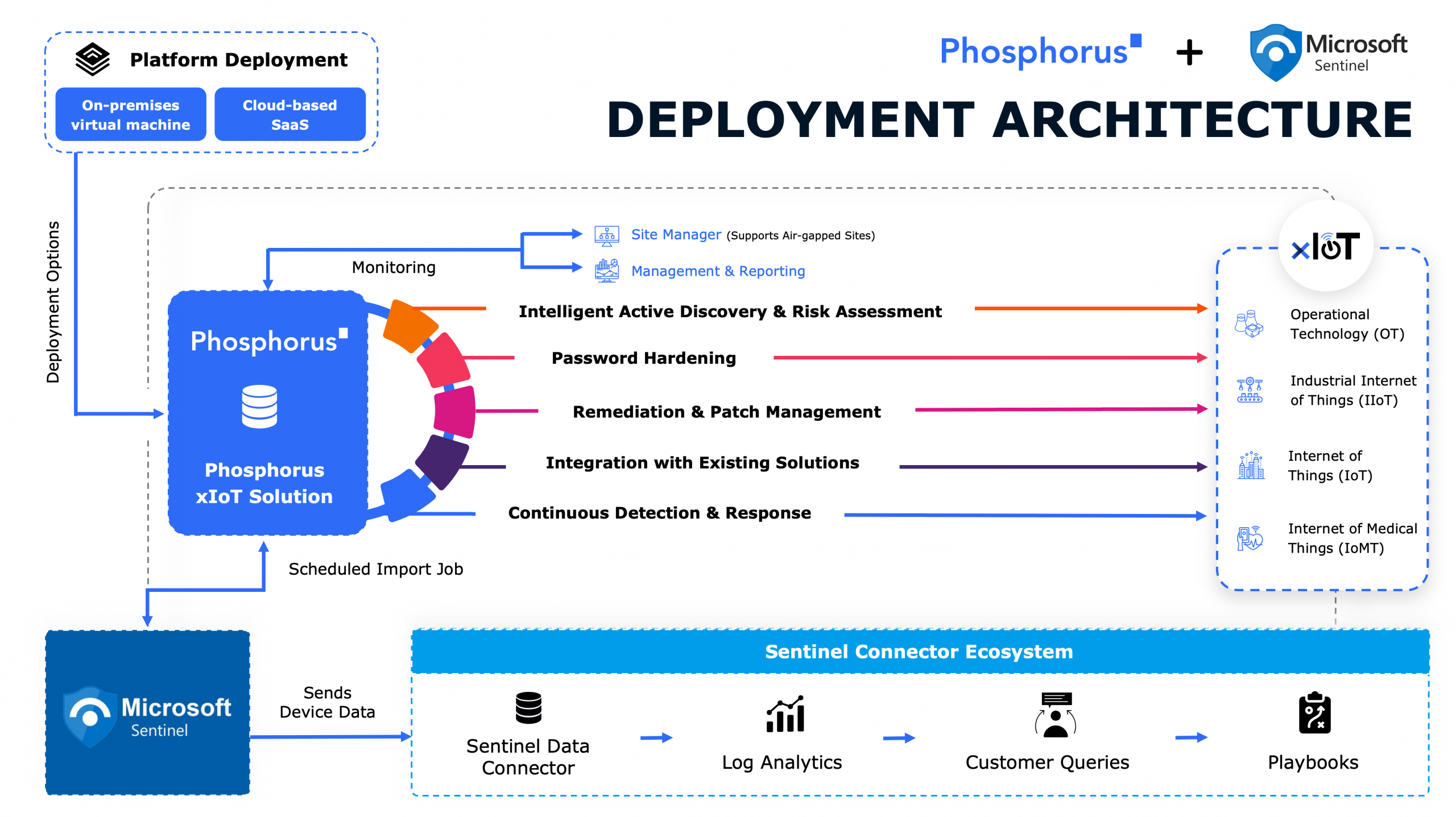
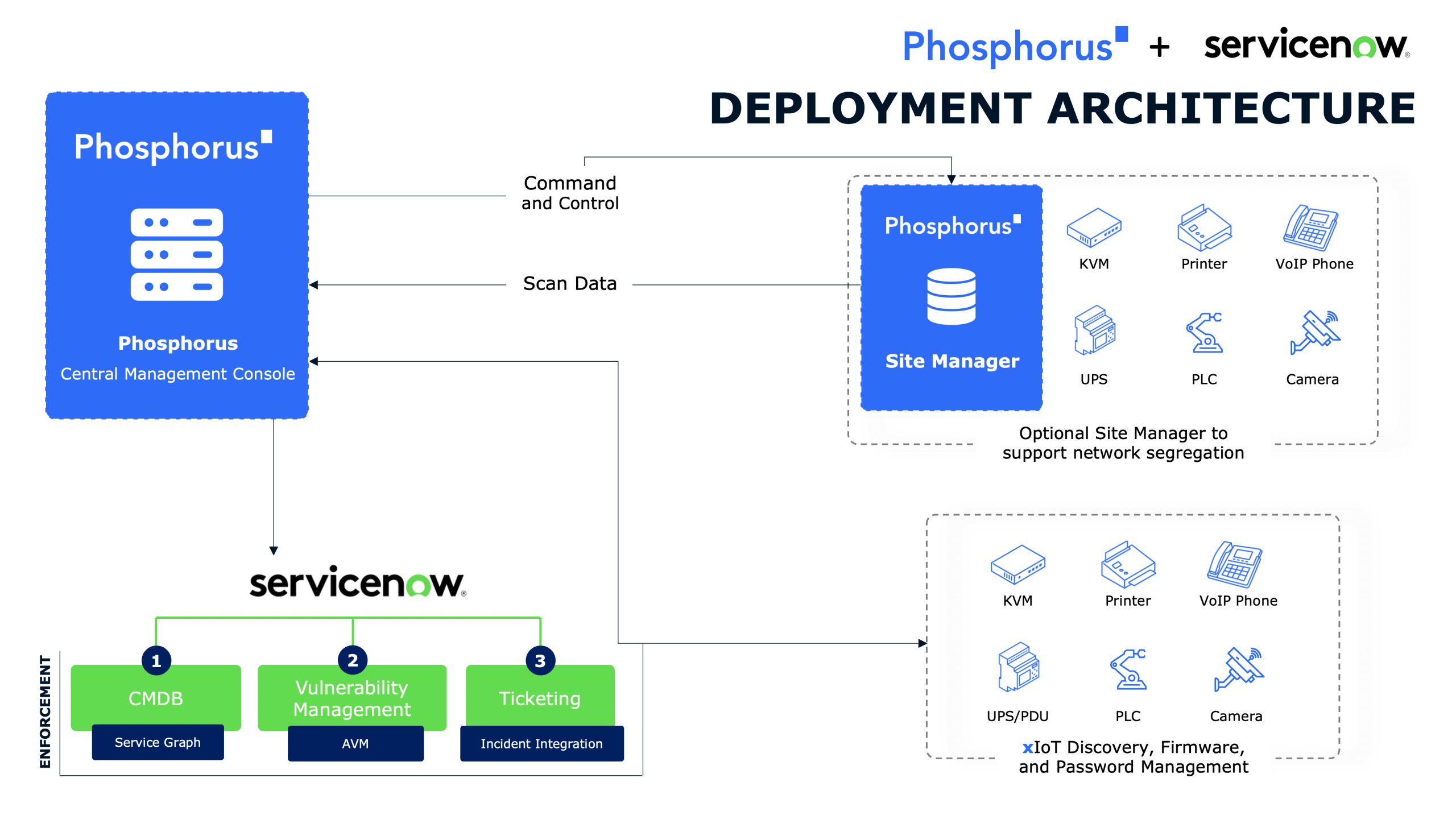
The dynamic evolution of hacker culture, the ongoing transformation of cybersecurity conferences, and the importance of resilience and curiosity among security researchers are all topics covered in this episode through stories of past and present with Dhillon Kannabhiran, CEO and Founder of Hack In The Box (HITB) and Out Of The Box. He and Phillip Wylie examine the shift from open knowledge sharing and exploration to the monetization and commercialization of cybersecurity exploits. Dhillon offers insights into the unique approaches Hack In The Box and Out of the Box conferences have taken, encouraging people the valuing of persistence and the collaborative spirit that push the community forward.
- Evolution of hacker culture and the foundational role of resilience and curiosity
- History, mission, and format of Hack In The Box and Out of the Box conferences
- Shifts in conference and research communities post-COVID and the influence of commercialization on sharing
- The continuing need for community, knowledge sharing, and supporting new talent in cybersecurity
- The changing landscape of security research and bug hunting with the advent of AI and new technology
Transcript
Dhillon Kannabhiran: I think what makes hackers different from everybody else is resilience and our willingness to not give up and not say, oh, this shit doesn’t go on bile. So fuck this shit, I’m going to watch Netflix. But figuring it out and making it work, right, I think that that sets us apart. As in, that’s what makes us different. As in, that’s what makes hackers different. Right? Is that not giving up resilience?
Phillip Wylie: In this episode of the Phosphorus IoT Security Podcast, I’m joined by Dhillon Kannabhiran and we discuss cybersecurity conferences in the Middle East and Asia, as well as discussing cybersecurity research and cybersecurity community. I hope you enjoy this episode. Hello and welcome to another episode of the Phosphorus IoT Security Podcast. Today I’m joined by Dhillon Kannabhiran. Dhillon and I have been connected on social media for many years. I think we originally connected on Twitter, now rebranded as X. And I got to speak at his Hack in the Box conference in Singapore back in 2022, the first time we actually got to meet in person. So it’s an honor to have you join us today and welcome to the show.
Dhillon Kannabhiran: Thanks for having me, man. Thanks for having me. Always a privilege, always fun. Yeah.
Phillip Wylie: Great to virtually see you. It’s been too long since the last time. I’ve got to get out to one of your conferences again.
Dhillon Kannabhiran: Yeah, man, time flies, right, when you’re having fun, so. But yeah, it does.
Phillip Wylie: Definitely.
Dhillon Kannabhiran: You just mentioned 2022 and I’m like, was it really that long ago? I was kind of doesn’t feel like it. But yeah, time’s really gone by, man.
Phillip Wylie: It was crazy, too, because this was still, you know, we still had Covid to deal with because I remember when I was there that you had the week. The week after I left is when they. They removed the mask mandate, so.
Dhillon Kannabhiran: Oh, yes.
Phillip Wylie: Had to.
Dhillon Kannabhiran: Yeah, yeah, yeah, man. Yeah. Covid’s a bad word. You know what I mean? It’s a time that we all want to forget, but, like, yeah, it was. There’s a distinction between BC before COVID and like, AC, I guess, you know, it’s. But yeah, 2022 was. Yeah, you’re right. It was still in the mask mandate. Social distancing, sanitize your hands. But yeah, interesting times that we live through, right?
Phillip Wylie: Like, yeah, definitely, definitely. Good to have that behind us now.
Dhillon Kannabhiran: So.
Phillip Wylie: So some of the folks that may not know who you are, if you wouldn’t mind introducing yourself and telling the listeners about your background.
Dhillon Kannabhiran: Sure, yeah. So basically we run this small little conference called HackInTheBox. We’ve been around for like 20 something years, always say we’re similar to Black Hat and defcon, except we’re in Asia. So we started out in Malaysia in like 2002, 2003. We’ve done events since then in the Middle east. So we were in Dubai and Abu Dhabi for a couple of years. We’ve then expanded to Europe and. Yeah, so it’s been like 20, 22, 23 years, something like that. Like a long, long time that like I’ve had so much gray hair. I didn’t have this much gray hair when I started. But this is what happens when you run conferences. Yeah.
Phillip Wylie: It’s usually people’s children that give them the gray hair.
Dhillon Kannabhiran: Yeah, I have attendees to worry about and speakers which are like children also I suppose, but it’s like. Yeah. A different set of all this. Yeah.
Phillip Wylie: And the interesting thing is is you, you really operate a high quality conference because one of the things I was really amazed is still one of the best conferences I’ve spoken at. I can’t. I was amazed at the. The artwork on the stage, the audio and video setup was like really, really very nice. I mean I remember because, yeah, it was pretty amazing. I was really impressed, especially considering it wasn’t like a really huge conference, but just the level of quality of the conference through the speakers. Because I know a lot of the speakers had original research because actually got to meet a young man that’s originally from Cuba, Sebastian Castro, he was there, he had some Windows security related research that he had done. So there’s a lot of original research and top notch speakers there. So it was a pretty amazing conference.
Dhillon Kannabhiran: Yeah, it was nice to have you over, man. So basically I think you attended the Singapore event and so for the listeners and for the viewers, I guess essentially we had like a few different types of conferences that we run. So we had like the flagship event which is called the HRDB Security Conference and that’s like a large scale event that we used to do in Amsterdam. Was used to be like our largest event. And then we decided, well, we should do something more bespoke. And so we did an event called HRTB gsec. And the difference was that we allowed the audience to kind of choose the talks. So you actually got invited because the audience wanted to do that.
We decided that since people are paying tickets to attend these kind of things and then usually not that cheap, we should probably let them have a say in who they’re going to See on stage and what kind of talks they want to listen to because yeah, we have a review board and they’re like, you know, Google Project zero and the who’s who of the security industry, folks from Microsoft and so on and so on. But it’s all fine and well, but they might not speak to what you are personally interested in. So if you’re buying a ticket, ultimately I think you should have a say in what’s interesting to you. For me, I love AI and all AI stuff. So if I had a choice I’ll be like, yeah, vote for all the AI talks. So we decided to do this different format and we call it GSEC where people could vote on the talks. And it was just a different style of event. So a little bit smaller but perhaps I would say attendee wise engagement will probably be a little bit higher since everybody kind of like really wanted to be there and wanted to see your talk. Right. Or and everybody else’s.
Phillip Wylie: Yeah, it’s kind of, kind of makes having not. It makes it to where you really don’t have to have a review board having that case because the attendees are the review board.
Dhillon Kannabhiran: Well we still had the review board choose the high level list. Okay, so let’s just say we. Because it was, I believe it was like a, a single track conference that we ran for two days if memory serves me right. So excuse the old man, I might not remember, but I think it was a single track over two days. But anyway, which would mean we have like something like, I don’t know, let’s just say 12 talks, right? So six per day. So six speakers per day and they would shortlist say 30 that they felt were worthy because most of the time we have a ratio of something like between for like the really big hack in the box events is something like 15 to 20 to 1. So which means 20 submissions to every one slot that we have, which means choosing the TOCs becomes ridiculous. Right.
So in Singapore I think it was a little bit more manageable, something like maybe 8 to 1 or something like that. So they chose the 30 favorite toms that they thought were like worthy of filling the 12 slots or whatever that we had. And then we shortlisted that and provided that list as a shortlisted list for people to vote on because essentially it will become overwhelming if we let the audience kind of choose from a list of 100 something talks because there’s lots of overlap and the nuances in what’s different between presentation A and B. They might not be the best person in order to kind of like pick that out, right? And that’s what we have our CFA review board for. So they would choose between A and B. That’s talking about the same topic, but which is talking about something that maybe hasn’t been fully explode, perhaps. So that would be our choice because it’s not been said before, or it’s a slightly different angle or slightly different take on the same problem, but approaching it from a different way or a different outlook. So we would say that because Talk A perhaps has been presented as black hat, we wouldn’t choose Talk A not because it’s been presented before. But if Talk B brings enough value and enough difference to the table, then it doesn’t matter who the speaker is. It’s like that point of view, you know what I mean? Even though it might be a bigger speaker and talk A bigger in the sense of like more famous or has presented many times before. But I guess that’s how things stay fresh and you kind of surface up new talents, you know what I mean?
Phillip Wylie: Yeah, that’s pretty interesting. Back to the quality of the conferences, the talks and stuff, it’s kind of different because most conferences that I’m used to going to, yeah, there will be some people that has some original research, but that is just not normal. Whereas I know the conference I spoke at, Hack in the Box Singapore, you actually had two different tracks. One was like a research track and the other one was a security track because I did a Talk on securing APIs through external attack service management. But then the other track was research. So that’s one of the stages that Sebastian spoke on.
Dhillon Kannabhiran: Okay, okay, okay, okay. Yeah, I mean we normally. So that’s the thing. When everybody always asks me like, how do I get a speaking slot at Hack in the Box? I’m like, well, submit your best research. And it doesn’t really have to be like zero day level stuff. Of course we love the zero day every prioritize attack based stocks, mainly because they’re exciting, not because we don’t think defense is important, but it’s like from an attendee standpoint, like it’s exciting to see stuff getting hacked, you know what I mean? So we always prioritize zero days, but I always tell folks that like submit your best research because at the end of the day it’s not me juicy. And so I might have my own biases of what I think makes a cool talk, but we trust our review board to be to have a holistic view on where the industry is going. And there’s so many folks in our Review board.
Anyway, so it kind of balances out anyway that, you know, you have some folks that would say, like, yeah, this topic has been covered many times before and others will be arguing for, well, yeah, okay, it has, but this particular portion of the research is novel and this particular researcher hasn’t had stage time. Why not give them an opportunity? And you never know what happens from there, you know what I mean? Because, yeah, there’s lots of smart people. You know what I mean? So it’s like not everybody might be a household name.
Phillip Wylie: Yeah, yeah, that’s. And that’s the thing too is just because someone is well known doesn’t always mean that it’s the best. Also topics they bring. But then again, at the same time, some of these people are well known. They’re. They’re presenting a lot of these same topics that’s been heard. So it’s very interesting that you bring. That you bring in the quality of speaker that you do.
So one of the things that’s interesting too, I just recently noticed, was that you have a series of conferences called Outside of the Output out of the box.
Dhillon Kannabhiran: So what’s.
Phillip Wylie: So what’s the difference between hack in the box and out of the Box?
Dhillon Kannabhiran: Out of the box. Yeah. So basically, so hang the box. We essentially sold the brand and the business back in like 2018 to the UAE. So anything that happens outside of the UAE, we have to call it something else. And since we are now in a post Covid era, we were thinking that, you know, looking at the way the conferences are these days and attendees and the, you know, looking at the next generation. Right. And the fact that they grew up through living through a pandemic.
Some of them graduated remotely, didn’t really go to classes, had remote classes. Like the expectation from an attendee for an event is quite different from you and I, who are much older with the gray hair. We had a different need when we went for conferences. It was a different time. Right. And now in the post Covid era, it’s like, you know, a lot of things are done remotely. Like even this podcast, for example. Right.
Like, this would probably be something we would have done at a conference in a room and having met each other in person and then sat down and had this podcast recorded. But now we’re doing everything remotely. I haven’t seen you in three years, so you know what I mean?
Phillip Wylie: Yeah.
Dhillon Kannabhiran: So the younger generation and even attendees want something else because, you know, having lived through a pandemic, you now value your time differently. As in time away from family and you know, time spent on the road, flying, staying in hotels, blah blah, blah. All the costs have gone up as well. And you weigh all of those things very differently, right? So we were thinking like, well, we have an opportunity to then now have a new brand and thus create a new experience or something completely different. Why not? I mean, it’s like, why do you want to do the same old thing that we’ve done before? And not to say that we can’t do a hide in the box event anymore. We just do those in uae, much larger event and we have the pro CTF where Invite the top 10 teams from CTF time to come compete. And like, you know, it’s got a. It’s like a completely different thing, right? So now we have the flexibility of adding something new.
We should like all good hackers experiment and try it out and see what happens. You know what I mean? Like, what’s the worst that can happen anyway, right?
Phillip Wylie: Yeah. And for, and for someone that comes from an offensive security background and really appreciates hacking, I really appreciate conferences that have a lot of focus around hacking and security research because a lot of, a lot of conferences here in the States are really not so much offensive oriented. There’s a lot of stuff around a defense which there’s a need for it, but it’s for those of us that work on the offensive side really appreciate the hacker conferences because for us there’s some around here. But it’s just, I don’t know, there is not as much emphasis I guess on some of these conferences on the offensive side or research side.
Dhillon Kannabhiran: I guess we grew up differently, right? I mean we are from a time when we were in exploratory as in, you know, we grew up in a time where you book into a hotel and you start exploring the WI fi. It’s like, you know what I mean? It’s like normal. It wasn’t something that you would. Why would you do that? Is it? It connects to the Internet, you’re fine, you can download stuff, right? We’ll be like, no, let’s look at the infrastructure. Let’s try mapping stuff out, see whether there’s any authentication problems, see if we can get into admin level. Not because we wanted to cause any trouble, but just because we were, we were just curious to see whether we could. Right. And so we’ve always been, I think, offensive focused in that sense.
Let’s see what happens if we poke this thing and break. Right. And I guess that sense of, you know, curiosity I suppose still drives a lot of what we do. And we, even though now we are much older and much younger, I suppose, quote unquote, wiser in everything that we approach, we kind of approach it with a more sense of play, you know what I mean? In the sense that like, what’s the worst that can happen, bro? Like, you know, just experiment and try. Right. Like, you can always go back to what worked before anyway. Right. Like, but there’s no harm in trying something else.
What happens when you double space? Double space. You know.
Phillip Wylie: It’s. It’s really interesting how security and the conference scene and hacking in general has, has evolved because, you know, when we were younger, getting started out, you didn’t have bug bounties.
Dhillon Kannabhiran: Yeah.
Phillip Wylie: So it was. So you didn’t have those opportunities.
Dhillon Kannabhiran: This is basically is what gets sense to you, man.
Phillip Wylie: Yeah. And it’s interesting too, because you mentioned the curiosity, because back then people could do things out of curiosity and not really have to worry about repercussions, you know, because a lot of times people were doing it out of curiosity, not malicious intent. So it’s just kind of interesting how that’s kind of changed. Nowadays, security researchers really have to be careful about what they do they’re doing, or they could find themselves in legal trouble.
Dhillon Kannabhiran: I don’t know, man. I think actually the amount of legal trouble you could find yourself in is probably the same as it was before. It’s just that right now I think people don’t share as openly the coolness about it, as in, it always has to be something big. And when it becomes something big, it’s more of like, how can I monetize this? It’s the question that today people will ask themselves. As in, if I found a vulnerability in iOS, let’s just give an example, right? If I found a 0 click verbal iOS that’s a $10 million exploit, basically, am I going to drop that knowledge on the Internet just for everybody else to enjoy? No, right? Even it used to be that, okay, I’ll save that knowledge and present it at Black Hat or present it at Hack in the Box or whatever, as in, I’ll save it for a special occasion. Now it’ll be like, who can I sell it to and who’s going to pay me enough for it, right? And can I trust them to actually pay me for it or are they going to rip me off? That’s like today’s thinking. So you have folks that are kind of like sitting on knowledge, which in itself is probably not really useful, but when chained with a lot of other stuff, can become Useful, but nobody wants to share anymore. It’s like everybody’s keeping all the goodies for themselves, right? Where? As opposed to in the early Dan Kaminsky days, for example, where he was on stage making money spit out of an atf.
Those shit days are over, man. We’re not going to see that anymore. Which is a shame. The days of Hugo Tesla getting up on stage and saying I can hack a plane, or Jim Giovanni saying I can take over a satellite and showing it, not because we can do something with it that’s malicious other than getting free Internet, but that was in itself cool. We could get free Internet using satellites. Like, wow, man, that’s cool, man. When would I use it? I don’t know, man, but it’s still cool. And those days are over.
And that’s a shame. That’s a crying shame for the younger guys who never got to experience that. You know, the joy of just finding something that, that you don’t think about, like, oh, like how much money can I make from this? It’s more of like, hey, let me show some guys because this is cool and this is interesting and isn’t this peculiar? You know, I mean like this cup. See what I discovered, you know, I mean like, this is cool, this is fun. And it wasn’t so much about the bragging rights, which was at some point it was about the bragging rights and then now it’s literally about the money.
Phillip Wylie: So it’s more about someone just sharing something, some cool technology, some cool hack that they found instead of just the monetary piece of it and kind of.
Dhillon Kannabhiran: Walking you through the thought process, which is like, I don’t think shown so much these days. People kind of like show the problem and you know, how they approached it perhaps and then exploit. But they don’t really show their tool set and their thinking or you know, what exact the steps, like, you know, literally step by step, kind of like walking you through it. Like where, as opposed to kind of like the earlier days, people would actually literally put in your hands, you know what I mean? The code and the methodology and how they got to where the solution. As in it’s not just about the solution, but it’s the thinking process behind it, the methodology. And I think that’s really where the value is, you know what I mean? That’s where the knowledge is, you know what I mean? Teaching somebody the trick behind the exploit, you know what I mean? Like how exactly do you find it? How exactly do you write it and how did you discover it, right? What made you look in that direction to begin with. What was the thing that kind of jumped out at you that, that you notice that other people glossed over, like there’s so many vulnerabilities these days that like, you know, an open source software that have been there for like, God, Lord knows, it’s like a decade or some shit. Nobody found it.
And it’s like major ass vulnerability. How the hell did you decide to download this package, look through it, and what is it about it that jumped out at you? Was it a fuzzing tool? Fuzzing toolchain? What is it? Is it like, what. What’s the special sauce, bro? Like, nobody wants to share their knowledge. And that’s a shape because it’s actually like, you know, if I was a toolset author and I’ve written a whole bunch of like nonsense scripts and shit, if somebody used it and made it better, I would want to know what they did to make it better and so that I could improve it myself. And so I feel like people are missing out on the kind of like sharing the knowledge in order to move everybody forward rather than just, I win. Everybody else just remain stagnant, which is the current status quo. It’s a shame, you know what I mean? It used to be that we all move forward together, you know what I mean? I presented at a talk or whatever and everybody else kind of gets access to it and does stuff with it and it’s cool.
Phillip Wylie: Yeah, it’s very interesting. And so I know you’ve seen running conferences around the globe like you have before we started our or recording the podcast. You were talking about some people just writing out exploits of stuff within Notepad with very minimal tools and creating these really cool hacks and stuff. So if you wouldn’t mind kind of explaining some of the things you’ve seen there.
Dhillon Kannabhiran: Yeah, I mean, so we’re talking like early 2000s, right? So in fact, yeah, it was in 2003. HD More was one of our first speakers that came to our first quote, unquote international hang in the box that we had in Malaysia. And he presented the metasploit framework as an idea, as in it wasn’t even like, you know what it is today, right, which is Rapid seven and blah, blah, blah. Right. And it was just a framework and he was working in God, Lord knows what. I think we just did server 2003 or something like that, and he found a zero day in it, like live. He was just playing around with stuff at the CTF that we had, and he found some vulnerability and we called Microsoft Malaysia and it was like, cool to see this in action. As in, like, he wasn’t safeguarding it.
He wasn’t saying, oh, I’m gonna use this to my own advantage and not share it. I found something cool. It’s like, you know, you guys can’t see about it. He was like, we were literally seeing discovery being made in person, as in like a bug hunter. Literally, like hunting a hacker, doing what he does best. And it was awesome. Like, and so those early days, and then we had folks like from Vietnam who were playing CTF and like, you know, they came. That Internet access for them came a little bit later, but they were writing exploit code, like, in the terminal, like shellcode, like, without using any kind of tool set or compiler or any shit.
The guy is just writing like, hexa. And I’m like, what the fuck, man? How the fuck do you do that, man? How do you even read it? And it’s like, you just read it. It’s like English. I’m like, you are different. You and I are not the same, man. You are on some next level, bro.
Phillip Wylie: Yeah, that’s really cool to get to see that and see how things have evolved. So for someone that wanted to get into security research now, what would you recommend since things have changed so much over the years?
Dhillon Kannabhiran: Yeah, I don’t know, man. Honestly, I would say don’t. But if you really want to get into security research or realize that the methodologies and things that you’re doing today, fundamentals are probably still important. But essentially the approach to bug hunting is going to change so drastically. I mean, I’m talking AI, obviously, agentic AI, stuff like Expo, you know, Hacker One, number one leaderboard is now AI. So does that mean bug hunting is dead? You know what I mean? Why bother hunting bugs manually? People have been evolving, obviously, to write fuzzing tool chains and stuff like that to help their workflow, and now AI is just the next iteration in it. So adopt the technologies now rather than later and kind of like imagine a new paradigm, you know what I mean? Everything is agentic and essentially you are an orchestrator and you’re not actually going to be hunting the bugs by yourself, like literally on the command line. That shit, those days are over, bro.
You’re going to have like a couple of agents and specialized agents that are going to be able to surface certain bugs. Your job is to direct them so that you don’t waste your tokens, which are going to be expensive, at least for the time being. Right? Because every context window in AI and how big the context window is and how big your, how much memory utilization you’re using determines the cost of your request. Right. So if your prompt isn’t succinct or if your instructions are not tight sharp, if your agents are not, well, fine tuned, you’ll end up spending a lot. But essentially your job is not going to be actually running the fuzzing tools and writing the exports for the offsets. You’re going to have to be thinking bigger picture and how systems interconnect and how exploits can surface not because of a technicality, but usually because of a design flaw. Most often than not, AIs might still be building most of the backend stuff, but there’s still going to be humans connecting the shit together.
And people inherently make mistakes. So that will be my advice.
Phillip Wylie: Yeah, kind of thinking along lines of that. Do you think using AI to vibe code, do you think it’s really going to drastically increase like the bugs and the insecurity out there?
Dhillon Kannabhiran: I don’t know about the bugs per se, although we have seen a lot of examples recently about like, you know, certain apps and services that have gotten compromised. And obviously the joke is that, oh, it must be a barcoded app. Whether that’s true or not. I would say to a certain extent, yes. If you have somebody who is not a developer who doesn’t understand the programmatic nature of computers in the sense that normally you as a programmer you would approach a program a problem and chunk it as in like, look at it in like smaller subsystems and smaller sub problems that need to be solved and kind of like a flow of like top down or whatever it is. And we would think of things in a logical manner. And as long as you a designer or have developed software before, you probably will not encounter these vibe coded bugs because you would have prompted it in such a way that you would have been succinct in the fact that you would have taken into consideration that certain actions need to be performed server side, not client side. So do not expose this API key.
Do not, you know the simple ass mistakes that an AI would make. If you just ask for a poc, which is a completely different thing from a production app, like sure, we’re making it work in your laptop and like on your little small, you know, demo is all fine and well, but then pushing that code to production, that’s where the problem becomes because it’s like you’re not thinking of like well, what happens when RLS only takes care of the role but you need access control to the column. Then you need an app secret and you cannot use it in a client side exposed API. It needs to be completely server side, right? Shit like that. As in, if you’ve never encountered those problems before and you try and whiteboard something, then yeah, of course your app is going to be like hacked like day after tomorrow, you know what I mean? But you’ll learn. So it’s not the end of the world. You won’t be the first person to get hacked anyway. So, you know, don’t feel bad, you know, if shit breaks, just fix it.
I think it’s the more of. I think what makes hackers different from everybody else is resilience and our willingness to not give up and not say, oh, this shit doesn’t go B, so fuck this shit, I’m going to watch Netflix. But I choose it. Figuring it out and making it work. Right. I think that that sets us apart. As in, that’s what makes us different. As in that’s what makes hackers different.
Right? Is that not giving up resilience?
Phillip Wylie: Yes, it’s that persistence for stubbornness. Because I got my start, start like a lot of folks in security and it, and I remember I’d be working and people say you’re really patient and said, no, I’m stubborn. It’s like, I got to solve this problem.
Dhillon Kannabhiran: Exactly. When somebody says it cannot be done, I’m like, hold my coffee. Are you sure? Let me try. You know, I mean, it’s. And I guess like, in a way it’s not that, that, that burn and that fire, I don’t think it’s dead. I do see that still alive in a lot of younger guys and a lot of like, you know, I’ve been to conferences in, you know, Kazakhstan, for example, so. And it’s completely different vibe from anything that we have in Europe or North America or even in Asia. And like that fire of like, hold my beer, let me show you is still alive and well.
So, you know, I’m not. I’m still quite hopeful that that hacker spirit of like, you know, let me show you and I don’t believe you. And you know, I’m going to try, try myself just to satisfy my own curiosity. Maybe you’re right, maybe you’re wrong, it doesn’t matter. But I’m going to try myself. And that stubbornness or that resilience to learn something, even if it’s like quote unquote difficult, is not dead. So that gives me a lot of hope.
Phillip Wylie: Yeah, that’s good. And one of the things I think that people should take in consideration is there’s conferences are great, but there’s also, when the conferences are not going on, there’s still community out there that you can share with and collaborate and learn from.
Dhillon Kannabhiran: 100 and I think, like, you know, a lot of people shouldn’t be so afraid of putting themselves out there, you know, I mean, like, now that I’m older, when I was younger, right? So a lot of times I would build something and I’ll be like, nah, I’m not going to share this with anybody.
Phillip Wylie: It’s.
Dhillon Kannabhiran: It’s silly. You know what I mean? It’s just a nonsense app, right? But now I. I’m older and I don’t give a. So I put some nonsense app and I just put it on GitHub anyway, right? And people downloaded the pocket and they star it and they write to me and say, like, hey, you know, it was cool. It’s good, you know, it helped me. Or like, you know, whatever, I used it for something. And that to me in itself is worth. Worth the effort then.
You know what I mean? So don’t prejudge what you’re working on, because to you, you’re so deep in it and you’re so entrenched in it that it seems simple. But to somebody else who’s from the outside, like, we were talking earlier and you asked me, like, do you know much about Iot stuff? I was like, I know some. But like, you know, I’m not an expert because I don’t spend that much time in that area. So for somebody who works in IoT, they might be working on something and they’ll be like, this is simple shit, bro. Like, everybody knows this, right? Like, I don’t. So somebody else might not either. So, you know, just put it out there. Upload a YouTube video, write a blog post, make a tweet, whatever it is, whatever.
Whatever floats your boat, whatever medium that you think works best, just share it. Because ultimately that’s all there is. Man, life is short. Yeah. Don’t silo stuff and don’t keep stuff on your hard drive. You know, like musicians always say, you know, don’t keep your music on your hard drive. Like, just release it. Like, put it up on YouTube or put it up wherever, right? Let people listen to it.
And it’s not. Your job is not to decide whether people will like it or not. Your job is just to put it out there anyway. Because where does the information come from anyway? Where does inspiration come from? Where does knowledge come from? Where do we find exploits? Where does the ah, I think this is where this would be how I’m going to solve this problem. Where does that inspiration come from? Who the fuck knows man? But it comes from somewhere. But it certainly didn’t come from side you. So take it, process it and put it back out. It’s my take.
Phillip Wylie: Yeah, I love your comments on the sharing thing because that’s one of the things that we can do at any level beginner to you know someone that’s been in this for a long time is sharing. Just sharing information. Doesn’t matter because I used to, I learned so much from my students when I taught at Dallas College. I taught pen testing. You had people coming in brand new that they were finding new resources that some of us veterans didn’t know about because we’d been in it for a while. We weren’t looking for educational stuff but they learned this stuff and shared it with us all the way. And so that’s one of the things I always like to share with you. People have been doing this for a while.
Don’t underestimate the new folks. They’re finding some really cool stuff.
Dhillon Kannabhiran: Precisely. Like I was like getting into, we’re talking about vibe coding. So I was getting into vibe coding stuff and like all of these new frameworks and all of these new like, you know, I’m so I’m from like C, cobol, C. So like you know, old school PHP is probably the most quote unquote modern language that I’ve last coded in by hand and then manually and then now it’s next JS and it’s whatever the fuck Rails and you know, Redis and all sorts of other shit on top of it and super base and you’re like what the fuck is all this shit man? And like so you know, having to learn something from scratch, it’s like it’s always interesting and so there’s always something new to learn and there’s. I always feel like there’s never, if you find something interesting, it’s somebody else has probably is probably going to encounter the same difficulty that you had as well. You know what I mean? And so if you can help somebody out and even if it seems trivial, you never really know the trickle on effect or you know like pebble in the lake effect or whatever it is. Right, like as in the ripple effect. Right, like so what might happen from you, you just sharing that piece of knowledge and who you might meet and friends you might make.
So yeah, I think the younger generation just needs to Kind of like Tremor. Don’t care less. Care less about what people think. Because honestly, people don’t think about anything, you know, I mean, they don’t think about you as much as you think. You’re not the lead role in their life, man. You’re only the lead role in your own life. So don’t overthink it. Just like, put stuff out there, you know? I mean, I spoke to a bunch of university students in Kazakhstan and they were like, you know, so what do you think we should do next? And I’m like, what do you should do next? I’m like, well, whatever it is that’s interesting to you today, it doesn’t matter how basic it is or whatever it is, but whatever it is that you’re kind of like, man, this is cool.
Like, I’m going to spend the next this weekend reading about it or learning about it. Write a blog post about it or record a video if that’s your medium and you like it. Record a TikTok if you like explaining it. Because you’ll probably end up realizing that you’re actually absorbing the knowledge a lot better by trying to explain it to somebody else. And if you surprise yourself, like, just by reading it, you might find out, oh, yeah, I understand this shit. But when you try to explain it to somebody else and you have to try and recall all of the stuff that you read, you make connections to certain topics or certain areas or certain viewpoints that you might not have stumbled across just by passively reading it. So try that out and see how that works out for you would be my advice to them.
Phillip Wylie: Great advice. It was great chatting with you today. It’s been too long, and hopefully we get to see each other in person again sometime soon. But thanks for. Thanks for joining. And where can people find you?
Dhillon Kannabhiran: Well, you can follow me on Twitter, I’m @leapdog. So L3T, D A W G. Or you can search for my name, which has a very long Last name, on LinkedIn, and you can find me there. But essentially, if you try hard enough, you’ll find me without much trouble.
Phillip Wylie: Well, thanks again.
Dhillon Kannabhiran: Thank you for having me, brother. I hope to see you at Bangkok next year and tell Chris you should come along as well. So go hang out together.
Phillip Wylie: Will do.
Dhillon Kannabhiran: Thanks, man. Take care. Thanks a lot, man.
Phillip Wylie: Thanks for joining us on this episode of the phosphorus IoT security podcast. If you enjoy the podcast, check out Phosphorus IO at Phosphorus IO. You can find more podcast episodes, white papers on IoT security, as well as blog posts and other information to help you secure your OT and Iot infrastructures, Sam.
If you would like to schedule a personalized demo, please use the demo request form; https://phosphorus.io/request-a-demo/
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.