Recent revelations about a novel malware strain named FrostyGoop have sent shockwaves through the cybersecurity community, particularly those involved in securing and operating Industrial Control Systems (ICS). FrostyGoop represents a significant escalation in the threat landscape, leveraging the Modbus TCP protocol to disrupt operations and potentially cause far-reaching Cyber-Physical consequences across most every industrial sector.
The Anatomy of the Attack
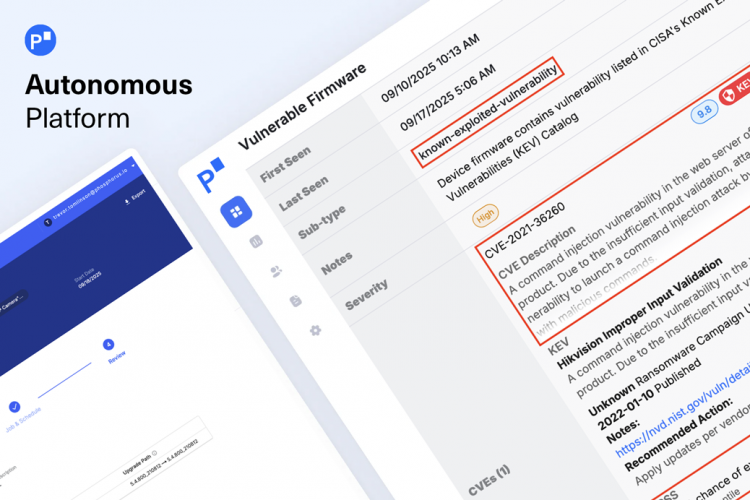
FrostyGoop’s attack sequence is both sophisticated and alarming in its simplicity. The initial access point is a vulnerable MikroTik device, which serves as the gateway for deploying the malware. Once inside the network, FrostyGoop sends commands downstream to heating/cooling system controllers known as ENCO devices, downgrading their firmware to versions that lack critical monitoring features. [NOTE that in order to downgrade the firmware, the attackers likely exploited common IoT/OT security vulnerabilities like default or weak device passwords.] This downgrade is not just a minor inconvenience—it manipulates data on these devices to report faulty measurements, leading to the shutdown of heating systems and leaving civilian customers without heat.
A New Frontier in Modbus Protocol Exploitation
One of the most concerning aspects of FrostyGoop is its pioneering use of Modbus TCP communications in the cyberattack. Modbus, a communication protocol widely used in ICS environments, allows devices to communicate over TCP/IP networks. FrostyGoop’s ability to send commands to read or modify data on Modbus devices marks it as one of the first known attacks of its kind. This capability is not restricted to ENCO HVAC systems but can extend to any ICS device – modern or legacy – utilizing the Modbus protocol. This broad applicability underscores the far-reaching potential of FrostyGoop to disrupt mission-critical operations worldwide.
Technical Capabilities of FrostyGoop
FrostyGoop’s advanced nature is demonstrated through its wide array of technical abilities, including:
- Accepting command-line execution arguments for flexible deployment
- Using configuration files to detail target IP addresses and Modbus commands
- Communicating directly with ICS devices via the Modbus TCP protocol
- Issuing Modbus commands to read or alter data on ICS devices
- Logging output data either to a console or to a JSON file for analysis
These sophisticated features enable FrostyGoop to carry out precise and destructive attacks on targeted ICS infrastructure, emphasizing the necessity for stringent security measures.
The Importance of Fundamental Cyber-Physical System Security Hygiene
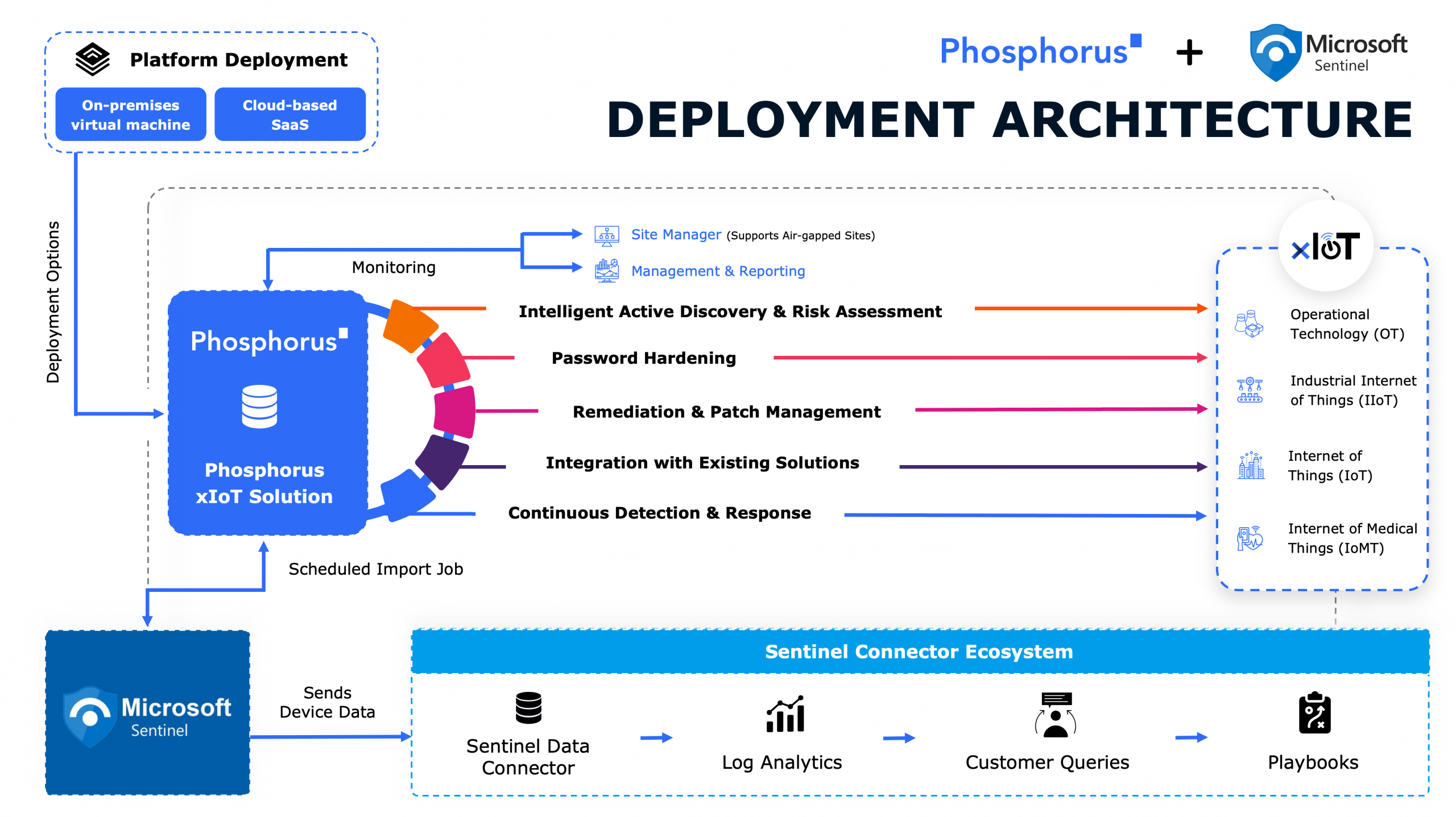
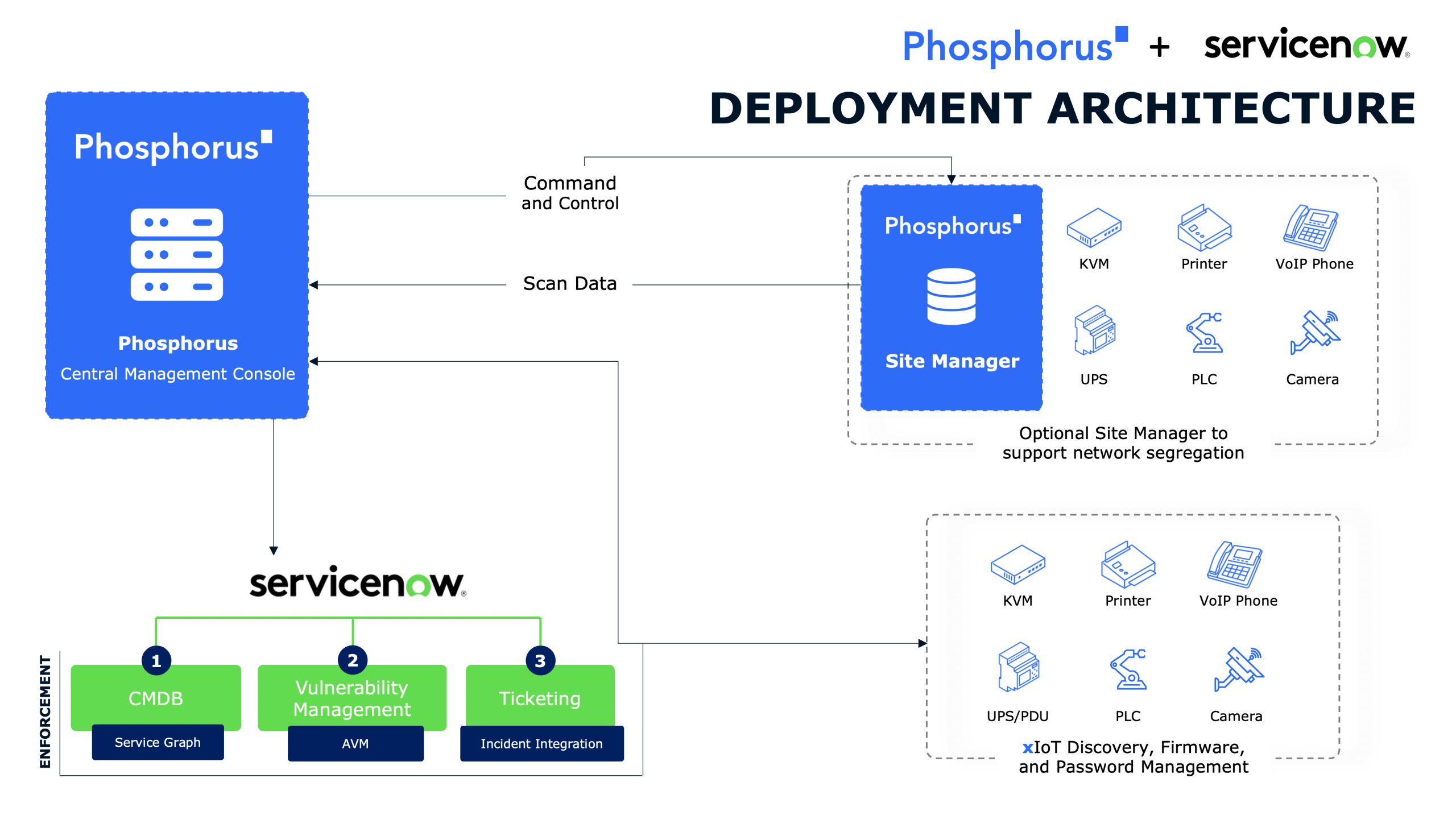
The FrostyGoop incident highlights a critical issue within ICS environments: the failure to implement even the most fundamental security hygiene and controls. But it’s also critical to understand that those security controls need to apply to the entire xTended IoT (xIoT) environment and attack surface, not just to OT-specific devices. For example, there will always be “OT-adjacent” IoT systems – such as Industrial Gateways – that also need attention from a security hygiene perspective, particularly since they can have an outsized impact on operational disruption downstream.
Here are the key IoT/OT vulnerabilities exploited by this and most xIoT malware:
- Default Credentials: Over 70% of ICS devices are operating with default passwords, making them easy targets for attackers.
- Wide-Open Ports/Protocols: Exposing ICS devices to the internet without proper security measures invites exploitation.
- Old/Unpatched/Vulnerable Firmware: Running vulnerable and unpatched firmware increases the risk of vulnerabilities being exploited.
Addressing these issues is paramount to protecting ICS infrastructure from threats like FrostyGoop. Organizations must prioritize securing their devices by ensuring that passwords for ICS devices in scope (as well as OT-adjacent IoT devices) are rotated on a schedule, that configurations are hardened and internet exposure is restricted, and that device firmware is up-to-date and patched regularly. And note that patching those OT-adjacent IoT devices will often be on a different cadence than traditional ICS/OT devices.
Conclusion
FrostyGoop serves as a stark reminder of the evolving threat landscape facing ICS environments. Its ability to exploit the Modbus TCP protocol and disrupt operations across various industrial and public safety sectors is a wake-up call for organizations to bolster their cybersecurity defenses. Implementing basic security hygiene measures and staying vigilant against such threats is not just recommended—it is essential for safeguarding the critical infrastructure that our modern world depends on.
As outlined by Gartner in last year’s inaugural Market Guide for CPS Protection Platforms:
“Operational systems are deployed with their default credentials unchanged,” “Ports on all kinds of systems in all kinds of remote locations are wide open,” and “The number of vulnerabilities continues to grow at the same time as CPS patching remains very difficult.”
As we continue to monitor and respond to Cyber-Physical threats like FrostyGoop, Sandworm, and Pipedream (to name a few), the importance of efficient, safe, and proactive IoT and OT security management to help prevent breaches and protect our critical infrastructure cannot be overstated.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.