“The challenge is clear: organizations face too many vulnerabilities and not enough clarity on which ones truly matter. CVSS alone doesn’t solve that. KEV and EPSS do, because they highlight what is being exploited now and what is most likely to be exploited next.
That’s why we built them into the Phosphorus Platform. It’s not to check a box—it’s to give CISOs and CIOs a framework to defend decisions and allocate resources with confidence. And it’s to give operators automation so they’re not stuck chasing thousands of low-value alerts. At the end of the day, this is about making remediation measurable, defensible, and operationally efficient at scale.”
– Trevor Tomlinson,
Director of Product Management
The Problem with CVSS-Only Prioritization
- Is this vulnerability being actively exploited?
- How likely is it to be weaponized soon?
- Does this exposure put my operations, compliance, or customers at immediate risk?
Adding Exploit Context to xIoT Risk Management
KEV Enrichment:
- Direct correlation of device vulnerabilities against CISA’s authoritative KEV catalog
- Immediate visibility into vulnerabilities known to be exploited in the wild
- Automated alerts when new entries hit the KEV list
- Federal compliance alignment with CISA BOD 22-01 requirements
EPSS Enrichment:
- Machine learning-driven exploit probability scoring (0–100%)
- Daily updates predicting the likelihood of exploitation within the next 30 days
- Percentile-based benchmarking to compare risk across assets
- Historical analytics to understand exploit trends
Key Capabilities for CISOs, CIOs, and Device Owners
- Automated Intelligence: Real-time KEV correlation and daily EPSS refreshes ensure teams always act on current data.
- Risk Prioritization: A combined framework aligns vulnerability status, exploit likelihood, and compliance needs.
- Operational Integration: Alerting, dashboards, automated ticketing, and RESTful APIs bring context into SIEM/SOAR and ITSM systems.
Business Value: Smarter Remediation, Faster Risk Reduction
Operational Efficiency:
- Reduce noise and focus teams on what truly matters
- Automate compliance reporting and KEV mandate tracking
- Streamline triage with intelligent filtering
Risk Reduction:
- Address vulnerabilities with known exploits before they’re used against you
- Preemptively mitigate high-probability threats
- Strengthen defenses against ransomware and nation-state adversaries
A Smarter Journey from Discovery to Remediation
- Discovery & Assessment– Intelligent Active Discovery provides an accurate device inventory.
- Enrichment– Each vulnerability is contextualized with KEV and EPSS intelligence.
- Prioritization– Security leaders and device owners know which issues pose immediate risk.
- Remediation – Automated fixes: password rotations, firmware updates, and configuration changes, to reduce your exposure with minimal manual effort.
The Future of xIoT Risk Management
CISOs gain defensible prioritization. CIOs and device owners get clear remediation paths. Security teams eliminate wasted cycles.
The result? A safer, more resilient xIoT environment, secured automatically, at scale.
Don’t Just Find It. Fix It.
User Workflow
- Smart Detection: Phosphorus can instantly identify all devices with Known Exploited Vulnerabilities across users’ environments. Users can then automate the remediation of devices with KEVs via smart queries and remediation campaigns.

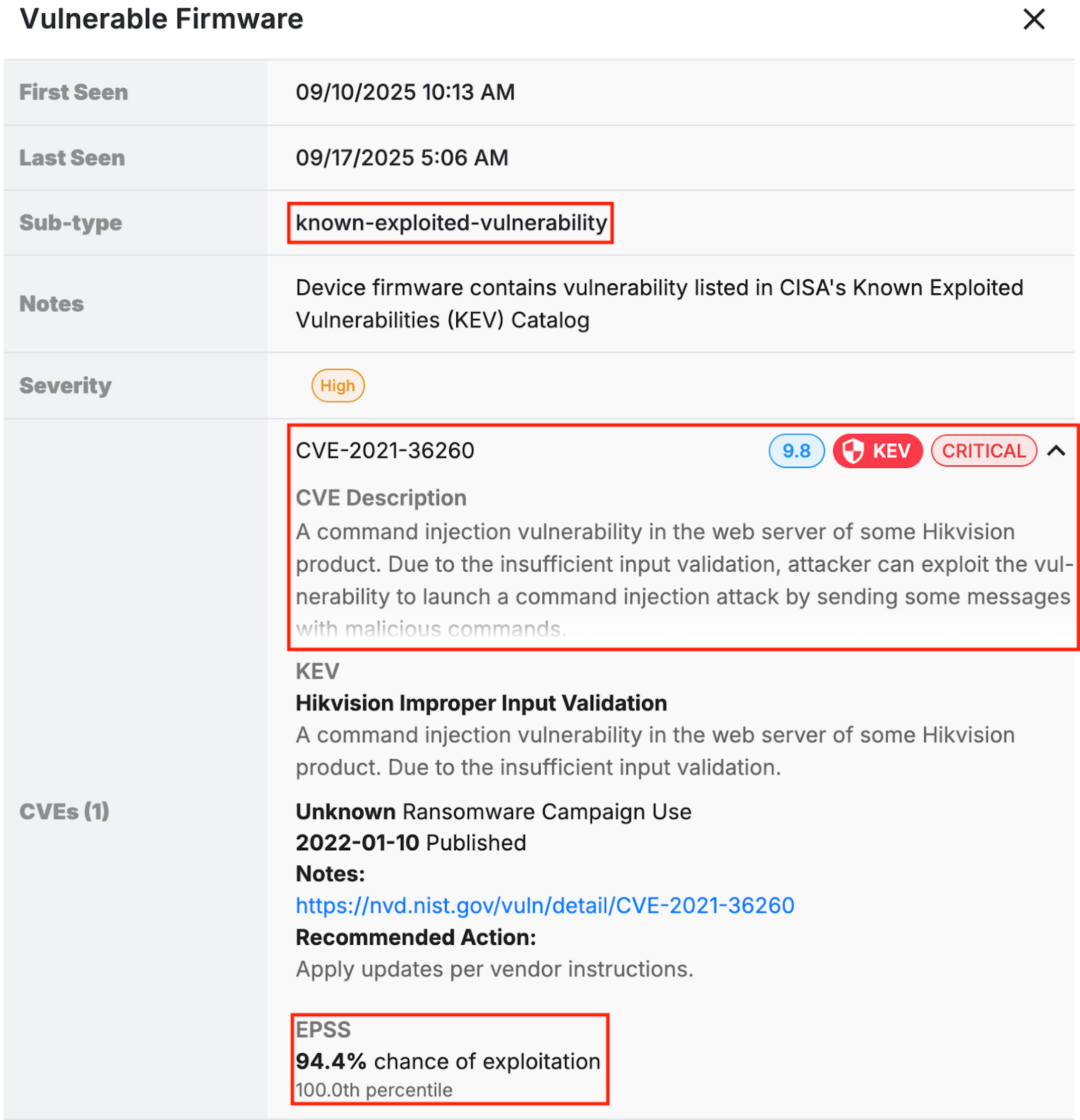
- Automated Remediation: Convert queries tailored to fetching KEVs into Advanced Jobs that automatically remediate vulnerable devices as they’re discovered. These remediation campaigns, configured with smart queries, detect and can automatically patch devices with KEVs during user-defined maintenance windows.
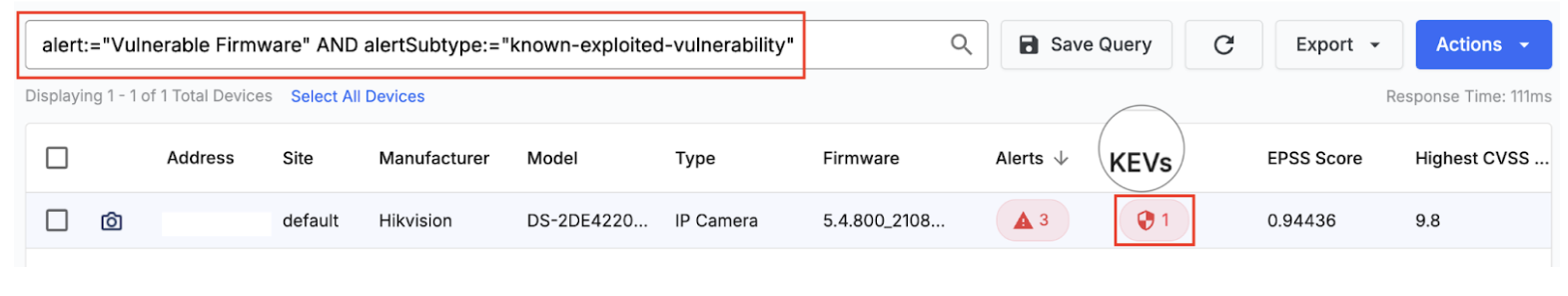
- Continuous Protection: Configure jobs to run on schedules, ensuring new devices with KEVs are automatically detected and queued for remediation without manual intervention.
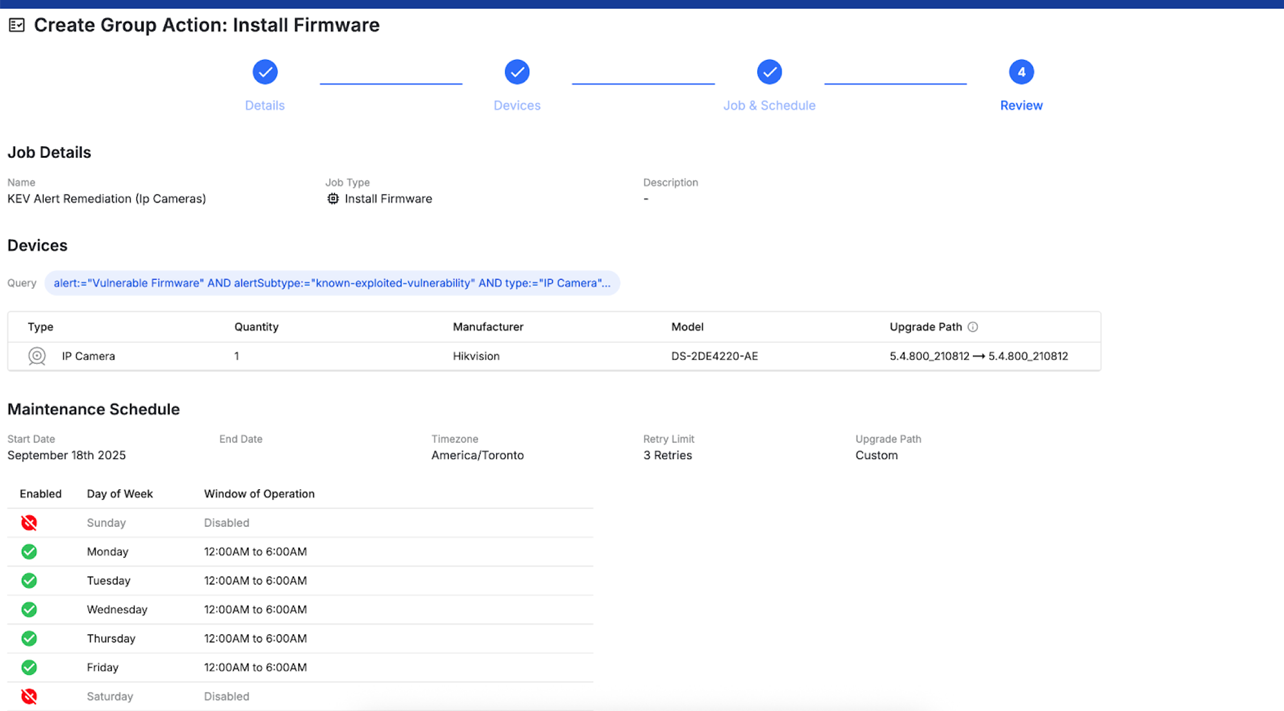
Turning Context into Action
This enhancement delivers operational clarity, regulatory alignment, and measurable risk reduction—all within the same automated workflows customers already rely on. By pairing enriched context with automated remediation, Phosphorus ensures that every vulnerability response is not just prioritized, but acted on at scale.
We invite you to start using this new feature today and share your feedback. Your insights will help us continue refining the platform to make xIoT environments safer, stronger, and more resilient.
Author
Phosphorus Cybersecurity
Phosphorus Cybersecurity® is the leading xTended Security of Things™ platform designed to find, fix, and monitor the rapidly growing and often unmonitored Things of the enterprise xIoT landscape.


