An excerpt from the forthcoming book Practical IoT Hacking: The Definitive Guide to Attacking the Internet of Things.
Provider of security for IoT devices will develop solution for 5G-enabled devices.
Most organizations today unknowingly leave themselves vulnerable to attack. The source of this threat: connected devices. As the number of devices connecting to the network grows, so does the...
In 2016, the makers of the Mirai malware turned their sights on well-known security expert Brian Krebs and his website KrebsonSecurity to flex their muscles. After the attackers published...
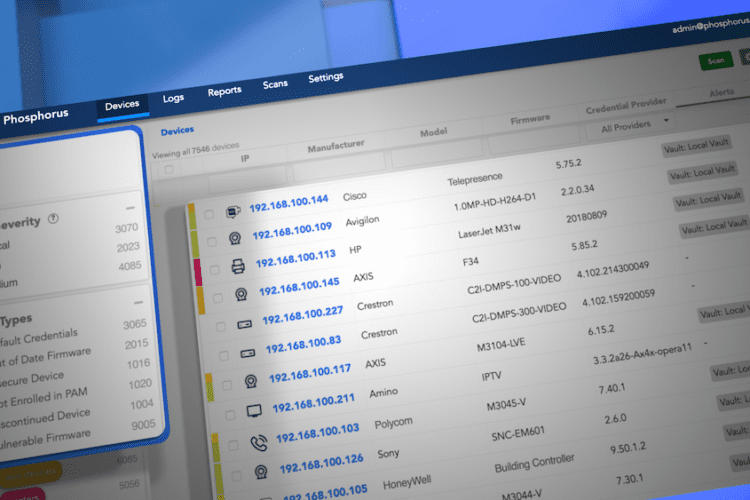
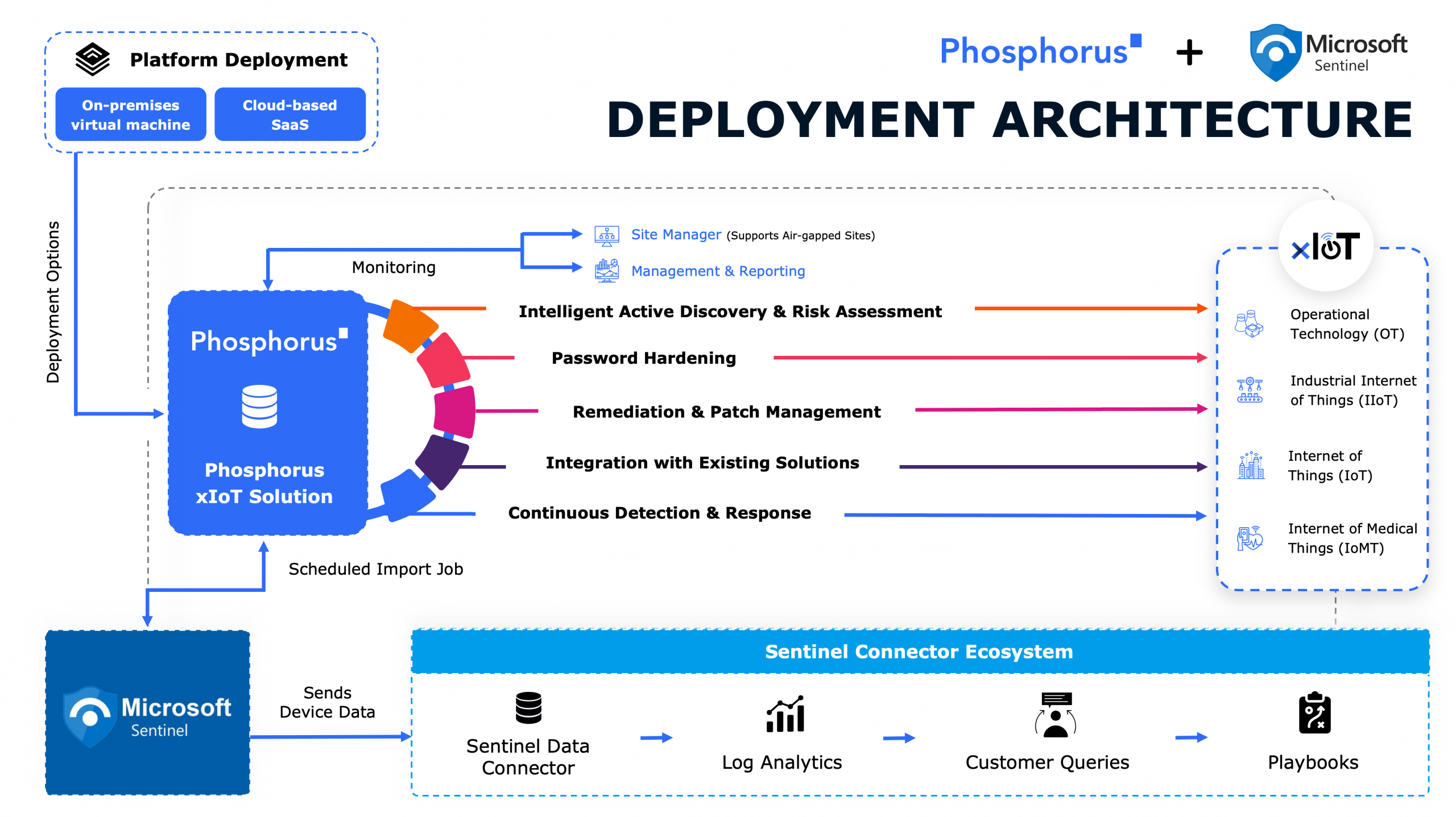
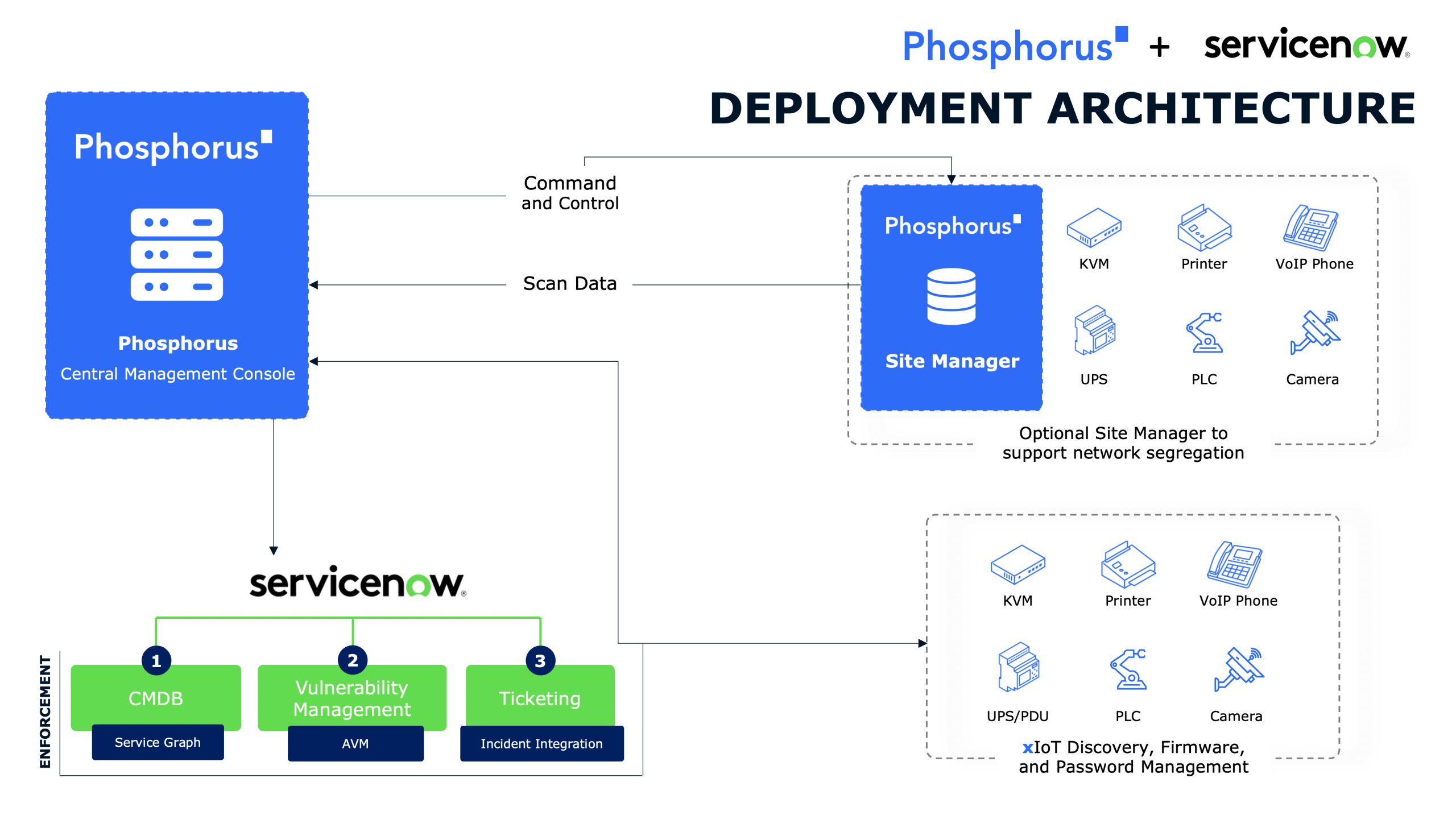
Download the Data Sheet Find Everything. Fix Everything. The Phosphorus Enterprise xIoT Security Platform enables your organization to Find, Fix, and Manage every cyber-physical asset in your enterprise. Designed...
This week, hackers breached Verkada security cameras exposing businesses, police departments, schools, jails and hospitals across the country. The incident, first reported by Bloomberg, allowed the hackers access to...
This week, hackers breached Verkada security cameras exposing businesses, police departments, schools, jails and hospitals across the country. The incident, first reported by Bloomberg, allowed the hackers access to...
Provider of security for IoT devices will develop solution for 5G-enabled devices.
Digital risks escalated in 2020 under the onset of the novel coronavirus and shaped the cybersecurity policy landscape.