Comprehensive xIoT Security Management for Energy & Utilities
Key benefits of the Unified xIoT Security Management Platform
See every xIoT device. Secure every xIoT device.

100% Safe

Simple & Fast

Maintain Compliance

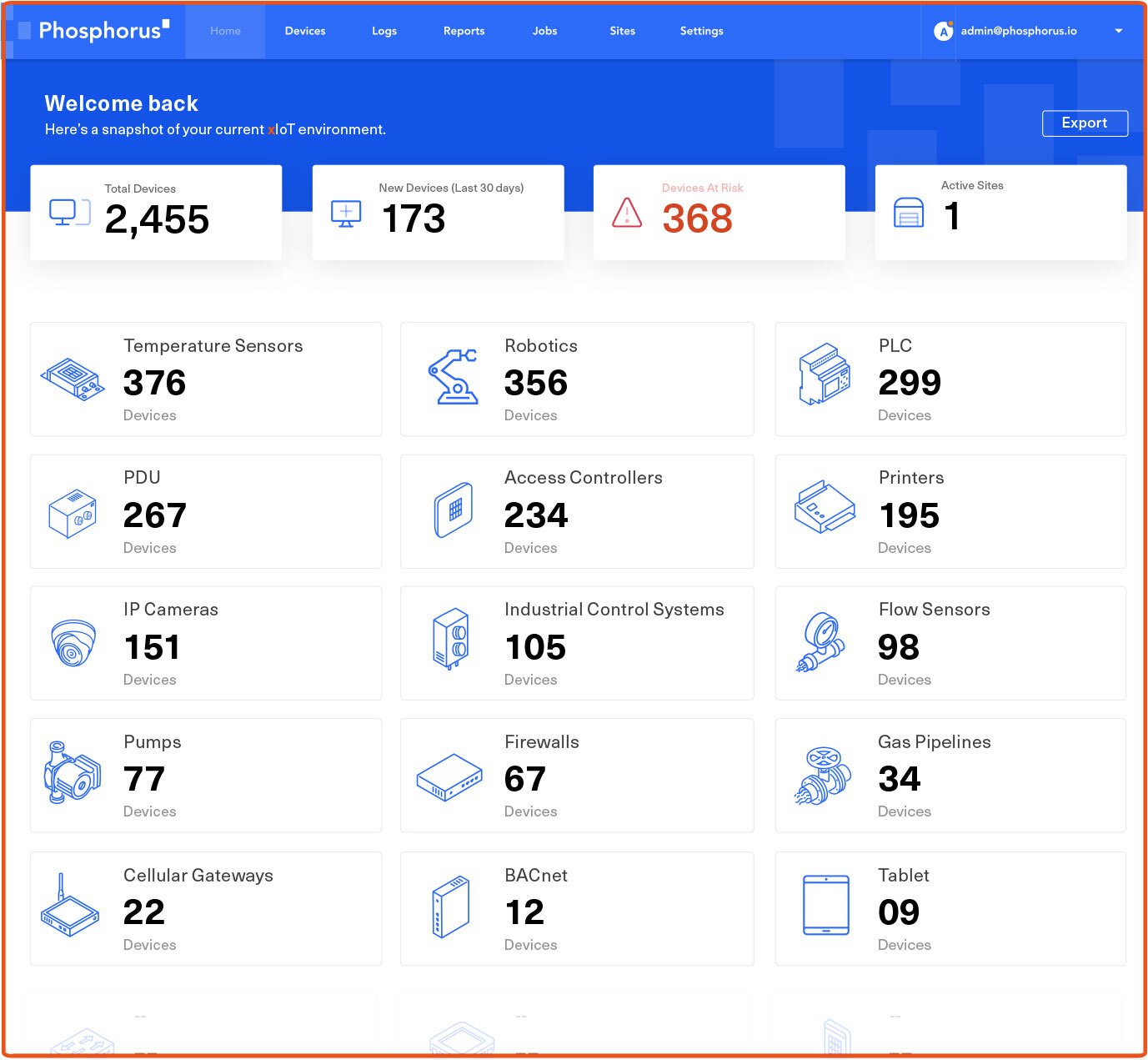
100% Visibility

Monitor Anything

Log Anything

Remediate Your Way
The challenge
OT, ICS, and SCADA systems are an essential and mission-critical part of utilities, energy, and oil & gas companies. But because they were historically air-gapped, they have fewer built-in protections and are more vulnerable to attacks and ransomware. And, the lack of scalable, cost-effective, and prevention-based xIoT security solutions means that securing these sensitive and mission-critical cyber-physical systems and assets is slow, complex, error-prone, costly, and manual – due to the resource and infrastructure dependencies of legacy scanners and passive discovery solutions.
xIoT Visibility:
Legacy active solutions fail with OT/ICS and SCADA assets primarily because of their intrusive, brute-force device scanning approaches that result in disrupted or dramatically degraded operations. Legacy passive discovery solutions are dependent on network monitoring to perform discovery, resulting in limited visibility, inaccurate inventory, long mean-time-to-inventory, infrastructure dependencies, and high network performance impact.
xIoT Risk Reduction:
The lack of safe, prevention-based xIoT security solutions for energy, utilities, and oil & gas environments means that organizations have had no ability to find, identify, and prevent OT, ICS, and SCADA system security risks, let alone meet the key cybersecurity recommendations set forth by the Department of Energy. This includes best practices for security, such as continuous monitoring & alerting, changing default cyber-physical system passwords, or fixing risky configurations on embedded devices.
xIoT Monitoring & Automated Alerts:
One of the biggest challenges for long-term xIoT security in critical infrastructure and OT environments is ‘environmental drift,’ which inadvertently diminishes device security.



The Phosphorus
Safe
Oh. So. Safe.
Device SAFETY is the foundational characteristic of the Phosphorus platform and approach. No brute-force scanning here. Only safe and intelligent active xIoT discovery using native device protocols.


Fast
Oh. So. Fast.
See complete xIoT discovery results in a fraction of the time as it happens. Using Customized Agendas, Phosphorus IAD generates tiered probe sequences designed to increase the speed of discovery, while dramatically reducing unnecessary traffic on the network.
Accurate
Oh. So. Accurate.
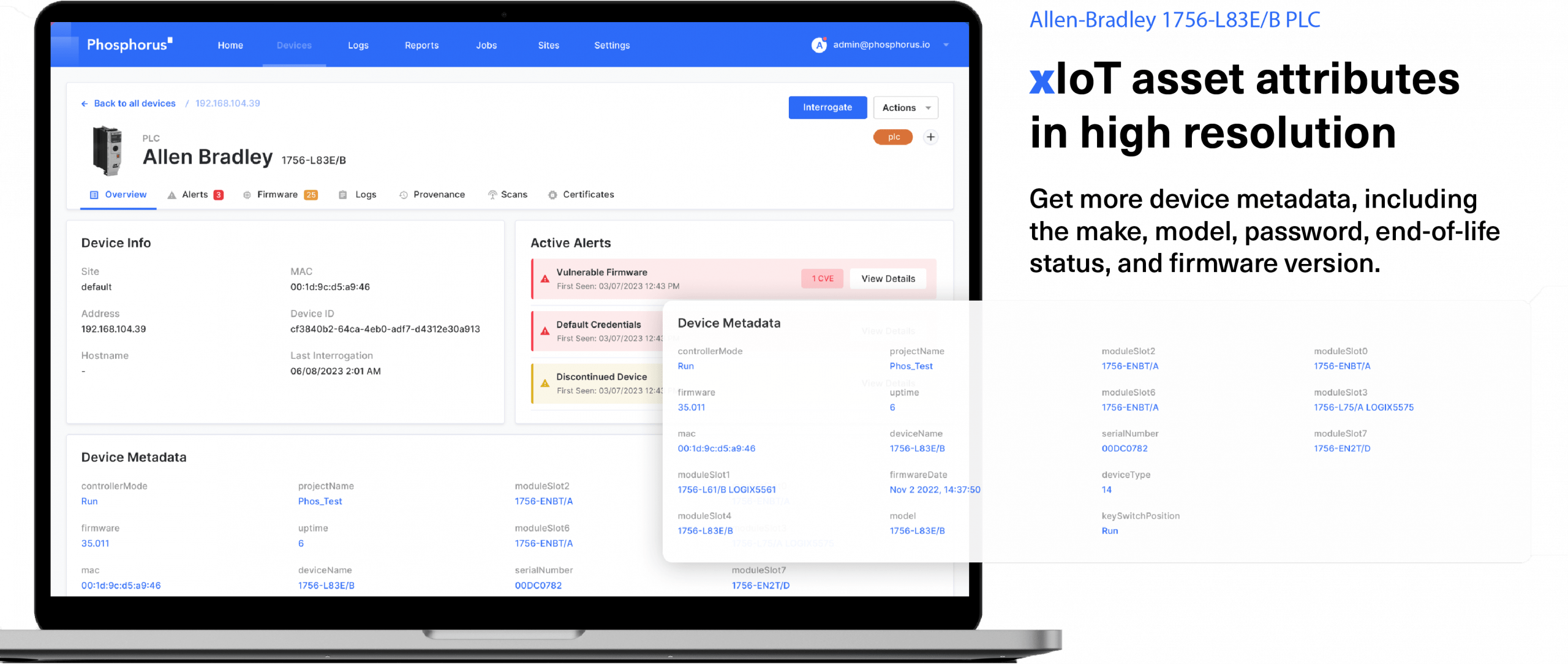
Complete xloT estate visibility and posture assessment. Phosphorus collects deep, granular device metadata to provide 100% device certainty the first time, every time.


Real-Time
Monitor Anything
Monitor OT/ICS/SCADA device state to detect and alert on configuration or environmental drift. Keep an eye on on-site changes, like the ol’ “paper clip reset” or resets to factory settings, while looking for new or rogue devices being added to your network.
Proactive
Remediate Your Way
The power to harden and remediate OT and ICS device vulnerabilities is at your fingertips. Whether it is default credentials, open and risky ports, End-of-Life and assets, or critical firmware patching, harden or remediate devices with full control–ensuring the safety of the entire OT/ICS/SCADA environment.

xIoT BREACH PREVENTION FOR ENERGY & UTILITIES
Common Use Cases
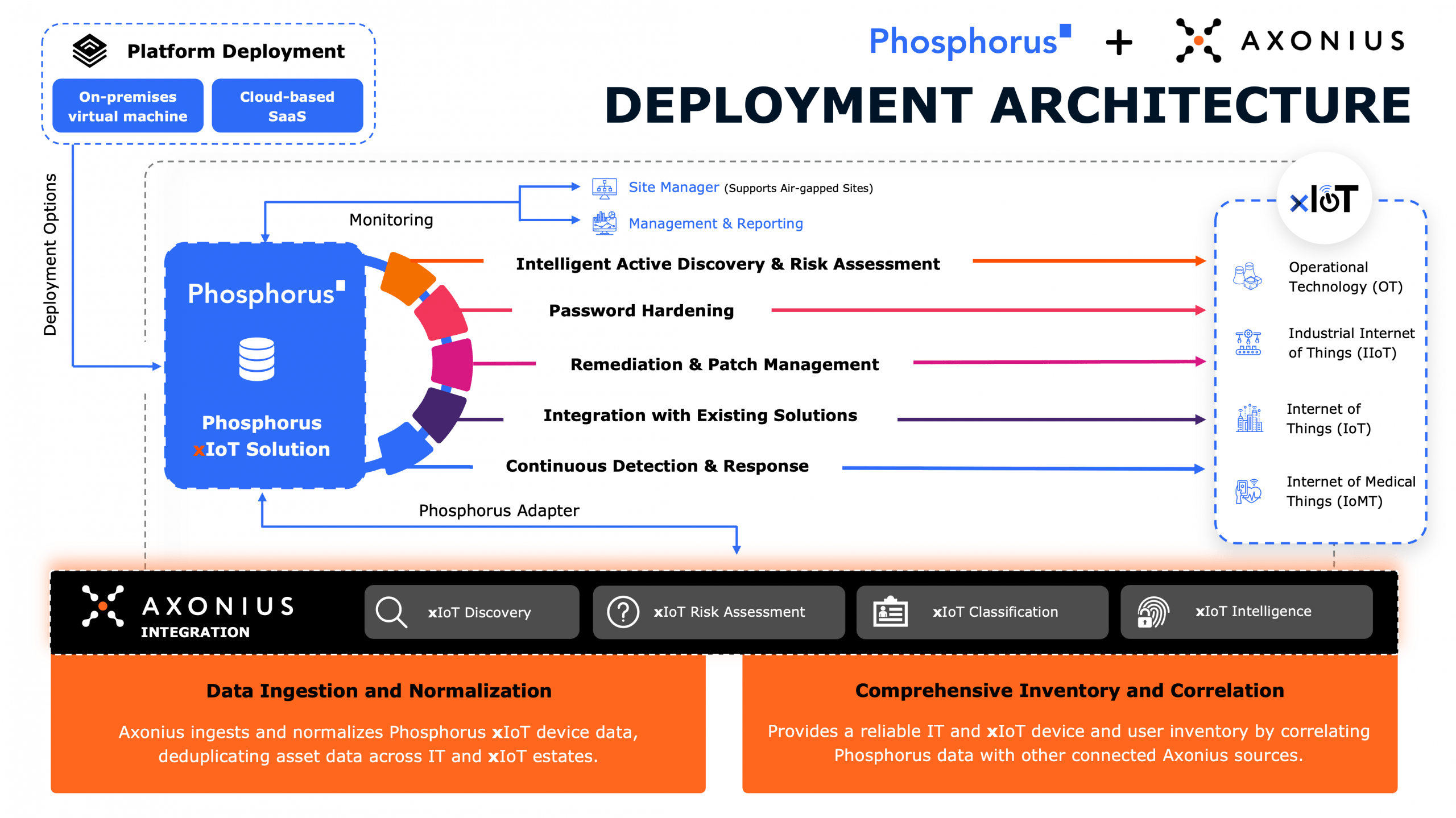
Intelligent Active Discovery & Risk Assessment

Password Hardening, Device Hardening, & Isolation

Remediation & Patch Management

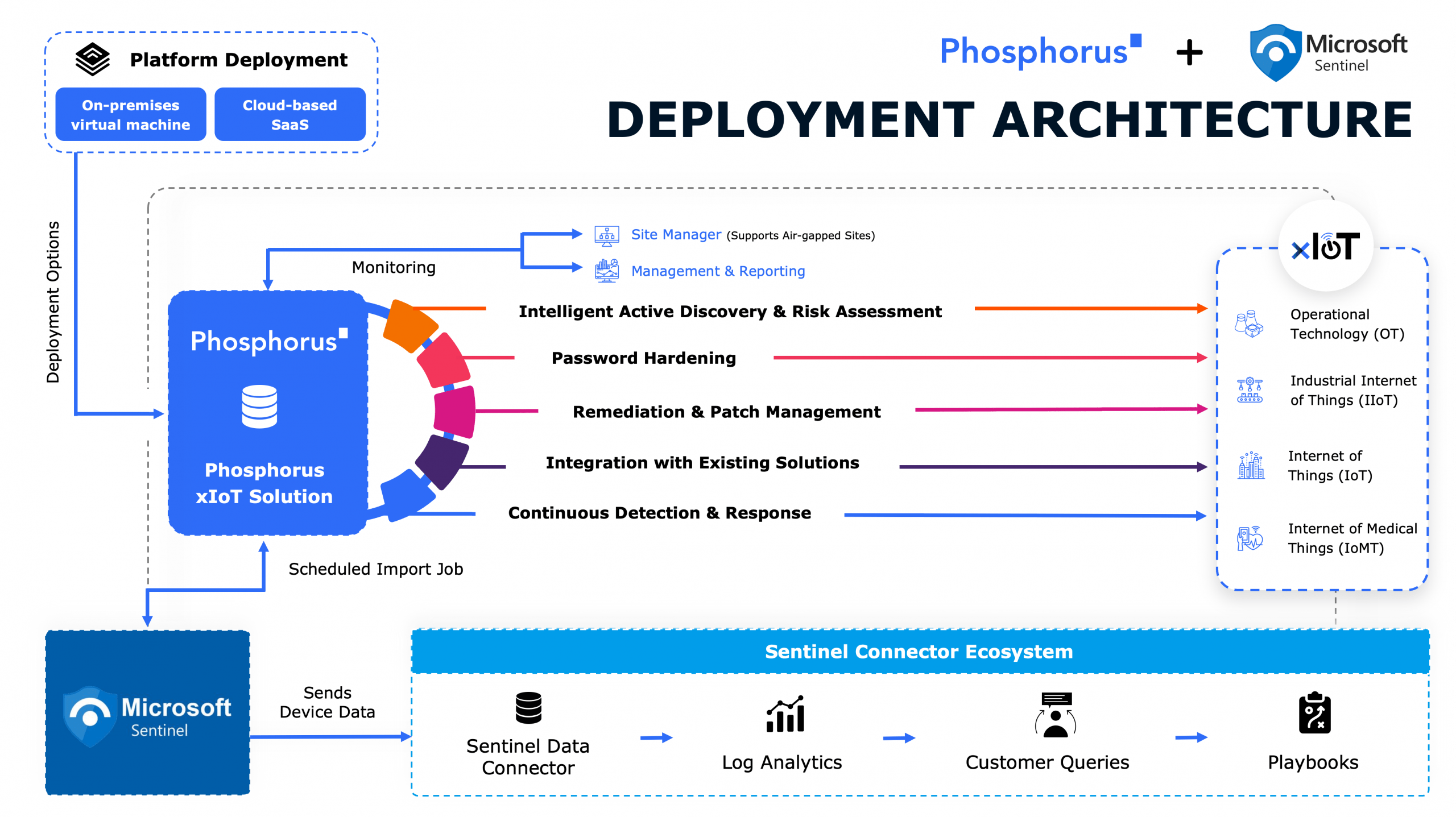
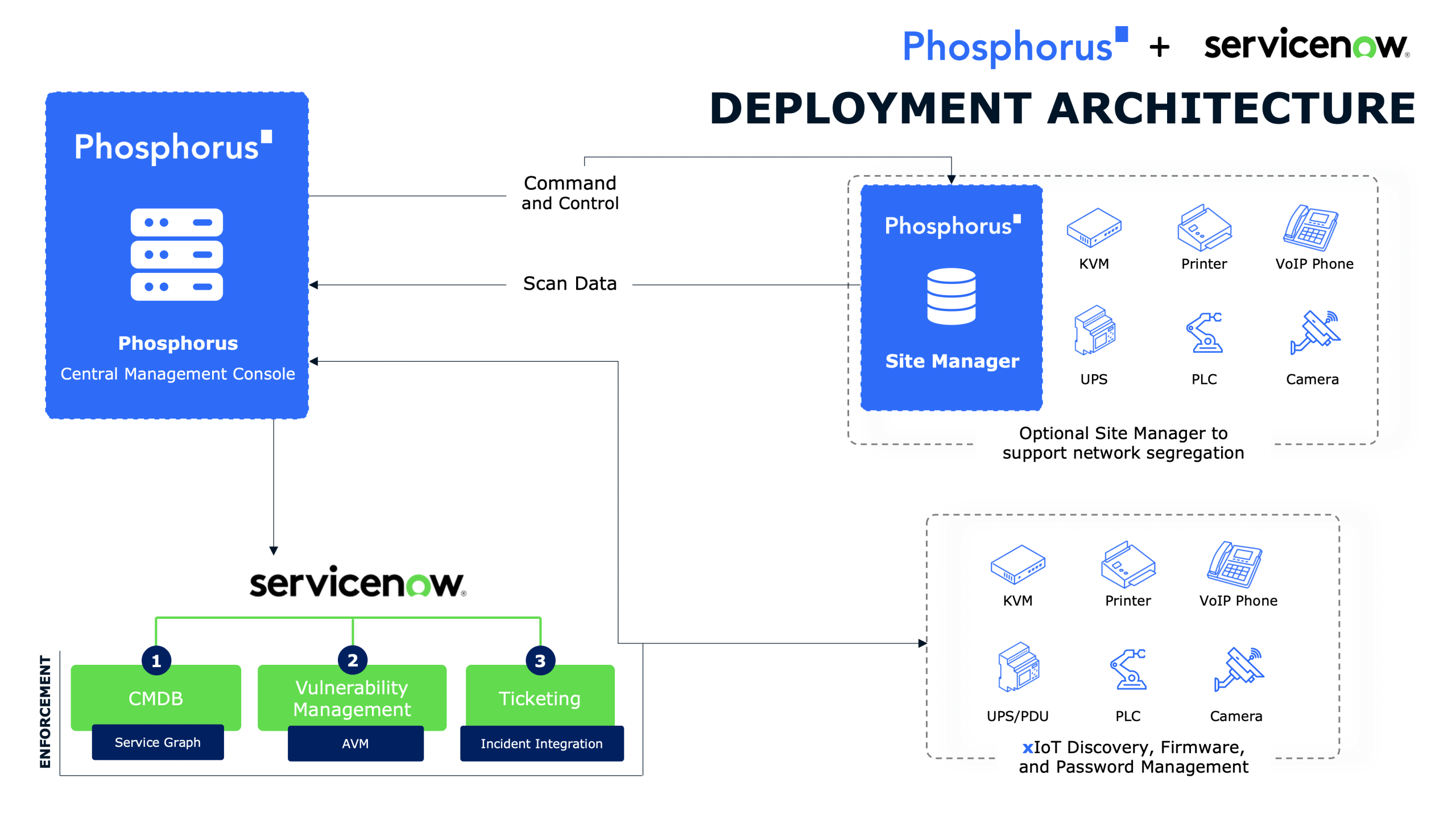
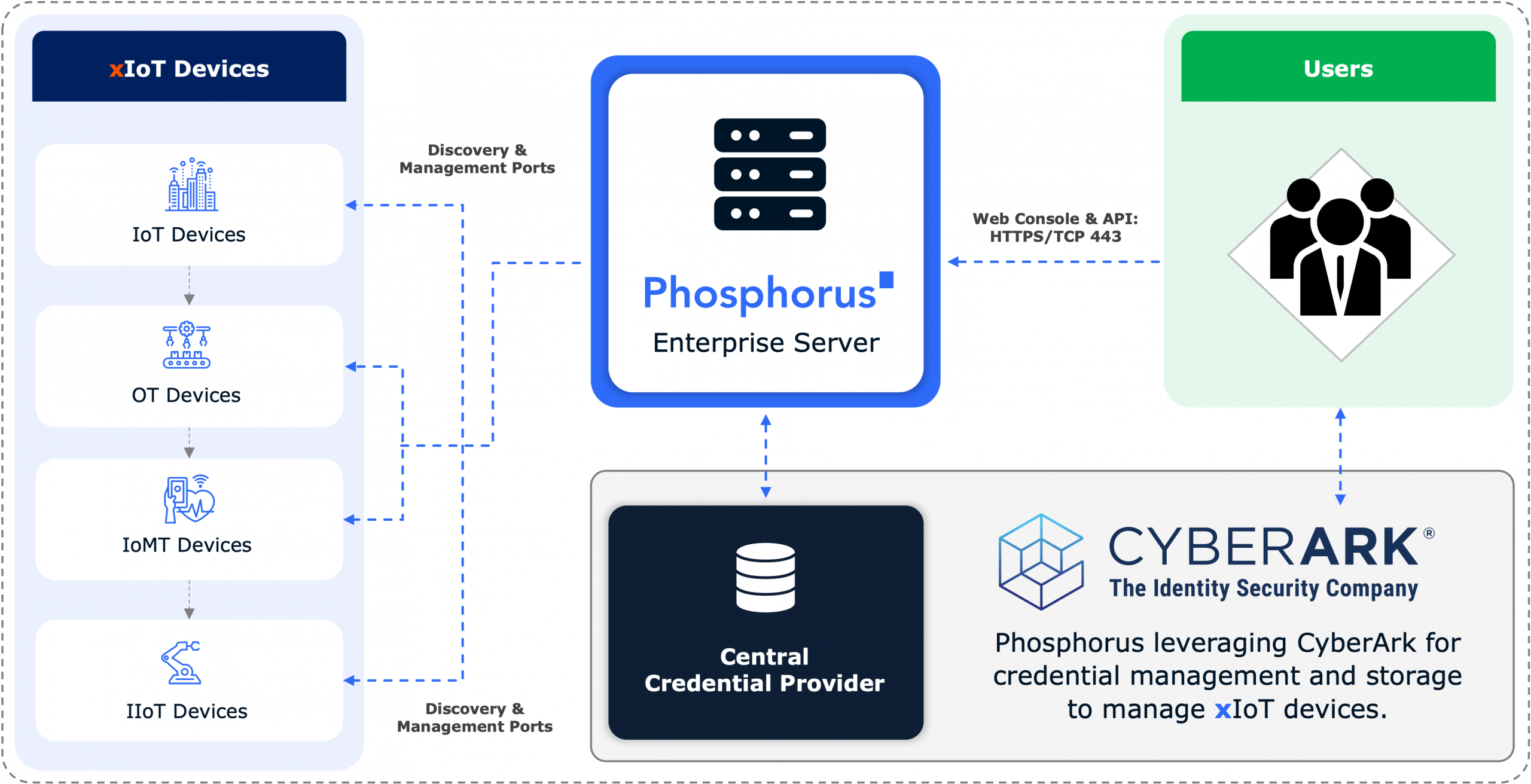
Integration with Existing Solutions

Continuous Monitoring & Management
Explore the Phosphorus Unified xIoT Security Management Platform
Discover & identify IoT, OT, and IIoT devices safely, accurately, and without impacting them.
Assess & show risk posture of xIoT devices by identifying weak credentials, end-of-life assets, CVEs, expired certificates, or
out-of-date firmware.
Continuous monitoring & management of IoT, OT, and IIoT devices for environmental drift or compliance with existing regulations.
Integrate with existing IT infrastructure like PAM, SIEM, and SOAR for rapid ROI.
Remediate vulnerabilities with full control at your fingertips, while maintaining the control needed in sensitive environments.