OT Asset Inventory: The Fastest Path to 100% Visibility
Every day, organizations operate with thousands of connected devices. An alarming portion of them sit outside active management.
According to recent research, devices classified as unmanaged or agentless now represent 42% of all enterprise assets, and they drive 64% of mid-to-high level enterprise risk.
Even more stark: 80% of organizations can’t identify the majority of their IoT, OT, IoMT, or IIoT devices.
The good news is, gaining a complete picture of your OT asset inventory is well within reach. In this blog, we’ll talk about the different methods of reaching 100% visibility in your OT asset inventory and why Intelligent Active Discovery (IAD) is the key to keeping your organization safe.
Why Traditional OT Asset Inventory Fails
Traditional OT asset inventory can’t keep up with the demands of today’s enterprise environments. Here’s why:
- Most OT environments still rely on the same asset inventory methods used a decade ago, including SPAN ports, passive listening, or spreadsheets that depend on partial data.
- Outdated tools only capture what devices choose to broadcast, leaving vast sections of the network invisible.
- These tools also can’t safely talk to devices, which means full discovery often takes months and still misses critical assets.
- Traditional asset inventory doesn’t include risk assessments, which uncover the risk profile of each device.
- Passive tools were never built for the complexity of OT monitoring. They can’t communicate across diverse device types or extract the high-fidelity data required for real security decisions.
The result is blind spots that undermine risk assessments, compliance gaps that persist through audits, and asset inventory reports that are incomplete.
Uptime, safety, and compliance depend on knowing exactly what’s connected and how it’s configured.
Plus, active threats are evolving. Attackers are choosing to go after IoT assets, increasing 400% YoY, because they are far quicker and easier to target than a laptop or server. Yet, securing and hardening these xIoT devices at scale is impossible.
To address this evolving problem, we have to rethink discovery and assessment of our OT asset inventories.
Passive vs. Active vs. Intelligent Active Discovery
For years, OT monitoring teams have been told there’s only one safe way to discover assets. That belief has shaped an entire generation of passive discovery tools that wait for devices to communicate with them.
Passive Discovery
Passive discovery listens for network traffic. It’s safe, but it doesn’t see everything. These tools depend entirely on what devices choose to broadcast, offering a partial view at best.
- Listens Only: Gathers data from network broadcasts without interacting directly with devices.
- Safe But Incomplete: Misses silent or misconfigured assets that never broadcast.
- Low-Fidelity Data: Limited insights. Often includes only IP or MAC addresses.
- Slow Time-to-Inventory: Full coverage can take months and still remain partial.
- High Blind Spot Risk: You can’t secure what you can’t see. With passive discovery, you’ll never see it all.
Traditional Active Discovery
Active discovery, on the other hand, was designed to go deeper by communicating directly with devices. However, traditional approaches have a reputation for being blunt and risky.
- Aggressive Scanning: Uses brute-force probing that overwhelms fragile OT devices.
- High Network Load: Floods the environment with packets, consuming bandwidth and resources.
- Operational Risk: Can trigger performance degradation or downtime during scans.
- Limited OT Suitability: Designed for IT environments, not for safety-critical industrial systems.
- Avoided in OT Monitoring: Most organizations steer clear of traditional active discovery to prevent disruptions.
Intelligent Active Discovery
Intelligent Active Discovery is different. It’s the evolution of both approaches, offering complete visibility, deeper discovery, and zero disruption.
- Safe, Native Communication: No reckless scanning. Intelligent Active Discovery speaks each device’s native language, ensuring secure and non-disruptive interaction across IoT, OT, IIoT, and IoMT environments.
- Evidence-Based Analysis: Intelligent Active Discovery delivers 100% device certainty the first time, gathering a full risk profile on the firmware, certificates, credentials, and configurations.
- No Infrastructure or Agents: Completely software-based and agentless. Deploy on-prem or in the cloud in minutes without hardware installation or downtime.
- Automated and Scalable: Discovers faster, uses fewer resources, and collects more granular data than any other method.
- Full Remediation: Intelligent Active Discovery automates credential rotation, firmware management, certificate renewal, and configuration enforcement to close every risk loop.
What “100% Visibility” Really Means
True visibility means cataloging every layer of identity, configuration, and security posture that defines how a device behaves on your network.
To get the complete picture of your OT asset inventory, here’s everything you need to know about your devices:
- Device type
- Manufacturer
- Model/series
- IP address
- MAC address
- Device identifier
- Serial numbers
- Model number
- Firmware version and patch status
- Active protocols
- Open ports
- Active services
- Device family–specific detail
- Manufacturer–specific detail
- Password configuration and credential health
What’s the Fastest Way to Reach Complete OT Asset Inventory?
The fastest way to reach complete OT asset visibility is Intelligent Active Discovery.
Intelligent Active Discovery achieves what traditional methods can’t: 100% visibility in hours, not weeks or months. It safely communicates with every connected device across your OT asset inventory using native protocols to gather verified intelligence in real time.
Compare the difference:
- Passive Discovery: Incomplete after months. Limited visibility and outdated results before you’re even finished.
- Manual Audits: Impossible at scale. Labor-intensive, error-prone, and often disruptive to production systems.
- Intelligent Active Discovery: Full coverage in hours. Automated, accurate, and proven safe for mission-critical OT environments. Includes risk assessments that show the entire risk profile of devices.
Is Active Discovery Safe for OT Networks?
Active discovery can be safe for OT networks. Here are some questions you can ask to determine if an active discovery solution is safe for OT networks.
Does it Promise Zero Disruption?
Active discovery solutions must be able to discover and classify assets without operational impact on mission-critical, life-critical, and other sensitive cyber-physical security systems.
Does It Have Device-Aware Communication?
Check to see if the interaction layer enables direct, intelligent communication with embedded devices. If it uses each device’s native protocols, both authenticated and unauthenticated, to identify and classify assets safely, quickly, and accurately, you’re in good hands.
Does It Use Dynamic, Self-Calibrating Discovery?
The platform you use should dynamically adjust parameters such as probe sequencing, packet rates, and ports in scope through self-calibrating “Agendas” to ensure every interaction is optimized for speed, safety, and zero disruption.
Is It Efficient?
Make sure the solution you choose is lightweight and efficient, sending only a fraction of the traffic of traditional passive tools. This will result in comprehensive asset visibility with no network performance degradation ever.
What Device Data (Firmware, Certs, Credentials, and Configuration) Should We Collect?
Complete visibility means understanding every layer of your device’s identity. To truly eliminate risk, organizations need to collect high-fidelity data across four critical dimensions of xIoT security.
1. Firmware Intelligence
Every firmware version tells a story about vulnerabilities, patch history, and end-of-life risks. An effective OT asset inventory should identify outdated or vulnerable firmware across thousands of devices, enabling proactive remediation before attackers can exploit known weaknesses.
2. Credential Hygiene
Default and weak passwords remain one of the easiest paths into an OT network. Regularly auditing and rotating device credentials is essential to maintain system integrity and prevent unauthorized access.
3. Certificate Status
Expired, self-signed, or missing certificates silently weaken trust across connected systems. A complete asset inventory must identify all device certificates, flag issues, and support timely renewal or revocation to maintain encrypted, compliant communication.
4. Configuration Consistency
Misconfigurations create drift, instability, and compliance gaps. Standardizing configurations across sites and vendors ensures every device aligns with organizational policy and operates safely within the network.
10-Step OT Asset Inventory Checklist
Building a complete OT asset inventory doesn’t have to be slow or risky. Use this 10-step checklist to move from blind spots to full visibility.
- Define Your Scope: Identify all network segments, sites, and device categories across IT, OT, and xIoT environments.
- Set Clear Goals: Establish what success looks like, including coverage, accuracy, time-to-inventory, and acceptable network impact.
- Select a Safe Discovery Method: Choose a discovery approach that communicates natively with devices, not one that risks downtime.
- Run a Pilot Scan: Start with a small, representative environment to verify data fidelity and ensure zero disruption.
- Gather Complete Device Intelligence: Collect firmware details, credentials, certificates, and configuration data.
- Validate and Enrich the Data: Cross-check findings with your CMDB, NAC, or SIEM to confirm accuracy and fill in ownership details.
- Classify and Tag Assets: Assign device type, location, owner, and criticality. This sets the foundation for risk-based management.
- Remediate Key Risks: Rotate default credentials, update outdated firmware, and replace expired certificates.
- Standardize Configurations: Enforce consistent settings and policies across devices and sites to prevent configuration drift.
- Schedule Continuous Discovery: Automate ongoing discovery and monitoring so your asset inventory remains complete and current over time.
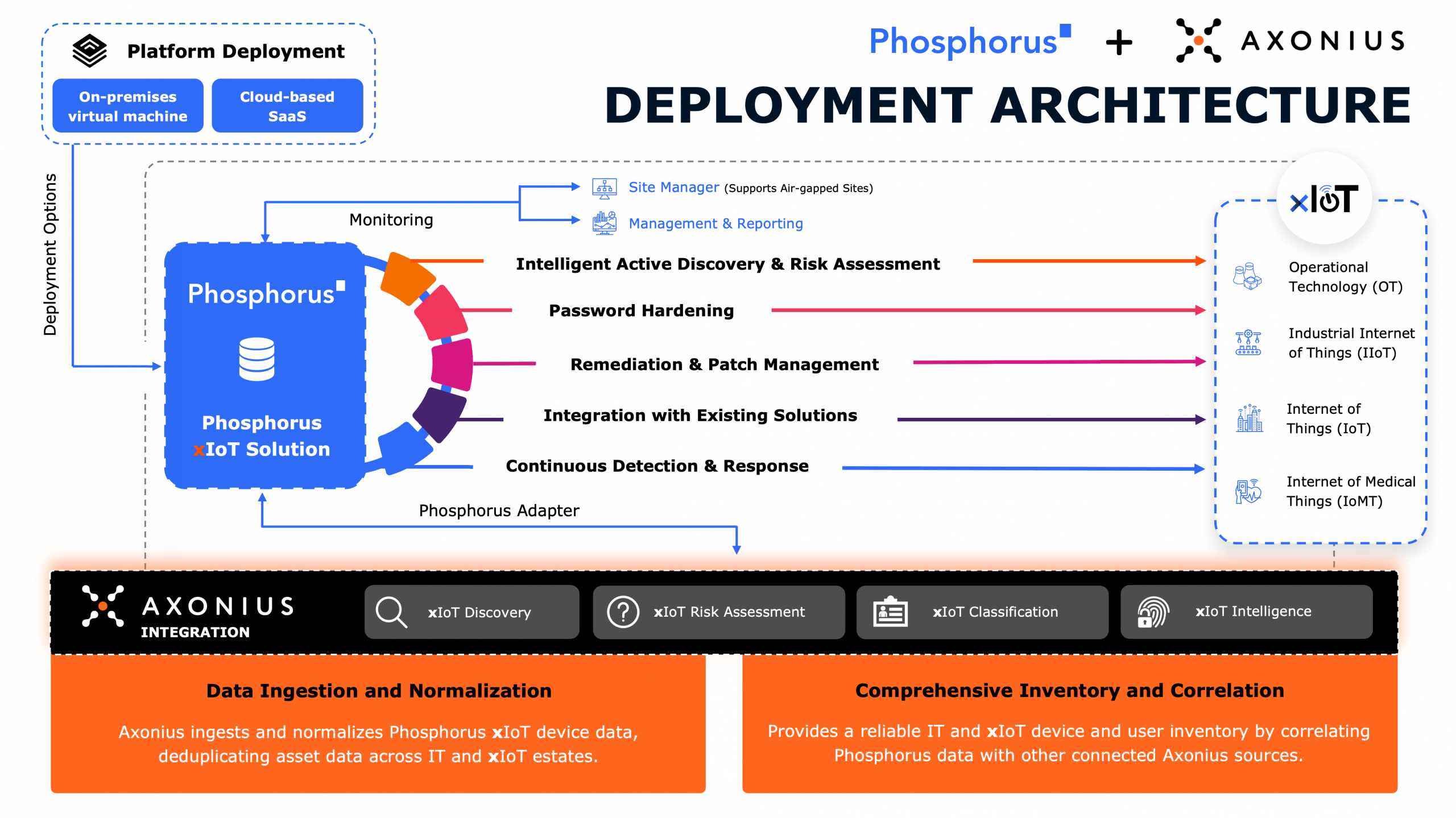
How Phosphorus Delivers Complete OT Asset Inventory Discovery & Remediation
Collecting a complete OT asset inventory is traditionally a long, inefficient process. However, with Phosphorus Intelligent Active Discovery, enterprises can discover, remediate, and manage their entire OT asset inventory in hours. Here’s how:
- Discover & Assess: Phosphorus surfaces every unmanaged asset safely across IoT, OT, IIoT, and IoMT. The result is a complete, high-fidelity asset inventory enriched with firmware, credentials, and configuration intelligence, all gathered without disrupting operations.
- Harden & Remediate: Phosphorus automates the hardening process with credential rotation, firmware management, and configuration enforcement, eliminating default credentials, patching vulnerabilities, and ensuring compliance across every connected device.
- Manage & Monitor: Phosphorus delivers continuous assurance through ongoing monitoring and lifecycle management.
Looking to discover your full OT asset inventory quickly? Contact Phosphorus to schedule your personalized demo.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.