What to know about the new Directive requiring asset visibility and vulnerability detection by April 2023
With the announcement of Binding Operational Directive (BOD 23-01): Improving Asset Visibility and Vulnerability Detection on Federal Networks, the Cybersecurity and Infrastructure Security Agency (CISA) issued a sea change meant to improve asset visibility and vulnerability detection within federal agencies. This directive focuses on all Federal Civilian Executive Branch (FCEB) departments and agencies, but the concept applies to all organizations and should be part of security best practices.
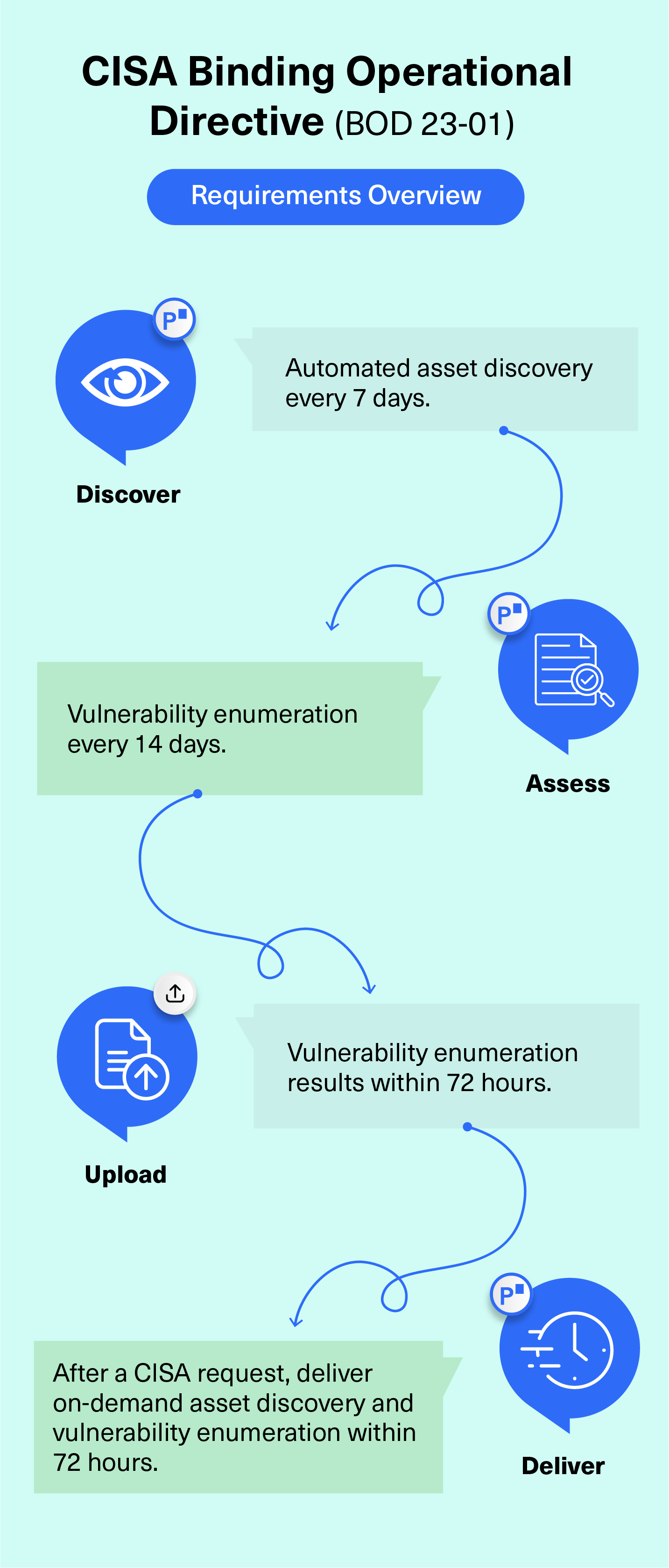
This mandatory directive asks federal departments, the executive branch, and agencies to:
- Perform automated asset discovery on all IPv4 assets every seven days.
- Initiate vulnerability enumeration across all discovered assets every 14 days.
- Upload vulnerability enumeration results into the CDM (Continuous Diagnostics and Mitigation) Agency Dashboard within 72 hours.
- Deliver on-demand asset discovery and vulnerability enumeration within 72 hours of receiving a request from CISA.
What to know:
The CISA BOD 23-01 requires that FCEB agencies build and maintain robust asset discovery and vulnerability enumeration capabilities with high-fidelity data of all assets. The discovery process must be scheduled both on predefined intervals and delivered on demand. The resulting data needs to be uploaded to the CDM Agency Dashboard regularly.
What to consider:
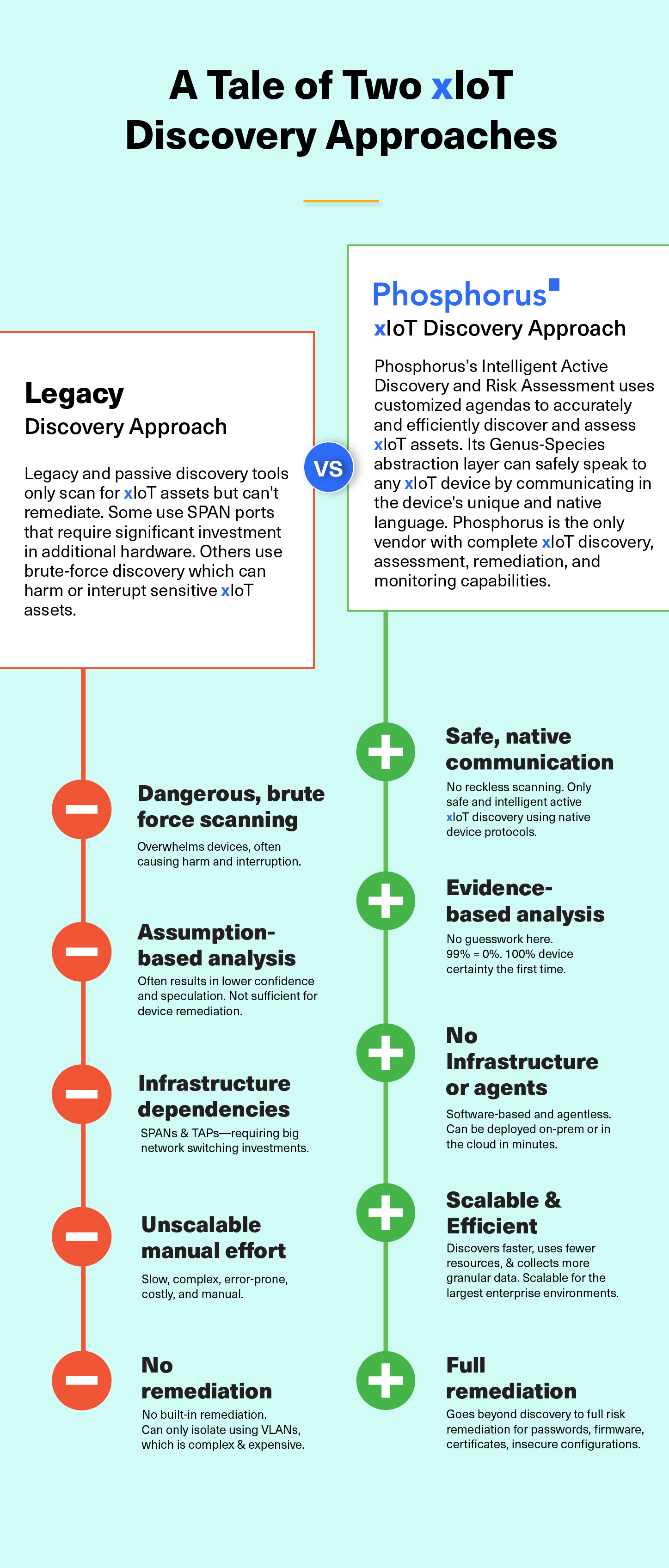
Most FCEB agencies use legacy Vulnerability Assessment or passive Asset Management tools for asset discovery and vulnerability enumeration. These kinds of tools are unsuitable for satisfying BOD 23-01 as they don’t have complete visibility into all network-connected assets in a network. Most specifically, given that xIoT devices and assets can comprise up to 20% of the network attack surface, traditional vulnerability and asset management tools won’t quite cut it here.
What to know:
Complete and accurate network visibility is the foundation of robust cybersecurity. Not only can it help you see what to protect, but it can also give organizations critical context around every asset that’s connected to their network. Without having an accurate, up-to-date inventory and risk assessment of everything on the network, it’s impossible to effectively protect your environments. But how do you get full visibility and posture assessment of all of your xIoT devices? (NOTE: our research shows that there are 2-3 xIoT devices per employee in an organization.)
What to consider:
Most organizations have invested heavily in the visibility of their traditional IT assets – like servers, laptops, workstations, routers, and switches. But they lack the comprehensive visibility into non-traditional xIoT assets—such as IoT devices (printers, cameras, door controllers, HVAC controllers), OT devices (PLCs, HMI’s, ICSs, robotics), IoMT devices (infusion pumps, wireless vital monitors, temperature sensors), and network devices (L2 switches, WiFi routers, NAS, UPSs).
Traditional vulnerability assessment and passive asset management systems do not and cannot discover most xIoT assets effectively and accurately. They frequently misclassify these assets and even harm or break them with brute-force scans. Furthermore, they typically take days, weeks, and even months to finish, making them unsuitable for on-demand asset discovery. FCEB departments and agencies need a fast, accurate, and safe xIoT asset discovery and risk assessment solution to have true visibility of their networks and overall attack surface.
How Phosphorus can help
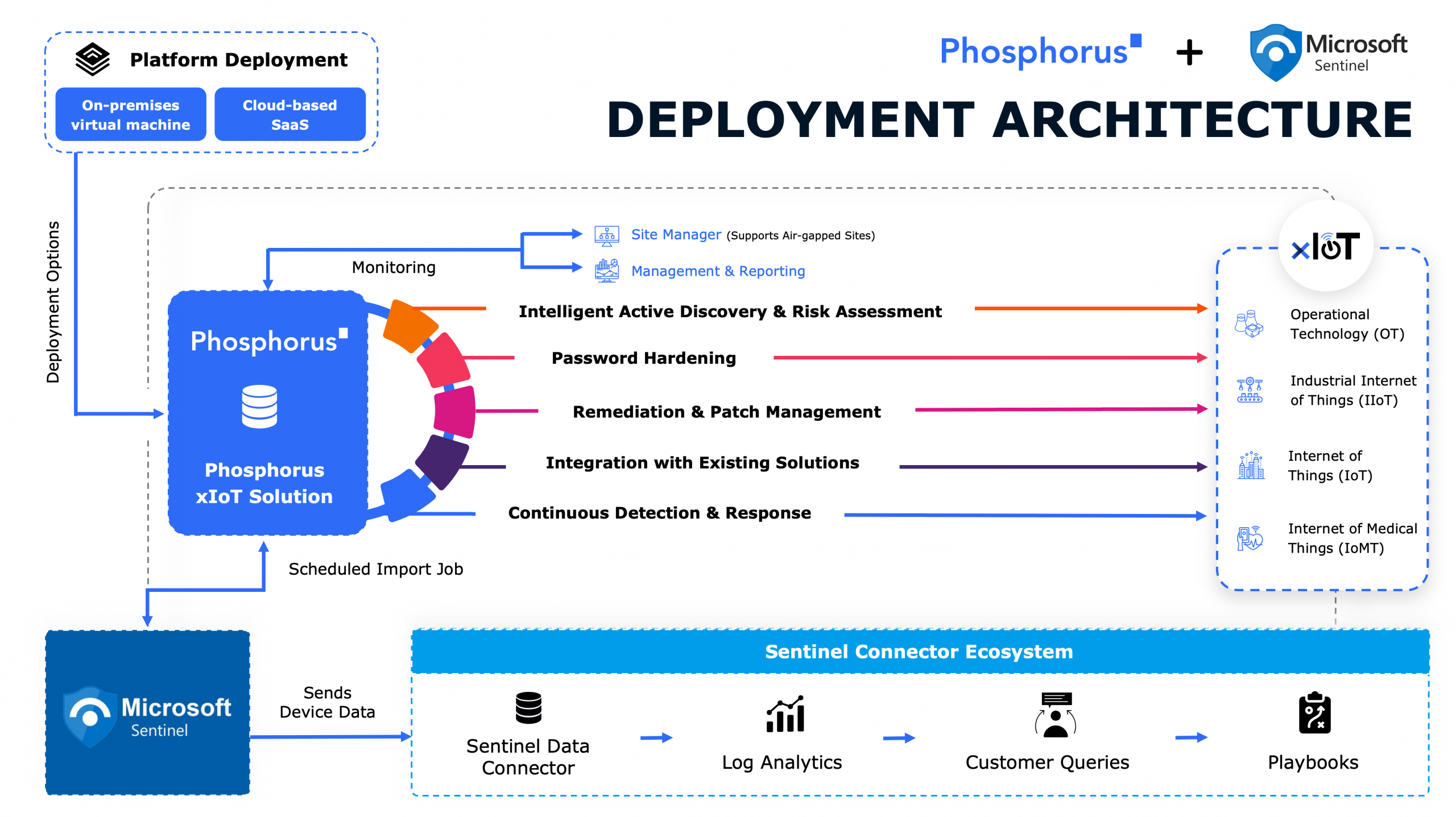
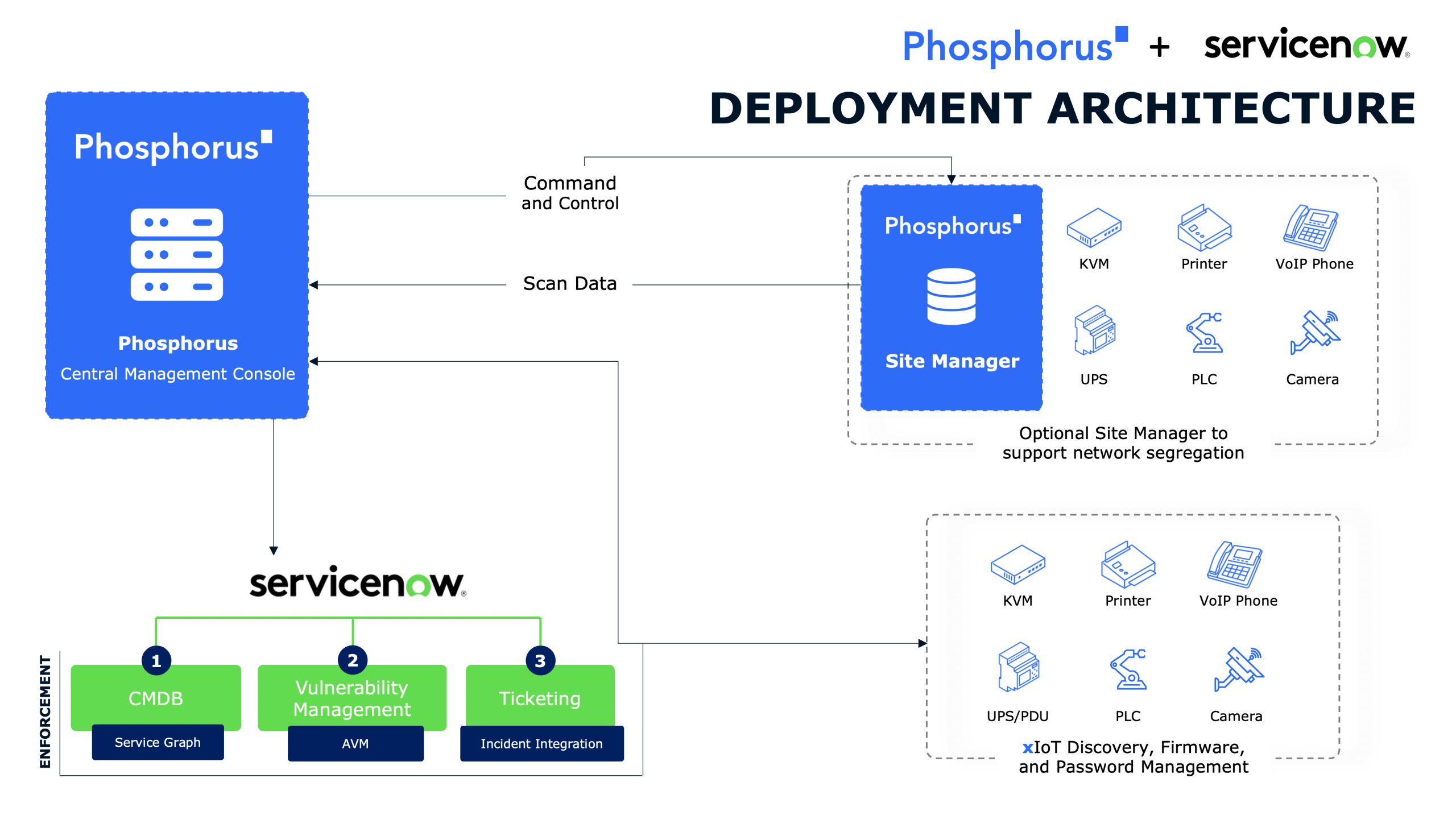
The Phosphorus Enterprise xIoT Security Platform is a comprehensive, agentless asset discovery, remediation, and monitoring solution for IoT, OT, IoMT, and Network device assets. It delivers complete visibility into xIoT environments – accurately, safely, and quickly. Once discovered, the platform identifies and classifies xIoT assets, assesses their risk posture, and automates a host of hardening and remediating actions. The platform also provides robust xIoT Detect & Response capabilities through real-time continuous monitoring and drift detection.
Full Discovery and Vulnerability Enumeration
The Phosphorus Platform delivers on-demand asset discovery and vulnerability enumeration of all xIoT assets. With its Intelligent Active Discovery (IAD) engine, Phosphorus can identify 100% of xIoT assets without interrupting them or impacting the operational availability of older, and more sensitive, assets like OT, ICS, and SCADA devices. Using customized discovery agendas, IAD deploys a tiered sequence of probes to ensure safe and fast discovery while using significantly less bandwidth – making the Phosphorus solution ideal for on-demand asset discovery and vulnerability enumeration.
The Phosphorus technology also identifies asset vulnerabilities and delivers full security posture assessment for xIoT assets. It can automatically remediate known vulnerabilities like weak and default passwords, outdated firmware, expired certificates, and insecure device configurations.
Contact us
Contact us here for information on how Phosphorus can help your organization meet BOD 23-01.
Author
John Vecchi
As Chief Marketing Officer, John brings more than 25 years of experience in high-tech marketing, strategy, product marketing, product management, sales and consulting. Most recently, John was Chief Marketing Officer at Anitian, ColorTokens, and Anonyome Labs.