Did You Know Your Office Camera Could Be a Cybercriminal’s Backdoor?
Let us set the stage. Imagine this: Your cybersecurity team has deployed top-tier endpoint detection and response (EDR) solutions, successfully blocking a ransomware attack before it spreads. Phew. We all breathe a metaphorical sigh of relief – until the attackers find another way in.
Through a security camera.
According to cybersecurity firm S-RM, a recent Akira ransomware attack exploited an unsecured and unmanaged IoT device – an IP webcam – to bypass traditional security tools. This attack exposes a critical blind spot in enterprise security: IoT devices that aren’t actively monitored or protected.
S-RM’s Steve Ross, director of cybersecurity for the Americas, told the publication IT-Brew about the attack that cybersecurity professionals need to get better at thinking outside the box and locking devices down. “We are getting better at security,” he says, “but they’re pretty driven, too, and so they’re going to find whatever that vulnerability is, and in this case, it’s a webcam.”
Let’s break down how it happened and what you can do to help your business avoid being next.
Who or What Is Akira, and Why Is It Targeting IoT?
The Akira ransomware gang is a cybercriminal group known for demonstrating significant adaptability and technical prowess in targeting Linux, Windows, and ESXi systems. Initially focused on Windows systems, the group evolved to encrypt files on Linux servers and VMware ESXi hypervisors, aiming to disrupt enterprise environments and maximize ransom payments.
Their latest move? Scanning for unsecured devices and targeting IoT – like cameras, printers, and routers – that lack basic security hygiene, allowing them to infiltrate networks undetected.
How Hackers Used an IoT Camera to Deploy Ransomware
In a recent case, Akira ransomware operators attempted to deploy malware onto an enterprise network. Their initial attack was blocked by EDR, preventing them from encrypting files on a Windows server.
So they pivoted. Here’s how.
(Watch us break it down with James McCarthy and staff engineer Chris Prest on Phosphorus LIVE here.)
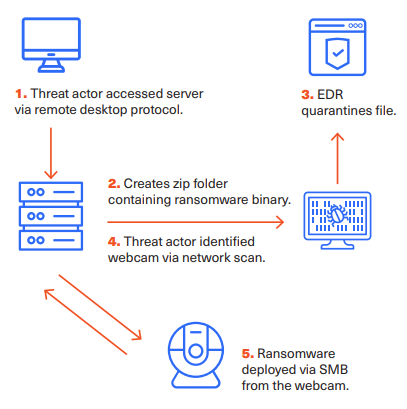
Step 1: Reconnaissance – Using a simple scan, the attackers identified an unsecured IP webcam on the same network.
Step 2: Exploitation – The webcam lacked firmware updates and secure authentication, allowing attackers to gain remote shell access.
Step 3: Installation – With direct control over the camera, the group used it as a launchpad to execute their Linux ransomware encryptor.
Step 4: Lateral Movement – The ransomware spread through the network by targeting shared Windows SMB file shares and encrypting critical data.
The result? A successful ransomware deployment. Despite not being joined to Active Directory, the web camera was able to compromise an Active Directory service.
Why Can IoT Devices Be Such a Cybersecurity Risk?
Most companies focus on securing traditional endpoints (laptops, servers, workstations) but overlook the growing number of IoT, OT, and IoMT devices connected to their networks. What’s the problem? These devices often have:
Default or weak credentials, often never changed from factory settings
Out-of-date firmware with known vulnerabilities
Lack of EDR or antivirus compatibility
Risky configurations with unnecessarily open ports and protocols, like Telnet, SSH, or Bluetooth
This makes unmanaged IoT devices an ideal entry point for ransomware gangs like Akira. But there’s good news, too. The right proactive security measures can help to mitigate these risks.
Why Doesn’t Traditional Endpoint Security Work with IoT?
Most enterprises rely on EDR, antivirus, and traditional IT security tools to protect their networks. But, uh oh, there’s a significant flaw – these solutions were never designed for IoT. They were designed to protect conventional IT assets like servers, desktops, and laptops.
Here’s why traditional endpoint security fails when it comes to the rapidly expanding landscape of IoT/OT/IoMT:
1. Lack of Built-in Security Features
Unlike your traditional IT systems, many purpose-built IoT devices are developed with minimal security considerations. They often lack basic security features, making them more susceptible to cyber threats.
2. Diverse Operating Systems and Architectures
IoT devices operate on a wide range of platforms and architectures, many of which are proprietary or specialized. This diversity makes it challenging for standard endpoint security solutions, which are typically designed for common operating systems, to be effectively deployed across all IoT devices.
3. Resource Constraints
Many IoT devices have limited processing power, memory, and storage, as they’re constructed with a singular purpose and targeted cost in mind. These constraints make it impractical to run traditional security software, which can be resource-intensive, on such devices without impacting their primary functionalities.
4. Network Exposure
IoT devices are often deployed in environments where they are directly exposed to the internet or untrusted networks, increasing their vulnerability to attacks. Traditional endpoint security measures may not account for the unique network configurations and exposures inherent to IoT deployments.
5. Infrequent Updates and Patching
Manufacturers of IoT devices may not provide regular firmware updates or patches, leaving known vulnerabilities unaddressed. Traditional endpoint security relies on regular updates to protect against emerging threats, a practice not consistently applied in the IoT realm.
6. Scalability Challenges
The sheer number of IoT devices within an organization can be overwhelming. Managing and securing thousands or even millions of devices require specialized solutions that can scale effectively, a challenge for traditional endpoint security systems.
The takeaway? IoT security requires a different approach – one that goes beyond endpoint security to actively manage, harden, and monitor every IoT, OT, and IoMT device.
5 Steps to Help Prevent IoT-Based Ransomware Attacks
To protect against attacks like this one, businesses must begin by proactively securing their IoT environment. (Get more detail on the attack and tips for preventing attacks with the transcript to “Akira & the IoT Blind Spot: EDR Won’t Save You” here.) Here’s how:
Find & Assess Every IoT Device
- Conduct a full asset inventory to identify all IoT devices connected to your network.
- Use automated and safe IoT discovery systems to detect shadow IT devices.
- Assess each device’s security posture, including firmware status, default credentials, and network exposure.
Disable Unused Protocols & Secure Configurations
- Reduce the attack surface by shutting off unnecessary services and ports (e.g., Telnet, SSH, Bluetooth).
- Ensure devices follow secure configuration management best practices.
Change Default Credentials & Enforce Strong Passwords
- Ensure all IoT devices use unique, complex passwords.
- Implement automatic credential rotation to prevent unauthorized access.
Patch & Update Firmware Regularly
- Stay ahead of vulnerabilities by monitoring CVEs related to IoT devices.
- Apply firmware updates as soon as they’re released.
Monitor & Detect IoT Network Anomalies
- Deploy continuous monitoring for suspicious IoT activity.
- Set up automated alerts for unauthorized access attempts.
Final Thoughts: Don’t Let IoT Be Your Weakest Link
As we like to say, you’re only as strong as your weakest link, so Every Device Counts. This Akira ransomware attack should be a wake-up call: IoT devices are no longer a niche cybersecurity concern; they’re a significant attack vector. Organizations must go beyond traditional endpoint security and take proactive steps to find, fix, and monitor IoT, OT, and IoMT Cyber-Physical Systems before attackers exploit their vulnerabilities.
Want to know how vulnerable your IoT environment really is? Run a free IoT security assessment workshop with Phosphorus today.
Contact us to learn how we can help secure your IoT devices against emerging threats.
Join the Conversation
Follow us on LinkedIn, BlueSky, and YouTube to stay informed about the latest IoT security trends, CPS protection strategies, and IoT threat intelligence.
Join us above for a special edition of Phosphorus LIVE. Sign up for ongoing sessions here.
Learn:
🔹 Why EDR fails for IoT threats
🔹 How hackers are using unmanaged devices to spread ransomware
🔹 What the industry must do to stop this growing trend
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.