Just last week, CISA confirmed that the systems exploited in the attack on the Municipal Water Authority of Aliquippa were Unitronics programmable logic controllers (PLCs). These PLCs are used in the water and wastewater sector to “control and monitor various stages and processes of water and wastewater treatment, including turning on and off pumps at a pump station to fill tanks and reservoirs, flow pacing chemicals to meet regulations, gathering compliance data for monthly regulation reports, and announcing critical alarms to operations.”
In its advisory, CISA urged water utilities using Unitronics PLCs to take some of the following protective measures:
- Change the Unitronics PLC default password—validate that the default password “1111” is not in use.
- Require multifactor authentication for all remote access to the OT network, including from the IT network and external networks.
- Disconnect the PLC from the open internet.
- If possible, utilize a TCP port that is different than the default port TCP 20256. Cyber actors are actively targeting TCP 20256.
- Update PLC/HMI to the latest version provided by Unitronics.”
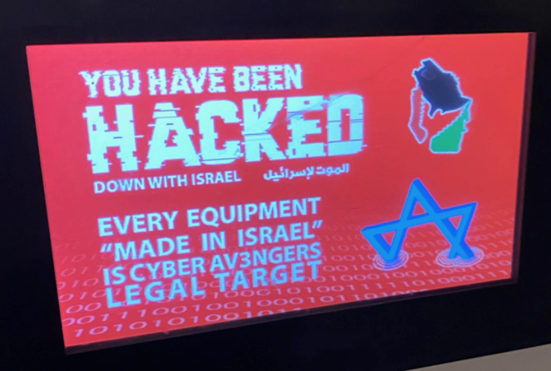
The WaterISAC’s discussion of the incident is based on open-source news reports in which they summarize without much explanation. The ISAC did express that ” the news site has posted an image stating it was submitted by the water authority. The image suggests the attacker’s message is displayed on the system that was compromised with the Unitronics device and model (V570).”
Below is the image believed to have been displayed on compromised systems.
Recently, the National Security Agency (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) released a joint cybersecurity advisory (CSA) highlighting the most common cybersecurity misconfigurations in large organizations. Among the agencies’ list of the Top 10 most common misconfigurations were many risks which both Phosphorus and its research wing Phosphorus Labs have been warning about since bringing its Gartner-recognized CPS Protection Platform to market. These include default configurations, insufficient monitoring, poor patch management, poor credential hygiene, and more.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.
Related Posts
Introducing the Phosphorus xIoT Compliance Report Phosphorus is introducing a new capability that changes...
The U.S. Coast Guard’s enforcement of 33 CFR Part 101, Subpart F draws a...


