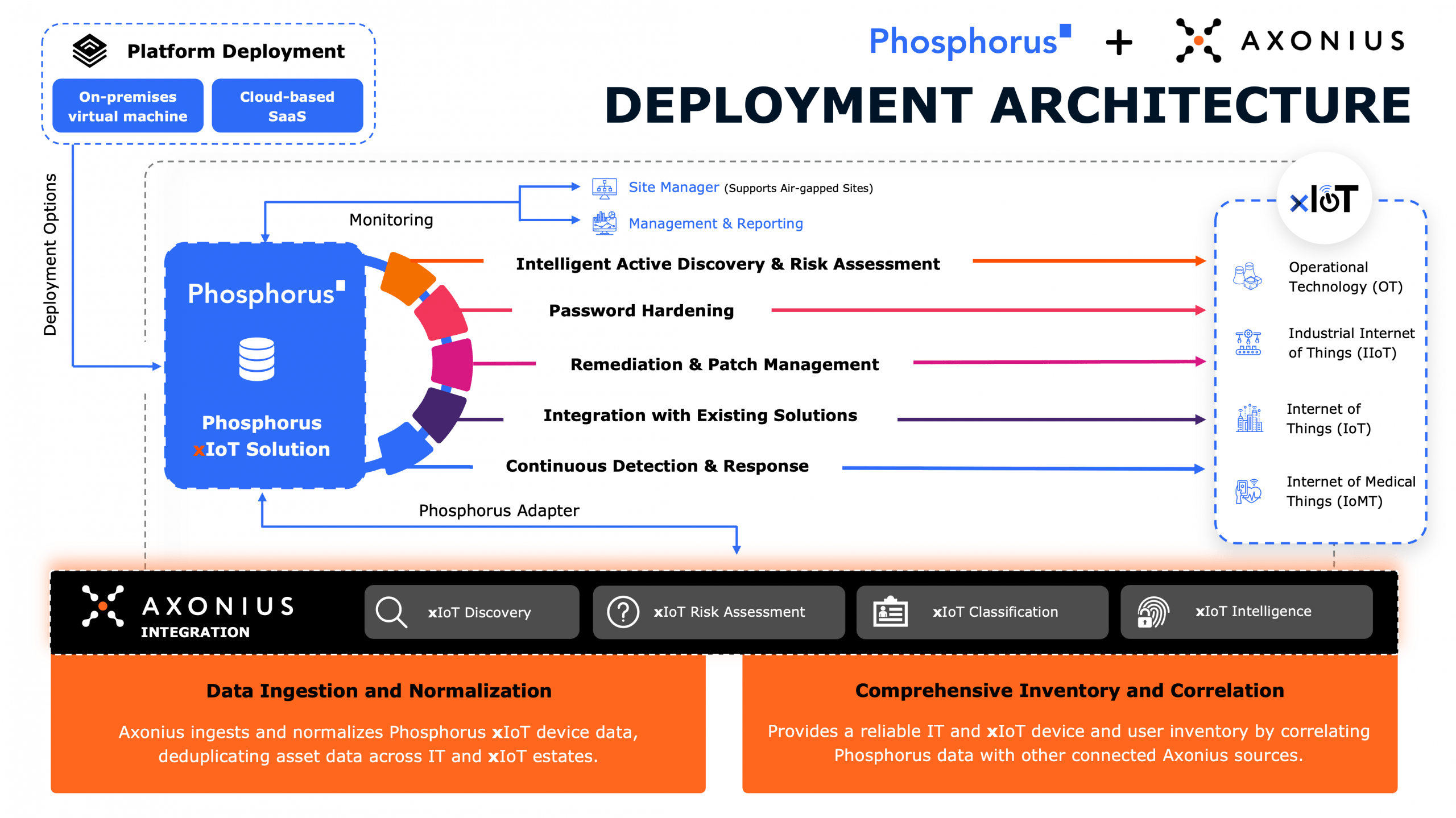
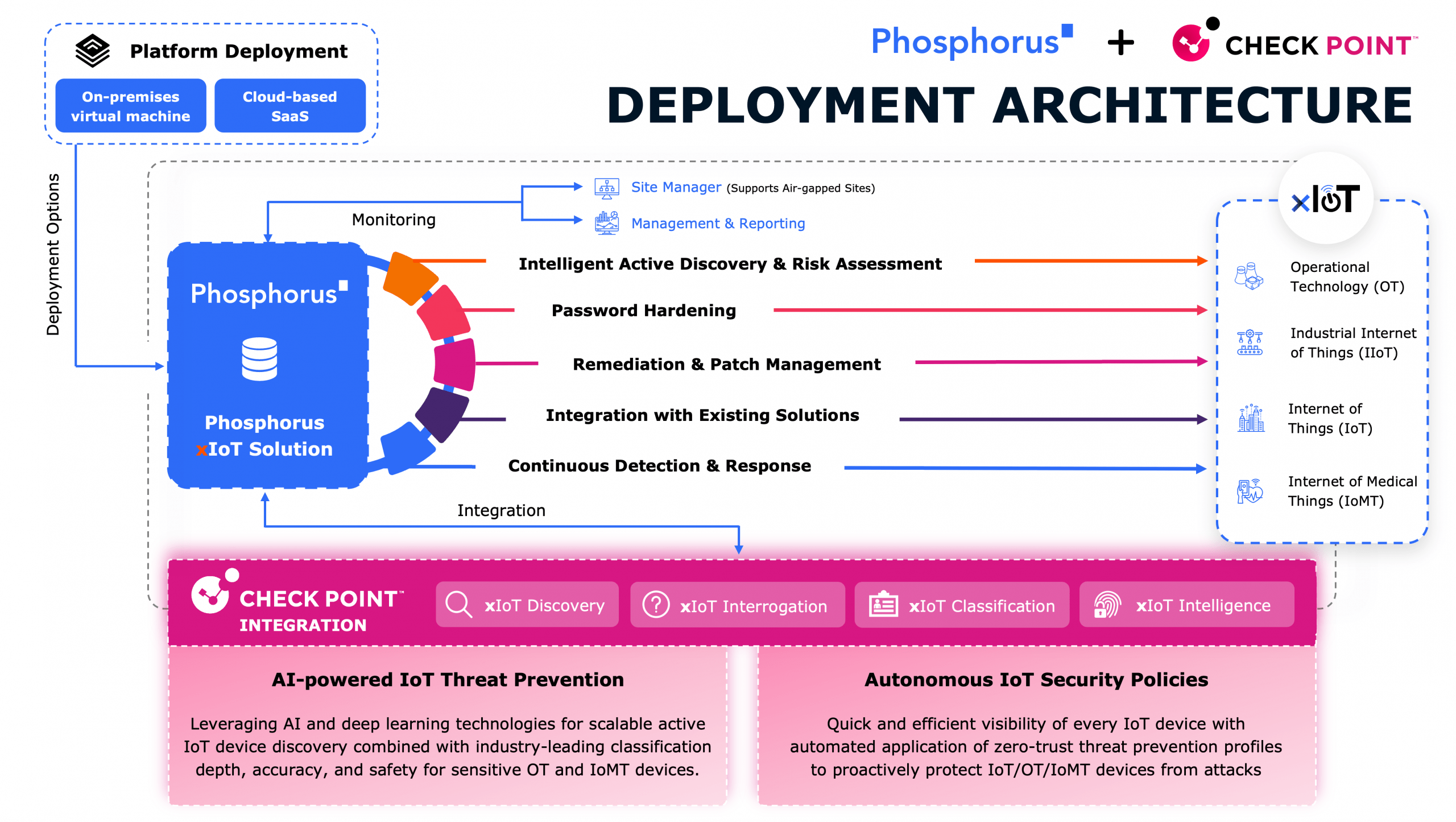
Phosphorus delivers a Unified xIoT Security Management Platform that enables organizations to find, fix, and manage xIoT devices at scale. With support for over 950 xIoT manufacturers and 1 million unique device models, Phosphorus goes beyond legacy passive tools that rely solely on network monitoring. Instead, Phosphorus proactively identifies and mitigates vulnerabilities, reduces the attack surface, and automates critical security actions such as:
- Patching Outdated Firmware: Keeping devices updated is one of the most effective ways to defend against known vulnerabilities. The Phosphorus platform automates firmware assessments and updates to ensure devices are not left exposed.
- Eliminating Default Passwords: Default credentials remain one of the most exploited attack vectors. Phosphorus identifies devices using default passwords and enables organizations to enforce strong password policies automatically.
- Hardening Risky Configurations: Insecure device settings create hidden risks. Phosphorus continuously monitors and remediates risky configurations, ensuring xIoT devices are securely deployed and managed.
- Removing Banned Devices: Devices banned by the FCC in the United States pose a security risk. Phosphorus enables their detection and specific device-level actions, such as changing passwords, disabling services, and reducing connectivity, prior to their removal from the network.
The FBI’s recommendations align directly with Phosphorus’ capabilities, emphasizing the need for immediate action. Patching, credential management, and configuration hardening are not optional—they are foundational requirements to secure the xIoT attack surface.
The FBI’s warning serves as a call to action: organizations can no longer afford to ignore their xIoT attack surface. With Phosphorus, enterprises can gain full visibility and control over their xIoT systems, ensuring they remain protected against today’s evolving cyber threats.
To learn more about how Phosphorus can secure your xIoT devices and address the challenges outlined in the FBI notification, visit Phosphorus Cybersecurity and contact us today for a technical demo.
By taking proactive steps now, organizations can mitigate the risks associated with insecure xIoT devices and protect their networks from future cyber campaigns. Phosphorus stands ready to help enterprises defend against this critical and growing threat.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.