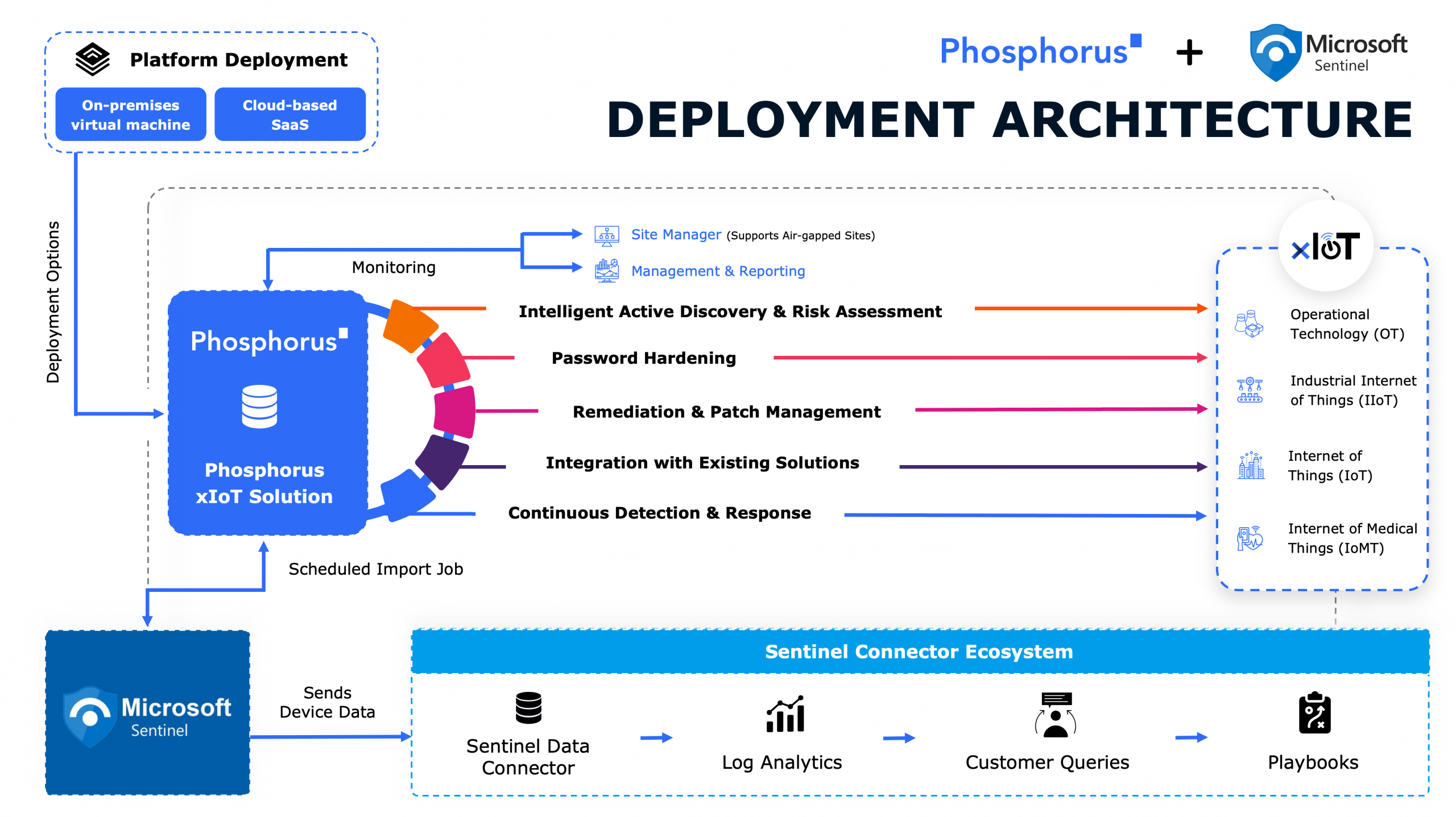
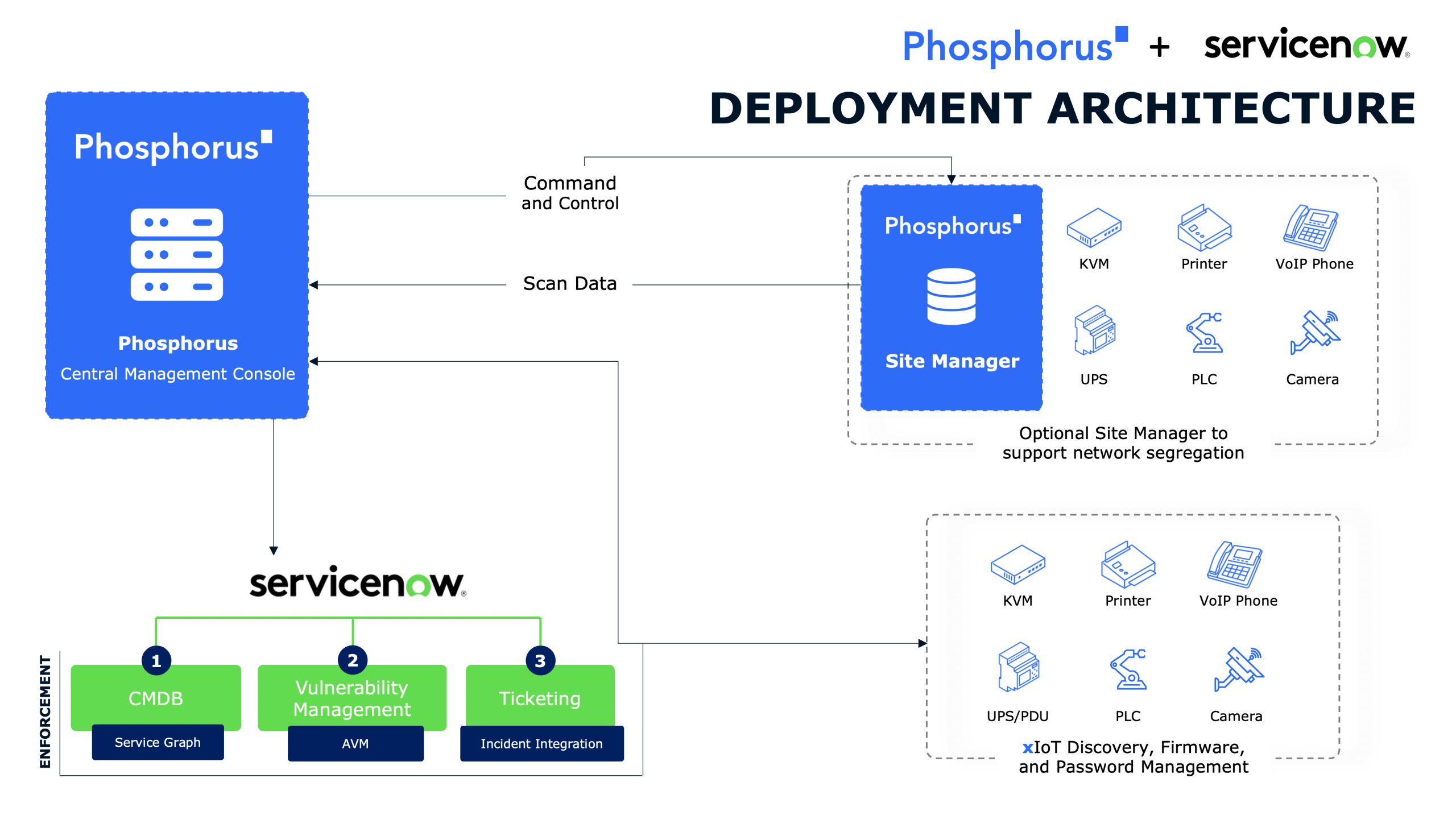
A Chinese government-linked threat group has reportedly infiltrated critical US networks, this time focusing on internet service providers (ISPs) to gather sensitive data and potentially initiate cyberattacks. According to a Wednesday report from The Wall Street Journal, citing sources familiar with the matter, the group—identified as Salt Typhoon—has gained access to the IT systems of several ISPs in recent months.
“It’s likely we’re going to see more of these Typhoon variants,” John Terrill, CISO of Phosphorus Cybersecurity, told Security Boulevard.
“In the past, the expectation for cybersecurity teams was to build defenses to the level of capabilities of the expected attacker, which was normally hacktivists and criminals. With the increasing amount of Typhoon activity across multiple industries, I think we’re facing a new expectation that we may all have to start increasing our cybersecurity programs to account for nation-states.”
Could Salt Typhoon affect OT environments in other areas of infrastructure? At this point, Terrill tells Industrial Cyber, it’s too early to say.
“At the moment, Salt Typhoon is limited to internet service providers that could definitely be considered critical infrastructure. ISPs don’t tend to have a lot of traditional OT environments but that doesn’t mean those environments aren’t being targeted. The same issues plaguing ISPs are plaguing companies at every level of our supply chain with the same vulnerabilities we continue to see: default credentials, lack of patching, weak passwords, etc,” he added.
Aside from potential disruption, Terrill says that nation-states might target ISPs “either as a pivot point into another environment or a collection point for a lot of data that traverses their infrastructure. It’s why when you’re thinking about attacker personas and capabilities, you don’t worry that much about breaking encryption – unless you’re worried about nation-states.”
“The joke in the hacker community is that ‘math is hard,’ insinuating that you go after the endpoint as the data is already decrypted by that point.”